Network on Chip (NoC) connectivity is ubiquitous in SoCs, therefore should be an attractive attack vector. Is it possible to prove robustness against a broad and configurable range of threats? Paul Cunningham (Senior VP/GM, Verification at Cadence), Raúl Camposano (Silicon Catalyst, entrepreneur, former Synopsys CTO and… Read More
Blockchain 4.0
The simple and best definition of Blockchain technology is to think about it as electricity , you only see it’s applications but you understand how important it’s and know there are many applications and products that can run on it . But like any other technology it went through stages and evolved as it progressed and matured. We started… Read More
NIST Standardizes PQShield Algorithms for International Post-Quantum Cryptography
News of cyberattacks is routine these days in spite of the security mechanisms built into widely used electronics systems. It is not surprising that entities involved with ensuring safe and secure systems are continually working on enhancing encryption/decryptions mechanisms. Recently NIST standardized cryptography algorithms… Read More
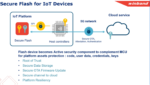
WEBINAR: Flash Memory as a Root of Trust
It should not come as a surprise that the vast majority of IoT devices are insecure. As an indication, one survey estimates that 98% of IoT traffic is unencrypted. It’s not hard to understand why. Many such devices are cost-sensitive, designing security into a product is hard, buyers aren’t prepared to pay a premium for security … Read More
WEBINAR: Taking eFPGA Security to the Next Level
We have written about eFPGA and for six years now and security even longer so it is natural to combine these two very important topics. Last month we covered the partnership between Flex Logix and Intrinsic ID, and the related white paper. Both companies are SemiWiki partners, so we were able to provide more depth and color:
In the … Read More
Protecting Critical IP With Next-Generation Zero Trust Security
While semiconductors are the enablers for high-tech solutions, the semiconductor industry was not at the forefront of Cloud adoption. There were many valid concerns behind the slow adoption, a primary reason being the threat to intellectual property (IP) security. IP in this context refers to not just chip building blocks but… Read More
Post-quantum cryptography steps on the field
In cybersecurity circles, the elephant in the room is a quantum computer in the hands of nefarious actors. A day is coming, soon, when well-funded organizations will be able to rent time on, or maybe even build or buy a quantum machine. Then, if data is valuable enough, people will hunt for it. Two or three months of compute time on a … Read More
CEO Interview: Jaushin Lee of Zentera Systems, Inc.
Dr. Jaushin Lee is the founder and CEO of Zentera Systems. He is the visionary architect behind the award-winning Zentera CoIP (Cloud over IP) platform that enables enterprises to dramatically accelerate their journey to Zero Trust security. Jaushin brings 20 years of management and executive experience in networking and computer… Read More
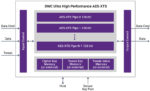
Memory Security Relies on Ultra High-Performance AES-XTS Encryption/Decryption
A recent SemiWiki post covered the topic of protecting high-speed interfaces in data centers using security IP. That post was based on a presentation made by Dana Neustadter at IP-Soc Silicon Valley 2022 conference. Dana’s talk was an overview of various interfaces and Synopsys’ security IP for protecting those interfaces. … Read More
Cybersecurity Threat Detection and Mitigation
Every week in the technology trade press I am reading about cybersecurity attacks against web sites, apps, IoT devices, vehicles and even ICs. At the recent IP SoC Silicon Valley 2022 event in April I watched a cybersecurity presentation from Robert Rand, Solution Architect for Tessent Embedded Analytics at Siemens EDA. Common… Read More








Real men have fabs!