Before the advent of the digitized society and computer chips, things that needed protection were mostly hard assets such as jewelry, coins, real estate, etc. Administering security was simple and depended on strong guards who provided security through physical means. Then came the safety box services offered by financial institutions such as banks. The bank vaults themselves were not easily penetrable and the assets remained safe. But the service itself was not of much value if the assets couldn’t be taken out and put back in whenever the bank customer wanted. And therein was the vulnerable aspect of the service, which was at the time and point of access. What if an unauthorized party gets hold of the safety box key and accesses the contents? The institutions offering the service instituted a two-step process. The first step was to authenticate the party who wants to access the box contents. This was accomplished by checking the person’s relevant identity credentials. The second step was to use the appropriate key to open the box itself. To prevent any bad actors within the institution itself from opening the box without the customer being present, a dual-key mechanism was deployed.
Fast forward to the digitized society, other than the house we live in and the vehicles we drive, most other assets are not physical in nature. Stocks, bonds, intellectual property ownership, fiat currencies, crypto currencies, etc. The list goes on. These assets are secured not by some physical means but rather through encryption and storage in the form of zeroes and ones in electronic form around the world. In other words, security is being provided through a combination of electronic hardware/software solutions. For every security solution that is deployed, cyber criminals are always working to identify a weakness to break-in and steal assets. The goal of digital security mechanisms deployed in electronic systems is efficiency and effectiveness. At a conceptual level, the mechanism is similar to the bank safety box access method. Authenticate the user and decrypt the data using valid keys. Given this, how to protect and secure the interfaces without compromising on fast access time for legitimate users of the assets? Low latency authentication and encryption are key.
Starts with the Design
The added complication with digital security mechanisms is that they have to deal with many different types of interfaces to the data. This is pushing the industry to look at security as an integral part of electronic design architecture, not as an afterthought. The block diagram below showcases the various types of data interfaces in an electronic system.
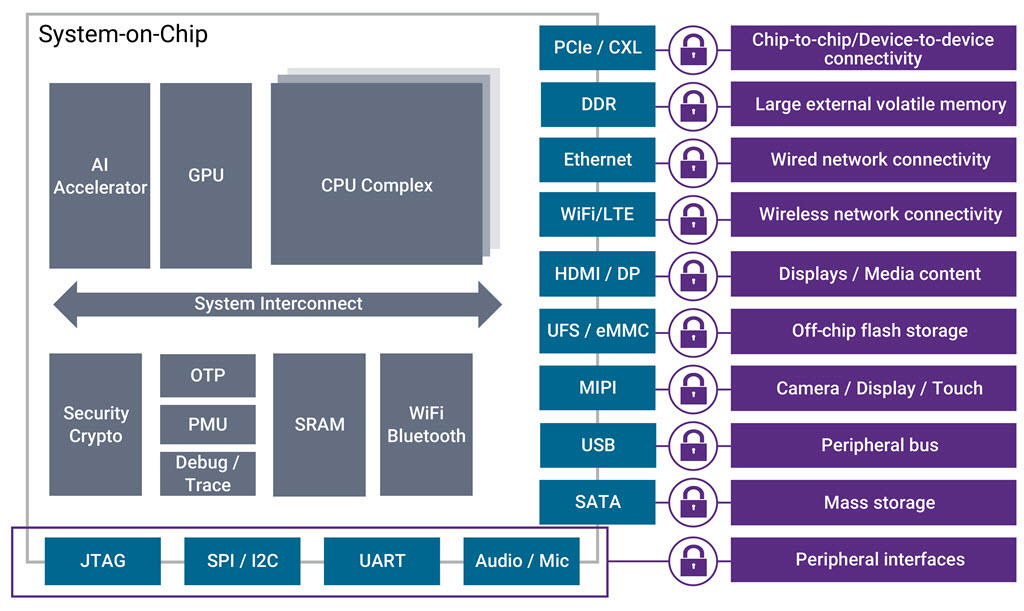
Securing all of these interfaces at a hardware level and implementing zero-knowledge architecture so that the data is encrypted and can’t be used maliciously is critical. To add complexity to the mix, the interface standards bodies are regularly upgrading existing protocol specifications and bringing out new interfaces standards as well. These changes need to be implemented in designs either at the controller level, PHY level or both without compromising throughput and latencies.
