With NIST performing its down-select to four post-quantum cryptography (PQC) algorithms for standardization in July 2022, some uncertainty remains. Starting an SoC with fixed PQC IP right now may be nerve-wracking, with possible PQC algorithm changes before standardization and another round of competition for even more advanced algorithms coming. Yet, PQC mandates loom, such as an NSA requirement starting in 2025. A low-risk path proposed in a short white paper by Xiphera and Flex Logix sees eFPGAs handling crypto-agility for SoCs with PQC.
Now the PQC algorithm journey gets serious
NIST selected four algorithms – CRYSTALS-Kyber, CRYSTALS-Dilithium, Falcon, and SPHINCS+ – that withstood the best attempts to expose vulnerabilities during its competition phase. In doing so, NIST now focuses resources on these four algorithms for standardization, marking the start of the PQC journey in earnest. Using teams of researchers armed with supercomputers, it can take years to thoroughly study a proposed crypto algorithm for potential vulnerabilities. A prime example: two PQC algorithms in the NIST competition broke under the weight of intense scrutiny very late in the contest, eliminating them from consideration.
While the odds of a significant break in these four selected PQC algorithms are low, minor changes are a distinct possibility. Uncertainty keeps many in the crypto community up at night, and changes that could disrupt hardware acceleration IP are always a concern for SoC developers. Hardware acceleration for these complex PQC algorithms is a must, especially in edge devices with size, power, and real-time determinism constraints.
Unfortunately, staying put isn’t an option, either. Existing crypto algorithms are vulnerable to quantum computer threats, if not immediately, then very soon. SoCs designed for lifecycles of more than a couple of years using only classical algorithms will be in dire peril when quantum threats materialize. The challenge becomes how to start a long life cycle SoC design now that can accelerate new PQC algorithms without falling victim to changes in those algorithms during design or, even worse, after it is complete.
Redefining crypto-agility practices for PQC in hardware
Crypto-agility sounds simple. Essentially, the idea is to run more than one crypto algorithm in parallel, with the objective that if one is compromised, the others remain intact, keeping the application secure. Researchers are already floating the idea of hybrid mechanisms as a safety net for PQC implementations. It’s possible to combine a traditional crypto algorithm, likely an ECC-based one, with a new PQC algorithm for the key derivation function (KDF).
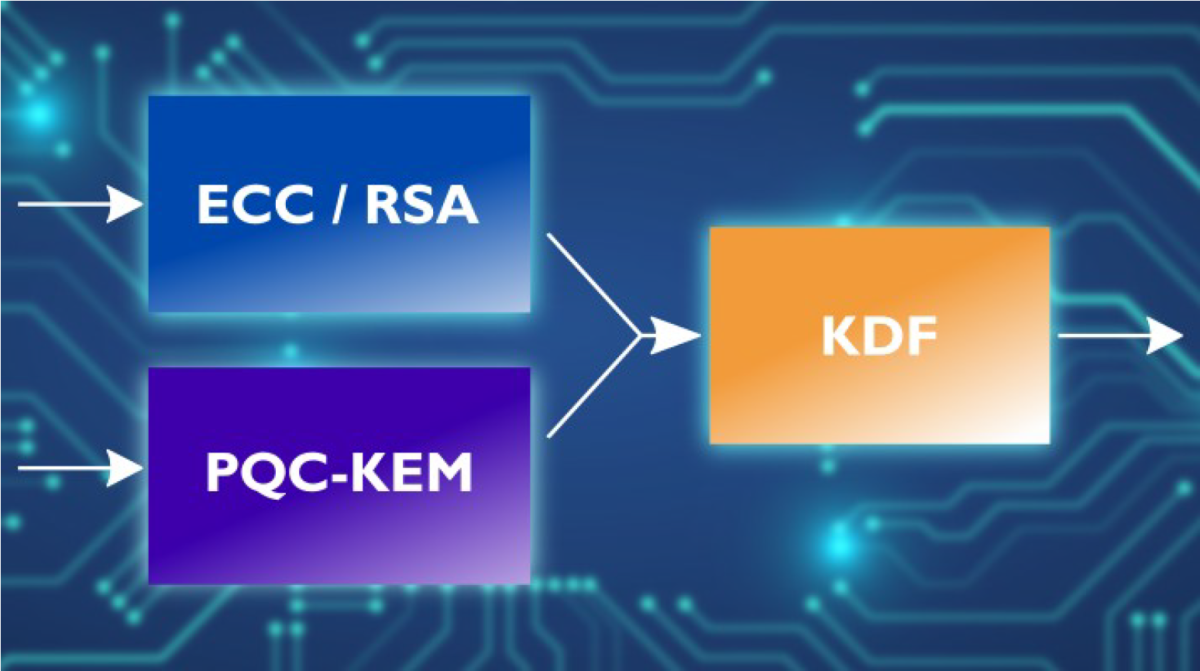
But in SoC form, hybrid mechanisms have a cost, which gets higher as complexity increases. Instead of replacing the existing crypto hardware IP, a hybrid approach adds more circuitry for PQC and coordination between the algorithms. Size, power consumption, and latency increase, and another risk emerges. Designers would have to guess correctly about implementing a PQC algorithm; otherwise, the implementation would essentially be classical. The PQC hardware would lay unutilized, wasting space and power used for it entirely and leaving the design as vulnerable as it was without PQC.
A better approach to crypto-agility is reconfigurable computing. If hardware is reconfigurable, patching, upgrading, or replacing algorithms is straightforward. A creative design could even implement a hybrid mechanism on the fly, running one algorithm for a classical key, then reconfiguring to run PQC for its key, then reconfiguring again for operation on a data stream once keys are derived.
eFPGA technology provides a robust, proven reconfigurable computing solution for SoCs now. It’s efficient from a power and area standpoint, rightsized to the SoC design and the logic needed for algorithms. And in a PQC context, it provides the ultimate protection while designs are in progress and algorithms may be in flux.
Xiphera, a hardware-based security solution provider, is teaming up with Flex Logix to bring crypto-agility to SoCs using eFPGAs. Following is a page describing the effort with a link to a short white paper with more background, and a link to the Flex Logix eFPGA page.
Xiphera: Solving the Quantum Threat with Post-Quantum Cryptography on eFPGAs
Flex Logix: What is eFPGA?
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.