Secure-IC is a global leader in end-to-end cybersecurity solutions, specializing in the domain of embedded systems and connected devices. With an unwavering commitment to pushing the boundaries of security innovation, Secure-IC has established a remarkable track record. Its credentials include active involvement in new… Read More
Tag: root of trust
Cyber-Physical Security from Chip to Cloud with Post-Quantum Cryptography
In our interconnected world, systems ranging from smart cities and autonomous vehicles to industrial control systems and healthcare devices have become everyday components of our lives. This fusion of physical and digital systems has led to a term called cyber-physical system (CPS). Ubiquitous connectivity is exposing the… Read More
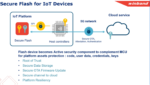
WEBINAR: Flash Memory as a Root of Trust
It should not come as a surprise that the vast majority of IoT devices are insecure. As an indication, one survey estimates that 98% of IoT traffic is unencrypted. It’s not hard to understand why. Many such devices are cost-sensitive, designing security into a product is hard, buyers aren’t prepared to pay a premium for security … Read More
Enlisting Entropy to Generate Secure SoC Root Keys
Most methods of securing SOCs involve storing a root key that provides the basis of all derived keys and encryption of communication. The weakness with these methods is that even if the root key is stored in secure non-volatile memory, there are often methods to read the key. Once a key has been divulged the device can be cloned and … Read More
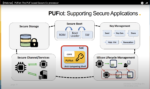
Securing Applications: A PUFiot Solution for RISC-V-based IoT Devices
In June 2021, eMemory Technology hosted a webinar titled “PUFiot: A PUFrt-based Secure Coprocessor.” You can read a blog leading up to that webinar here. PUFiot is a novel high-security crypto coprocessor. You can access a recording of that entire webinar from eMemory’s Resources page. While the focus of that webinar was to present… Read More
Digging Deeper in Hardware/Software Security
When it comes to security we’re all outraged at the manifest incompetence of whoever was most recently hacked, leaking personal account details for tens of millions of clients and everyone firmly believes that “they” ought to do better. Yet as a society there’s little evidence beyond our clickbait Pavlovian responses that we’re… Read More
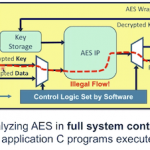
SOC security is not a job for general purpose CPUs
Life is full of convenience-security tradeoffs. Sometimes these are explicit, where you get to make an active choice about how secure or insecure you want things to be. Other times we are unaware of the choices we are making, and how risky they are for the convenience provided. If you leave your bike unlocked, you can expect it to be… Read More
Drop-In Security for IoT Edge Devices
You’re excited about the business potential for your cool new baby monitor, geo-fenced kid’s watch, home security system or whatever breakthrough app you want to build. You want to focus on the capabilities of the system, connecting it to the cloud and your marketing rollout plan. Then someone asks whether your system is architected… Read More
HDCP 2.2, Root of Trust, Industry’s First SHA-3 Security IP from Synopsys
Did you know that by 2020 90% of cars will be connected to Internet? Great, but today, there are already more than 100 car models affected with security flaws (Source: theguardian.com, 2015). That 320 apps are installed on average smartphone device? It would be a complete success, but 43% of Android devices allow installation of… Read More
Security All Around in SoCs at DAC
Last month I was on my way to write a detailed article on important aspects to look at while designing an SoC. This was important in the new context of modern SoCs that go much beyond the traditional power, performance and area (PPA) requirements. I had about 12-13 parameters in my list that I couldn’t cover in one go, so I put the write-up… Read More