While semiconductors are the enablers for high-tech solutions, the semiconductor industry was not at the forefront of Cloud adoption. There were many valid concerns behind the slow adoption, a primary reason being the threat to intellectual property (IP) security. IP in this context refers to not just chip building blocks but rather everything including tools, design methodologies and operational processes. Naturally, cloud providers took the IP security concern seriously and developed strong security mechanisms. They invested heavily into developing a secure infrastructure with tight security protocols and procedures for data at rest and data in motion.
With this increased level of cloud security, the chip industry started migrating to cloud computing. But accessing corporate data was still via on-prem equipment or via company supplied laptop computers and other mobile devices. The company’s IT department typically installed security software to protect against viruses and malware. As many other industries started accommodating bring your own devices (BYOD) policies with their employees, semiconductor industry was still lagging on this front.
Evolving Workplace
The semiconductor work environment has changed a lot over the recent years. Data and tools are nowadays accessible using both personal and company supplied devices. Access is made from within the firewall as well as from outside. When the Covid-19 pandemic hit, businesses were pushed into a work from home (WFH) model with predominant data access from outside the firewall. Of course, the primary mode for remote accessing data and tools was via a virtual private network (VPN).
VPNs are insecure because once hacked into, hackers can potentially access the entire network. Once an attacker has breached the network through a compromised device, hackers can try to steal corporate IP, customer or financial information, or launch a ransomware attack.
Security Challenges
In spite of elaborate security measures put in place, corporate networks are still hacked into on a regular basis. The usual hacks are made possible through a combination of phishing and breaking into a VPN client. With employees, contractors, vendors, supply-chain partners and customers needing different levels of access to various data, the threat of break-in is ever present.
Just last week, Cisco announced that their corporate network was hacked into.
Following is an excerpt from a blog post by Cisco Talos Intelligence Group, one of the largest commercial threat intelligence teams in the world.
- The attacker conducted a series of sophisticated voice phishing attacks under the guise of various trusted organizations attempting to convince the victim to accept multi-factor authentication (MFA) push notifications initiated by the attacker. The attacker ultimately succeeded in achieving an MFA push acceptance, granting them access to VPN in the context of the targeted user.
- Initial access to the Cisco VPN was achieved via the successful compromise of a Cisco employee’s personal Google account.
Following is an excerpt from SecurityWeek.com as it relates to the above Cisco news.
- The attacker managed to enroll new devices for MFA and authenticated to the Cisco VPN. Once that was achieved, they started dropping remote access and post-exploitation tools. The hackers escalated their privileges, created backdoors for persistence, and moved to other systems in the environment, including Citrix servers and domain controllers.
Security risks are only growing over time, prompting companies to favor a Zero Trust security model over a VPN-based model. As per a report on helpnetsecurity.com, attacks against VPNs were up nearly 2,000% in 2021. According to a VPN Risk Report based on Zscaler’s survey of over 350 cybersecurity professionals:
- 72% of organizations are concerned that VPN may jeopardize IT’s ability to keep their environments secure
- 67% of enterprises are considering remote access alternative to a traditional VPN
- 72% of companies are prioritizing the adoption of a Zero Trust model
Zero Trust Security (ZTS)
Even before Covid-19 impacted the workplace forever, ZTS was already in motion as a solution for addressing security threats. The ZTS model takes the approach of verifying everyone and every device that is seeking access to confirm they are who they claim to be. It does not matter whether the access is being sought from within the network or from outside.
Fundamental Requirements for Enterprise ZTS
- Access visibility – Full visibility of all access to critical applications and data
- Access control – Authenticate and control of who can access what resources, applications, and data
- Protocol control – Whitelisted software and protocol controls to block unapproved or malicious traffic
- Universal enforcement – Unified method across enterprise on-prem, in the cloud, or remote
- Business agility – Dynamic project-based controls, no infrastructure “rip and replace”
A primary challenge of Zero Trust approach is ensuring security without slowing things down. Access to sensitive data is needed on an ongoing basis to communicate and collaborate on projects. Team members’ roles and access levels vary and change on a frequent basis. ZTS implementation should be such that people don’t lose access, leading to productivity loss.
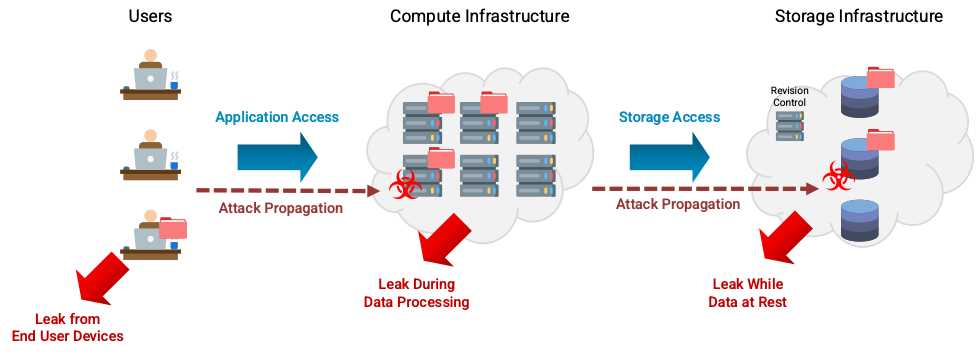
The Figure below highlights where data leaks typically happen and how attacks propagate through a network.
