Every week in the technology trade press I am reading about cybersecurity attacks against web sites, apps, IoT devices, vehicles and even ICs. At the recent IP SoC Silicon Valley 2022 event in April I watched a cybersecurity presentation from Robert Rand, Solution Architect for Tessent Embedded Analytics at Siemens EDA. Common jargon in cybersecurity discussions are terms like: vulnerability, threat, attack, risk, asset and attack surface.
Regulated industries with safety-critical usage like automotive, aerospace and medical all have a keen awareness of cybersecurity threats, so there’s a culture of detection and mitigation. There’s even a national vulnerability database maintained by NIST (National Institute of Standards and Technology), and they show a growing trend of vulnerabilities over time.
Embedded Analytics
Having hardware security allows an electronic system to detect a threat quickly, understand it, then act by responding, which avoids a dangerous outcome and places the system into a safe mode, keeping everyone safer. The specific technology that Siemens EDA brings to cybersecurity is something called Embedded Analytics, extra hardware that gives developers and operators of embedded systems the visibility needed to see what’s happening inside their SoC, and the ability to quickly respond to a cyber threat. This added analytics IP inside your SoC subsystem connects to all of the IP, giving it system-level visibility:
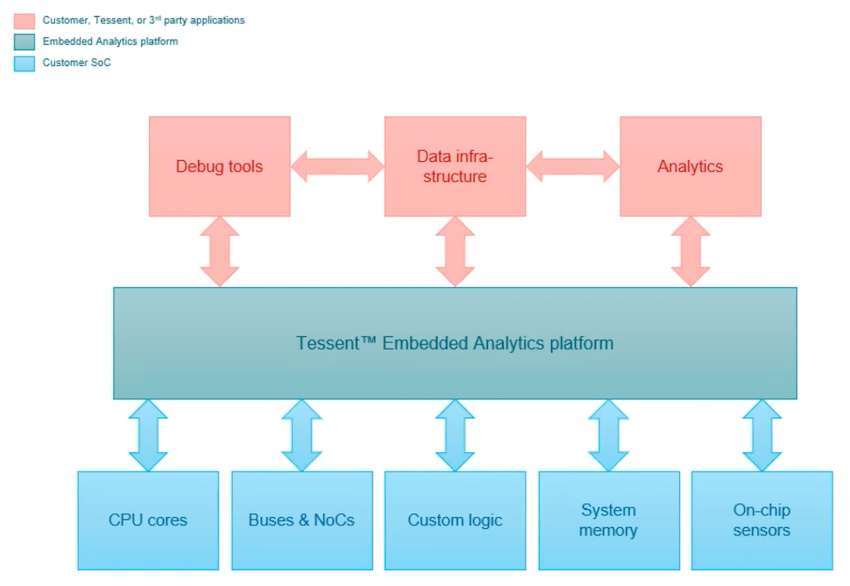
This added IP is customized for your specific SoC, and the data it analyzes can be communicated with existing IO (USB 2, USB 3, JTAG, Aurora Serdes, PCIexpress, Ethernet). There’s an Eclipse-based IDE tool to allow SW/HW debug capabilities of the complete system, or you can even use a Python API to get the visibility and control desired.
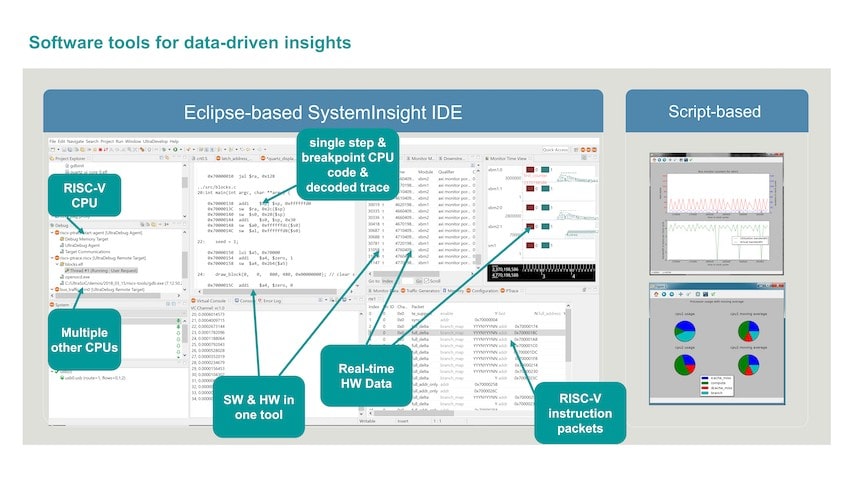
Adding embedded analytics does give your SoC team detailed insight in how their subsystem is being used in realtime, provides visibility of the whole system from boot, allows monitoring of interconnect at a transaction level, lets you control and trace each processor. All of the common ISAs and interconnect protocols are supported, so you’re not waisting any time. You get to decide which subsystems are connected to the embedded analytics.
