Kai Beckmann is a Member of the Executive Board at Merck KGaA, Darmstadt, Germany, and the CEO of Electronics. He is responsible for the Electronics business sector, which he has been leading since September 2017. In October 2018, Kai Beckmann also took over the responsibility for the Darmstadt site and In-house Consulting. In addition, he acts as the Country Speaker for Germany with responsibility for co-determination matters.
Prior to his current role, Kai Beckmann was Chief Administration Officer of Merck KGaA, Darmstadt, Germany, with responsibility for Group Human Resources, Group Business Technology, Group Procurement, In-house Consulting, Site Operations and the company’s Business Services, as well as Environment, Health, Safety, Security, and Quality.
In 2007, he became the first Chief Information Officer of Merck KGaA, Darmstadt, Germany, with responsibility for Corporate Information Services. From 2004 to 2007, he served as Managing Director of Singapore and Malaysia, and prior to that he held senior executive responsibility for the Information Management and Consulting unit from 1999 to 2004. He began his career at Merck KGaA, Darmstadt, Germany in 1989 as an IT system consultant.
Kai Beckmann studied computer science at the Technical University of Darmstadt from 1984 to 1989. In 1998, he earned a doctorate in Economics while working. He is married and has one son.
Tell us about EMD Electronics
Merck KGaA, Darmstadt, Germany, operates across life science, healthcare, and electronics. More than 60,000 employees work to make a positive difference in millions of people’s lives every day by creating more joyful and sustainable ways to live. In 2021, Merck KGaA, Darmstadt, Germany, generated sales of € 19.7 billion in 66 countries. The company holds the global rights to the name and trademark “Merck” internationally. The only exceptions are the United States and Canada, where the business sectors of Merck KGaA, Darmstadt, Germany, operate as MilliporeSigma in life science, EMD Serono in healthcare, and EMD Electronics in electronics.
As EMD Electronics we are the company behind the companies advancing digital living. Our portfolio covers a broad range of products and solutions, including high-tech materials and solutions for the semiconductor industry, as well as liquid crystals and OLED materials for displays and effect pigments for coatings and cosmetics. We offer the broadest portfolio of innovative materials in the semiconductor industry and support our customers in creating industry-leading microchips. In the US, EMD Electronics alone has approximately 2,000 employees across the country, with more than a dozen manufacturing and R&D sites spanning the continental U.S.
Last year you announced a $1 billion investment in the US to support semiconductor customers. Can you tell us more about these investments?
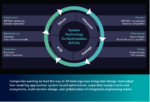
These investments are part of our global program called “Level Up” for investing in R&D, capacity, and accelerating growth in the semiconductor and display markets. Over the next five years, we plan to spend around $2.5 billion globally in long-term fixed assets (capital expenditures) in Semiconductor and Display Solutions. In the U.S., EMD Electronics plans to invest primarily in its Arizona, California, Texas, and Pennsylvania sites. Last year, we announced global investments of more than $3.5 billion as part of our “Level Up” growth program. With this, we seek to capture the growth opportunities that come with the significantly accelerating global demand for innovative semiconductor and display materials. This demand is driven by exponential data growth and highly impactful technology trends that include remote working, the growth of AI, and soaring demand for electric vehicles. Our “Level Up” growth program focuses on four mutually reinforcing key priorities: Scale, Technology, Portfolio, and Capabilities. Further investing in these four areas builds the foundation of our ambitious growth targets, in conjunction with the strong demand for electronics materials, particularly semiconductors.
Sustainability is becoming increasingly important across the industry. What is Merck KGaA, Darmstadt, Germany, and especially the business of EMD Electronics doing to ensure a sustainable future?
We believe that we can harness science and technology to help tackle many global challenges. Always guided by a robust set of values, we approach all our actions and decisions with a sense of responsibility. Sustainability has therefore been vital to us for many generations. We can only ensure our own future success by also creating lasting added value for society.
In creating long-term added value for society, we have defined three goals within our sustainability strategy. In 2030, we will achieve progress for more than one billion people through sustainable science and technology, along with integrating sustainability into all our value chains. By 2040, we will be climate-neutral and reduce our resource consumption. Most of our greenhouse gas emissions stem from process-related emissions during the production of specialty chemicals for the electronics industry. With improved processes, Merck can significantly reduce those emissions in the future.
As a materials supplier for the electronics industry, we are a key enabler for sustainable innovation. We are addressing emissions through abatement and alternatives. For example, we are now designing a process for large-scale NF3 abatement as a pre-requisite to meet our long-term GHG goals, and to drive decarbonization in the industry. In addition to optimizing our own processes to find more sustainable solutions, we are also a trustworthy partner for our customers to support them on their sustainability journey. Just recently we announced our collaboration with Micron, testing an alternative low-GWP etch gas of ours, further aligning on our shared sustainability goals.
You recently attended Semicon West. What were your reactions to being back in person with customers at a trade show in the US, and what announcements or innovations were you most excited about?
I truly appreciated being able to re-connect with many great people from all over the world face-to-face. SEMICON West is the choice place to exchange on key topics in our industry, tackling industry challenges, and to establish partnerships and collaborations. The vitality of innovation never stops and it’s wonderful to see the progress the industry is making. It is fascinating to see how the industry is driving innovations in new materials in fields such as 3D NAND, FinFET, Nanosheet or EUV, to continuously make devices more intelligent, power efficient and smaller. With the move to 3D, shrinking is no longer the most cost-effective way to increase density. Feature sizes for 3D chips will no longer shrink and may increase, as they already have for 3D NAND. I also heard several times “etch could become the new litho”. Since Merck is supplying materials for all parts of the manufacturing process – litho, deposition, etch, CMP, cleans, you name it – we are well positioned to participate in the continued growth story that is Moore’s Law, 2nd edition. Additionally, we appreciate that sustainability is becoming more and more important in our industry where we are a well-respected partner for our customers.
Finally, let me mention data analytics as one driving force for the industry. We combine a data-driven approach with a physics-based expertise. In December last year we formed the independent partnership Athinia together with Palantir to deliver a secure collaborative data analytics platform for the semiconductor industry. The Athinia platform will leverage AI and big data to solve critical challenges, improve quality and supply chain transparency, and time to market. At Semicon West Athinia announced that Micron Technology plans to use the data analytics platform to create a pioneering data collaboration ecosystem that will help lead a continued journey of digital transformation with Micron’s critical suppliers.
Advancing Digital Living has data at its core, data that will be continually leveraged in the coming decade. Our teams pioneer digital solutions that ensure we can deliver high-caliber, customized quality control that allows for optimal material performance. Our digital solutions team also serves customers in predictive quality analysis. Our approach starts at the production level, which is at the center of the supply chain, interacting with customers and partners. We gain learnings from the use of the right technology or system and then adapt, and scale as needed, ultimately allowing us to identify which characteristics led to the “golden batch”. This also helps to accelerate new material development in the future as we transfer the learnings in R&D in a systematic way periodically. By the way, minimizing quality-based excursions also offers sustainability benefits, minimizing wasted product and suboptimal paths through supply chains.
For more information click HERE.
Also read:
CEO Interview: Jaushin Lee of Zentera Systems, Inc.
CEO Interview: Shai Cohen of proteanTecs
CEO Interview: Barry Paterson of Agile Analog