You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
WP_Term Object
(
[term_id] => 97
[name] => Security
[slug] => security
[term_group] => 0
[term_taxonomy_id] => 97
[taxonomy] => category
[description] =>
[parent] => 0
[count] => 315
[filter] => raw
[cat_ID] => 97
[category_count] => 315
[category_description] =>
[cat_name] => Security
[category_nicename] => security
[category_parent] => 0
[is_post] =>
)
Dan is joined by Michele Sartori – senior product manager at PQShield. Michele is a software engineer in Computer and Network Security, specializing in product management. He is a passionate tech team leader at the forefront of emerging technologies focused on achieving tangible results.
In this highly informative discussion,… Read More
Dr. Andreas Kuehlmann, Executive Chairman and CEO at Cycuity, has spent his career across the fields of semiconductor design, software development, and cybersecurity. Prior to joining Cycuity, he helped build a market-leading software security business as head of engineering at Coverity and, after its acquisition by Synopsys,… Read More
Tell us a little bit about yourself and your company.
The PQShield team helped define the new PQC (post-quantum cryptography) standards that will be used to replace current encryption that is vulnerable to attack by quantum computers. Now, we work with international blue-chip organizations, disruptive scale-ups, and national… Read More
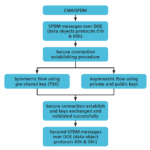
In today’s digital landscape, data security has become an indispensable feature for any data transfer protocol, including Peripheral Component Interconnect Express (PCIe). With the rising frequency and sophistication of digital attacks, ensuring data integrity, confidentiality, and authenticity during PCIe transport… Read More
A crucial step in helping any new technology specification gain adoption is certification. NIST has been hard at work establishing more than post-quantum cryptography algorithms – they’ve also integrated the new algorithms into their process for third-party validation testing to ensure implementations are as advertised.… Read More
Post-Quantum Cryptography, or PQC provides a technical approach to protect encrypted data and connections when quantum computers can cost-effectively defeat current approaches. Exactly when this will occur is open to much discussion, but the fact is this day is coming, some say in ten years. One of the imperatives is to deploy… Read More
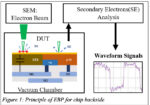
In the quest to secure the authenticity and ownership of advanced integrated circuit (IC) packages, a novel approach has been introduced in this paper that capitalizes on the inherent physical discrepancies within these components. This method, distinct from traditional strategies like physical unclonable functions (PUFs)… Read More
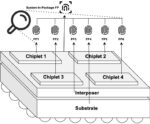
The outsourcing fabrication of ICs makes them vulnerable to hardware security threats. Security threats such as reverse engineering, insertion of hardware Trojan, and backside contact-less probing to steal cryptographic information can cause financial loss to IP owners and security risk to the system in which these ICs are… Read More
Many of you are already familiar with Silicon Catalyst and the value it brings to semiconductor startups, the industry and the electronics industry at large. Silicon Catalyst is an organization that supports early-stage semiconductor startups with an ecosystem that provides tools and resources needed to design, create, and… Read More
Quantum computing promises to deliver vast increases in processing power. The technology exploits the properties of quantum mechanics to create revolutionary increases in performance. Medical and material science research are examples of fields that will see dramatic improvement when production-worthy quantum computers… Read More






Facing the Quantum Nature of EUV Lithography