It should not come as a surprise that the vast majority of IoT devices are insecure. As an indication, one survey estimates that 98% of IoT traffic is unencrypted. It’s not hard to understand why. Many such devices are cost-sensitive, designing security into a product is hard, buyers aren’t prepared to pay a premium for security and there haven’t been any meaningful barriers to insecure products.
Overcoming our human inability to understand low percentage risks isn’t going to happen so the burden falls on regulations. Which are now starting to develop teeth. The EU will require security certificates for all connected devices by 2023. In the US, NIST is working on cybersecurity regulations which are thought will appear in a year or two and will carry penalties for non-compliance. Automotive markets will self-police security by expecting ISO 21434 documentation on processes and risk. Still, many product builders will try to dodge the problem unless solutions are easy. Winbond has an intriguing approach with their secure flash.
Roots of Trust (RoT)
This concept is familiar to anyone with a moderate understanding of security. A root of trust in a system is a core component the system can always trust for security purposes – authentication, cryptography and so on. The goal is to minimize the attack surface around essential security functions, rather than distributing these across the system. All other services must turn to the RoT when making a security-related request. A hardware-based RoT is essential in such implementations.
The standard approach to an RoT is processor-centric – Apple T2 and Google Titan chips are a couple of examples. Such chips use on-board flash memory, for support but with limited size. This is necessary to keep cost down and because the combination of embedded flash and processor logic on a single chip limits memory size. That limitation is a problem for IoT applications which need to support complex stacks for NB-IoT and other advanced communications protocols. There are workarounds outside the RoT but those again increase the attack surface.
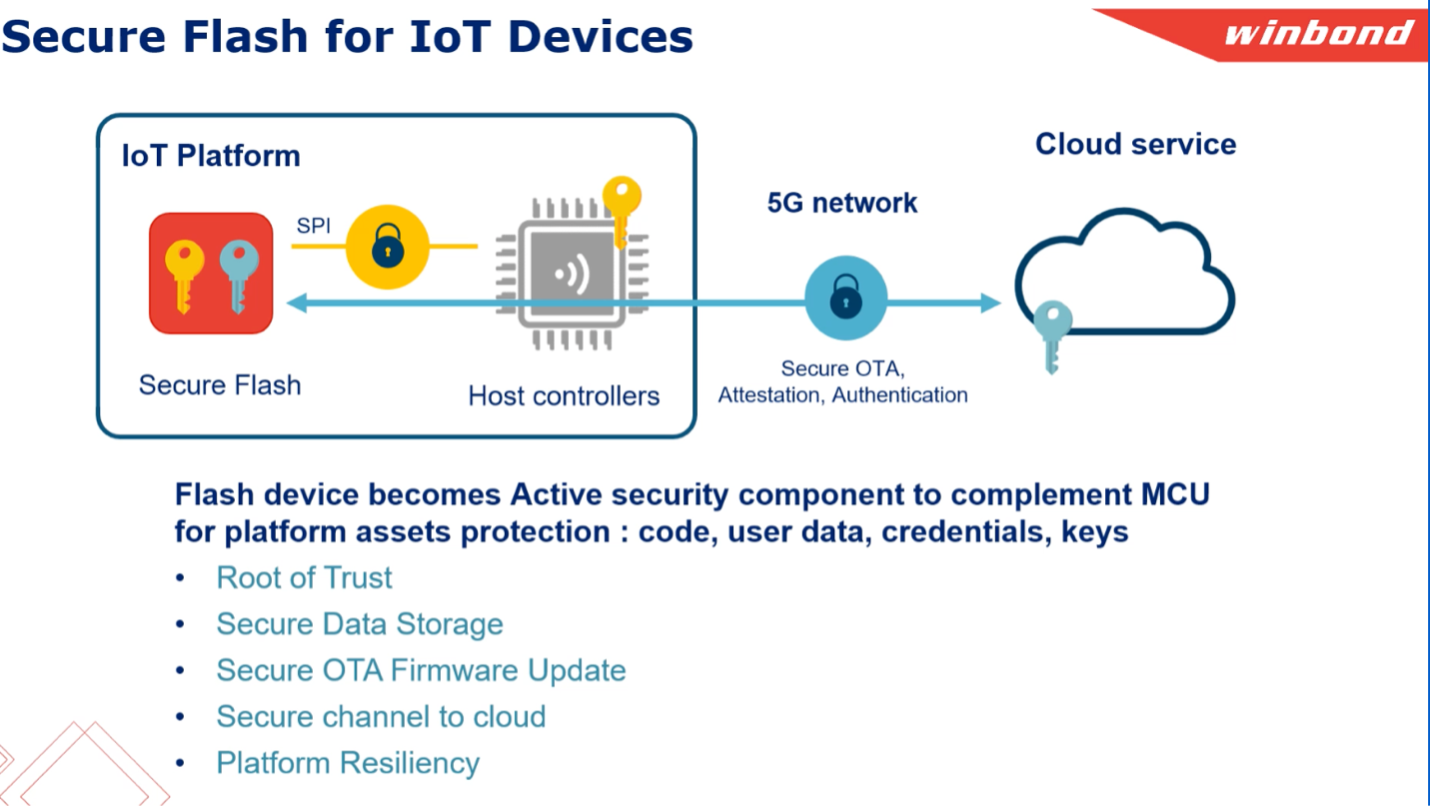
Winbond has an intriguing approach in which the make the flash memory a complement to an MCU root of trust, allowing for much more spacious storage. This is an active security component, not just a larger memory.
The Winbond W77Q secure flash memory
The W77Q is a smart flash memory with an emphasis on security. A single use key must sign write and erase commands. The device verifies boot code integrity on reset and allows for secure boot (XIP) directly from flash. Without need to first upload to DRAM. It supports fallback allowing boot from an alternative code space if an integrity problem is detected. It protects against rollback attacks where a hacker attempts to install a correctly signed older version of code with known bugs.
W77Q handles over the air updates directly, without need for MCU support. A remote trusted authority can force a clean boot using an authenticated watchdog timer. And it supports secure storage in separately protected partitions in the same device.
Pretty neat for a serial NOR flash pin-compatible with a conventional device, yet certified secure to a number of relevant standards. You can watch a detailed webinar HERE.
Also Read:
WEBINAR: Taking eFPGA Security to the Next Level
WEBINAR: How to Accelerate Ansys RedHawk-SC in the Cloud
Webinar: Semifore Offers Three Perspectives on System Design Challenges
Share this post via:






Flynn Was Right: How a 2003 Warning Foretold Today’s Architectural Pivot