Zentera CoIP® Platform and Technology
Zentera has developed the next generation ZTS solution using its patented technology. Its solution takes a differentiated approach of in-line ZTS. The Zentera CoIP Platform implements a Zero Trust security fabric using an overlay technology architecture. The platform authenticates users using a company’s existing identity providers and endpoints and applications using certificates and fingerprints. This method enables a role-based access to specific applications and resources. Accordingly, secure virtual zones can be created, managed and torn down rapidly as the requirements call for. Refer to the Figure below for the solution concept.
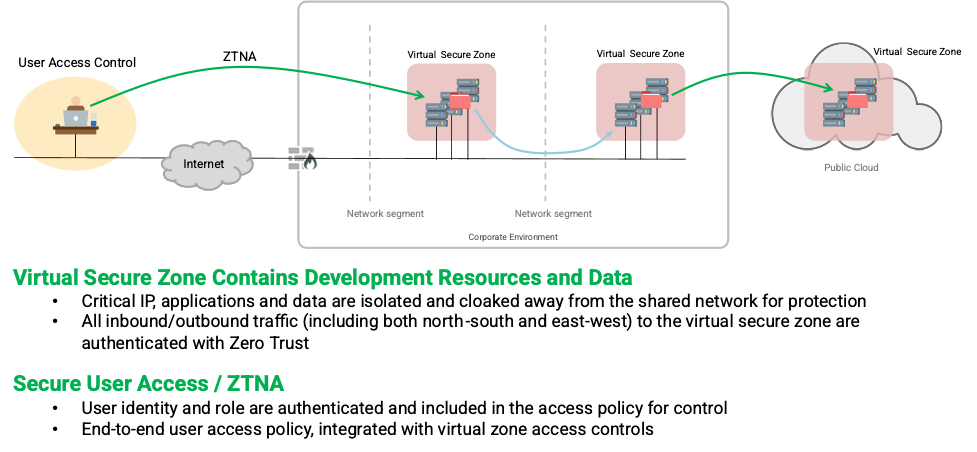
The CoIP platform integrates the following three core engines to implement ZTS.
The CoIP Chamber
The chamber implements the concept of a secure virtual development environment wherein applications are cloaked and lateral network access is eliminated. Inbound and outbound flow control are allowed only for authorized users, apps and services.
The CoIP Network
The CoIP network connects applications rather than connect networks across silos. The applications’ connectivity is based on application identity. IP collisions across environments are avoided through the use of overlay IP addressing.
CoIP Access
This engine authorizes each access based on an user’s role and privileges. The users and devices are authenticated through MFA. This engine also sets up non-step and one-stop access between specific applications instead of connecting entire networks together.
CoIP Technology in Action
Whether it is the employee, contractor, vendor or customer, they gain access to the remote desktop chamber via the CoIP platform. From there, they gain access to the application chamber and other applications based on CoIP access controls setup. Even if someone wants access from an on-prem workstation, they still have to go through the remote desktop chamber before they can access applications and data. Refer to the Figure below.
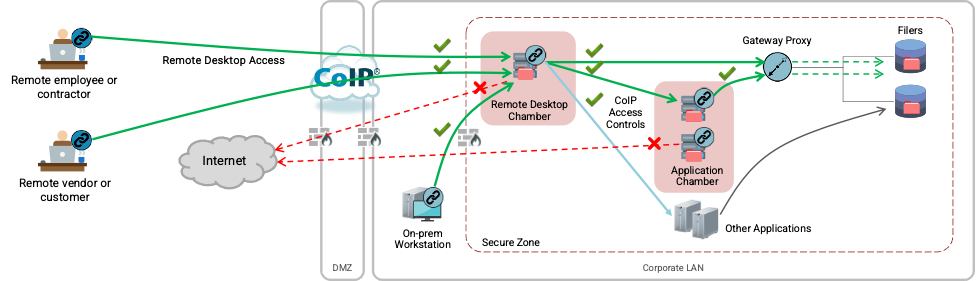
In the particular use-case shown in the above Figure, blanket access to the internet has been prohibited. For use-cases where internet access is required for specific purposes, the technology supports those requirements. For example, let’s say that access to a company’s remote data server is required, that specific connectivity can be authenticated and setup.
Also Read:
Post-quantum cryptography steps on the field
CEO Interview: Jaushin Lee of Zentera Systems, Inc.
Memory Security Relies on Ultra High-Performance AES-XTS Encryption/Decryption
Share this post via:





Flynn Was Right: How a 2003 Warning Foretold Today’s Architectural Pivot