You might think that one special advantage of AI systems is that they should be immune to attacks. After all, their methods are so complex and/or opaque that even we can’t understand how they work, so what hope would a hacker have in challenging these systems? But you would be mistaken. There’s nothing hackers like better than a challenge.… Read More
Author: Bernard Murphy
The Other Half of AI
I touched earlier on challenges that can appear in AI systems which operate as black-boxes, particularly in deep learning systems. Problems are limited when applied to simple recognition tasks, e.g. recognizing a speed limit posted on a sign. In these cases, the recognition task is (from a human viewpoint) simply choosing from… Read More
Renewable Energy is On a Roll
Since everything we build in this industry either runs on, stores or produces electricity, we should have a more than passing interest in how we get that power. A couple of organizations, confusingly named the IEA (International Energy Agency) and the EIA (Energy Information Administration – a US agency) provide lots of interesting… Read More
Building a Virtual Prototype
I wrote recently about how virtual prototypes (in the form of VDKs) can help embedded software teams practice continuous integration. Synopsys has just released a white paper detailing a practical approach to building a VDK, using the Juno ARM development platform (ADP) to illustrate. Just as a reminder, the point of a virtual… Read More
Enter the Cellular IoT
You could be forgiven for thinking that wireless in an IoT device must be Bluetooth-5 or Zigbee or Thread. After all, that’s what ARM has introduced as a part of their IoT solution and they have market weight that is difficult to dismiss. However those options aren’t the only game in town. There is already some level of (second… Read More
An End of Year View of Semi Consolidation
The last couple of years have been tumultuous for the semiconductor market. IC Insights just released a report showing just how much consolidation has concentrated market strength in a small number of companies. The report (which excludes fabs) shows that the 5 top companies – Intel, Samsung, Qualcomm, Broadcom and SK Hynix – … Read More
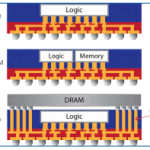
Design for Fanout Packaging
In constant pursuit of improved performance, power and cost, chip and system designers always want to integrate more functions together because this minimizes inter-device loads (affecting performance and power) and bill of materials on the board (affecting cost). However it generally isn’t possible to integrate … Read More
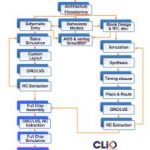
Managing International Design Collaboration
Customer perspectives on a tool are always interesting, as much for why they felt the need for the tool as how it is working out for them in practice. Active-Semi, an emerging leader in power management and digital motor drive ICs gave a presentation at CDNLive describing why they adopted ClioSoft tools for design collaboration … Read More
Design for Ultra-Low Power LTE: CEVA Webinar
You might have thought that ultra-low power communication for the IoT was limited to standards like BT5 and 802.15.4 (eg in ZigBee and Thread) which depend on gateways to cellular networks and limit reach, especially deep inside buildings. But now there’s a new standard for ultra-low power and ultra-low cost based on LTE, known… Read More
Hack This? Making Software a Moving Target
It sometimes seems that the black hats are always one step ahead of the white hats in the never-ending security game. One of the especially invidious ways hackers have found to evade detection is through mutation – changing the code in a virus on each copy, defeating classical signature detection methods and potentially requiring… Read More










Real men have fabs!