Sentry IP
To detect and respond to cybersecurity threats in just a few clock periods there’s the Sentry IP, and this hardware block is placed as a bus manager interface. This Sentry IP filters all transactions and only passes through safe transactions, blocks illegal transactions and can redirect when an attack is detected.
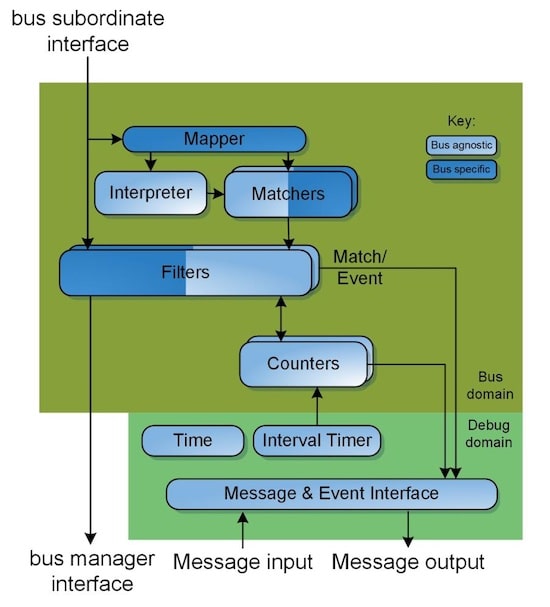
There are 1,024 possible matches to identify vulnerabilities, so this system can adapt to new threats as they emerge.
Embedded Security Subsystem
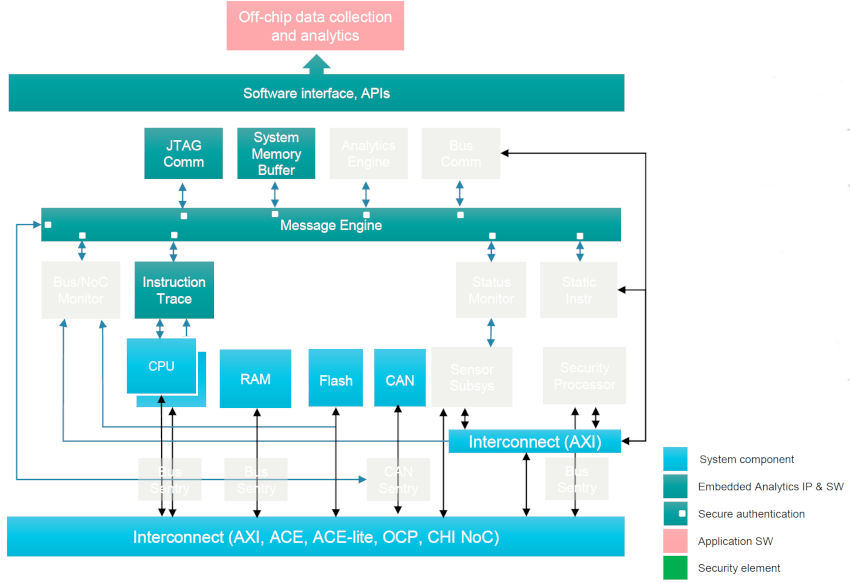
Robert shared an example system that had several CPUs, RAM, Flash, CAN and interconnect components shown in light blue:
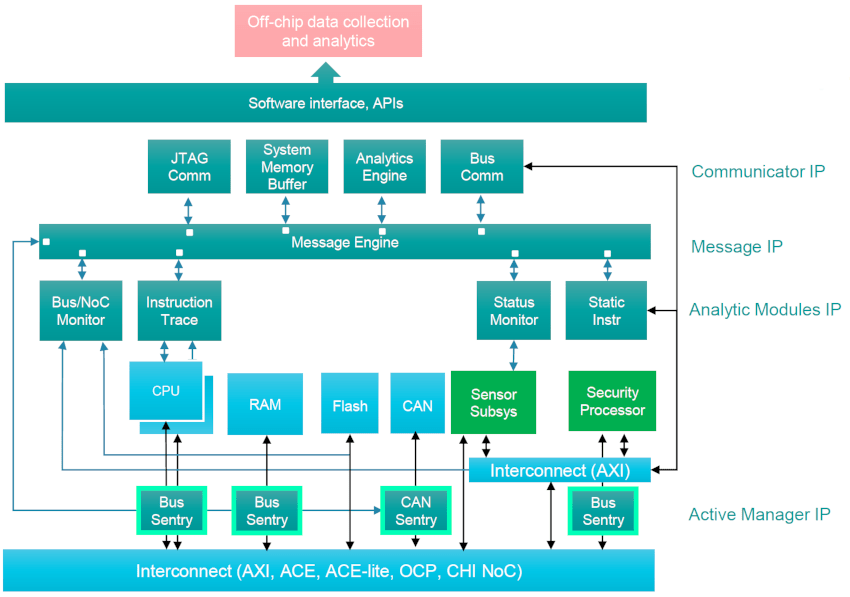
The embedded analytics IP modules are shown in teal color, and the Bus Sentry blocks are outlined in bright green. The subsystem can be run in either an application domain, or the security domain. The sentry blocks enforce your specific filters for each IP block connected. When your subsystem is run in the application domain you have complete visibility of what’s going on, provided by embedded analytics:
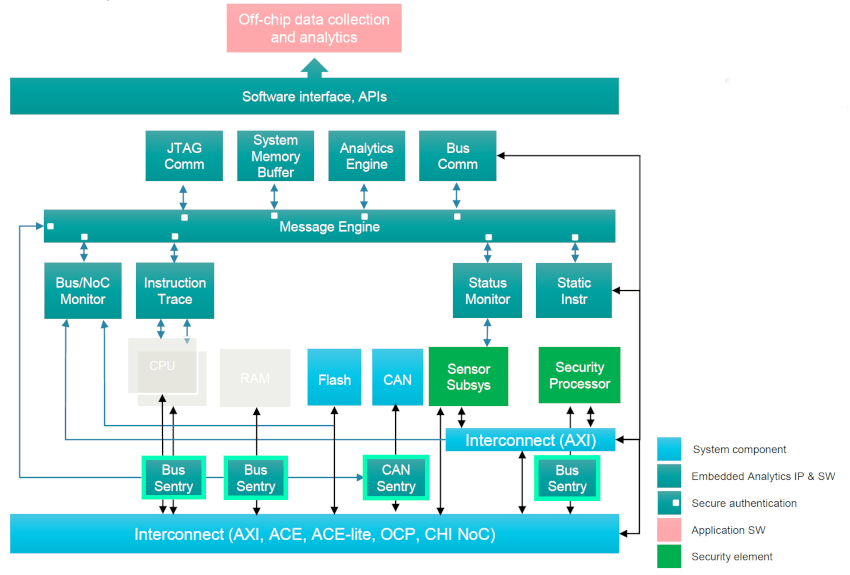
In the security domain all of the bus sentries are activated, providing hardware-level threat detection and mitigation:
Summary
Cybersecurity threats are a growing concern for companies providing electronic systems, but there’s some good news as the approach of adding Embedded Analytics hardware to detect, filter and mitigate threats is now possible. With Siemens EDA the Tessent Embedded Analytics approach provides analytic tools for building signatures of normal operation, so that signatures of threats can be quickly detected. Monitors can continuously collect fine-grained data to detect new threats, and enable your security team to develop mitigation.
The Bus Sentry IP blocks allow your chip to mitigate any threats at the hardware level. Over time you can always add new filters and mappers to provide improved security hardening. On-chip monitors and sentries provide new promise against cybersecurity attacks.
There’s also a 19 minute YouTube video of this presentation.
Related Blogs
- Embedded Analytics Becoming Essential
- Optimize AI Chips with Embedded Analytics
- Tessent Streaming Scan Network Brings Hierarchical Scan Test into the Modern Age
- Tessent Safety – Entering the Safety Ecosystem: A reference flow for automotive IC test






Comments
There are no comments yet.
You must register or log in to view/post comments.