You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
WP_Term Object
(
[term_id] => 140
[name] => Breker Verification Systems
[slug] => breker-verification-systems
[term_group] => 0
[term_taxonomy_id] => 140
[taxonomy] => category
[description] =>
[parent] => 157
[count] => 22
[filter] => raw
[cat_ID] => 140
[category_count] => 22
[category_description] =>
[cat_name] => Breker Verification Systems
[category_nicename] => breker-verification-systems
[category_parent] => 157
[is_post] =>
)
WP_Term Object
(
[term_id] => 140
[name] => Breker Verification Systems
[slug] => breker-verification-systems
[term_group] => 0
[term_taxonomy_id] => 140
[taxonomy] => category
[description] =>
[parent] => 157
[count] => 22
[filter] => raw
[cat_ID] => 140
[category_count] => 22
[category_description] =>
[cat_name] => Breker Verification Systems
[category_nicename] => breker-verification-systems
[category_parent] => 157
[is_post] =>
)
Breker Verification Systems Plans Demonstrations of its Complete Synthesis and SystemVIP Library and Solutions Portfolio
Attendees who step into the Breker Verification Systems booth during DAC (Booth #2520—second floor) will see demonstrations of its Trek Test Suite Synthesis and SystemVIP libraries and solutions portfolio.… Read More
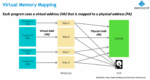
In the early days of RISC-V adoption, applications were microcontroller-centric with no need for virtualization support. But horizons expanded and now RISC-V is appearing in application processors, very much needing to be able to virtualize multiple apps concurrently. Take another step forward to datacenter servers running… Read More
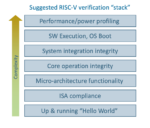
RISC-V cores are popping up everywhere. The growth of this open instruction set architecture (ISA) was quite evident at the recent RISC-V summit. You can check out some of the RISC-V buzz on SemiWiki here. While all this is quite exciting and encouraging, there are hurdles to face before true prime-time, ubiquitous application… Read More
Dan is joined by Dave Kelf, CEO of Breker Verification Systems, whose product portfolio solves challenges across the functional verification process for large, complex semiconductors. Dave has deep experience with semiconductor design and verification with management and executive level positions at Cadence, Synopsys,… Read More
RISC-V is clearly gaining momentum across many applications. That was quite clear at #61DAC as well. Breker Verification Systems solves challenges across the functional verification process for large, complex semiconductors. Its Trek family of products is production-proven at many leading semiconductor companies worldwide.… Read More
In the formal world the core technology is extremely powerful, and specialist users need full access to tackle difficult problems. But for many applications, teams prefer canned solutions built on the core technology yet scalable to non-experts. A similar dynamic appears to be playing out between System VIPs and PSS. PSS, the… Read More
Breker Verification Systems will demonstrate its new RISC-V CoreAssurance™ and SoCReady™ SystemVIP™ along with its Trek Test Suite Synthesis portfolio during the 61st Design Automation Conference (DAC) in Booth #2447. DAC will be held from Monday, June 24, through Wednesday, June 26, from 10 a.m. until 6 p.m. at Moscone West… Read More
I had grown comfortable thinking about RISC-V as a cost-saving and more flexible alternative to Intel/AMD or Arm in embedded applications. Where clearly it is already doing very well. But following a discussion with Dave Kelf and Adnan Hamid of Breker, RISC-V goals have become much more ambitious, chasing the same big system applications… Read More
Maheen Hamid, a member of the ESD Alliance (a SEMI Technology Community) Governing Council and a member of SEMI’s North America Advisory Board, is an astute business executive. Together with her husband Adnan Hamid, they founded Breker Verification Systems, a company developing test synthesis solutions. She serves today … Read More
The RISC-V open ISA premise was clearly a good bet. It’s taking off everywhere, however verification is still a challenge. As an alternative to Arm, the architecture and functionality from multiple IP providers looks very competitive, but how do RISC-V providers and users ensure the same level of confidence we have in Arm? Arm … Read More