The Demand for Secure Interface Solutions Keeps Growing
As an example, while the autonomous vehicle market is still in its early stage, it has already exposed security risks that are being addressed by today’s specifications used in cars for networking, ADAS camera/sensor connectivity, and displays. As advances in various fields of technology and markets happen, better security implementations will be needed. For example, quantum computing will have the capability to break today’s public key algorithms. Interface standards will need to adapt with quantum-safe algorithms over the coming years.
Implementing data security will continue to be on the top of the list of SoC designers’ tasks.
Synopsys Secure Interfaces
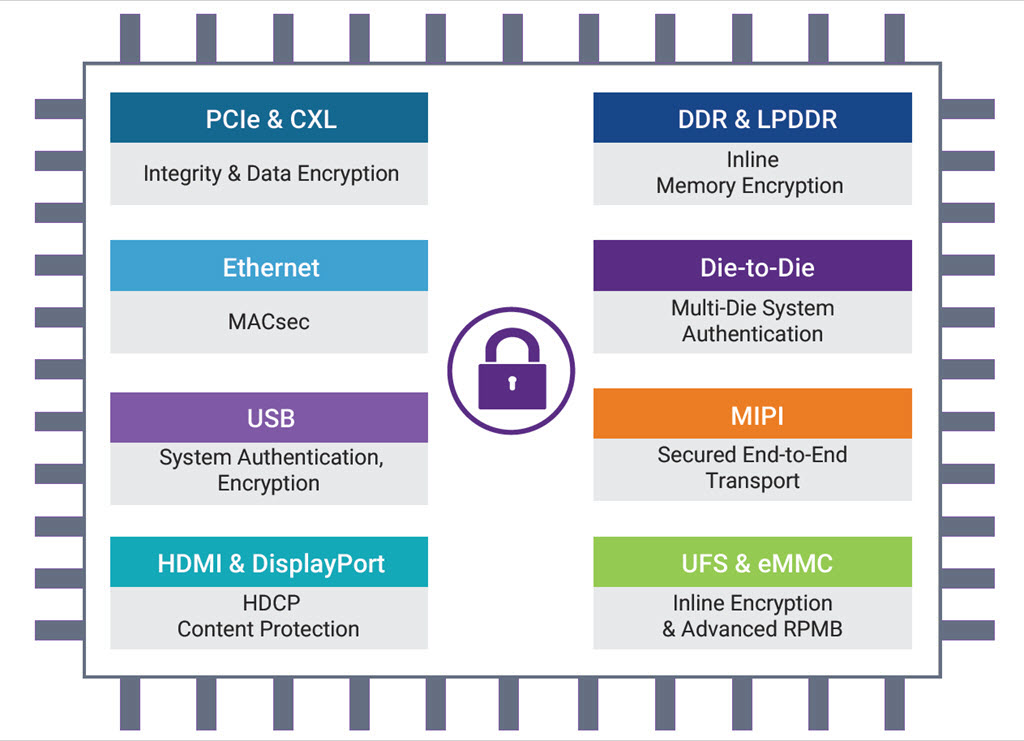
Synopsys offers the entire spectrum of interfaces that designers need for a variety of different applications. Their Interface IP products are pre-verified solutions that include silicon-proven Synopsys Controllers integrated with security features and offer reduced risk solutions for optimal security, low latency and area without compromising on performance. This makes it easier for SoC designers to address and implement data protection and security for quick time-to-market.
For more details on the following interfaces, visit the interfaces portfolio page.
Summary
Incorporating security into SoCs is a fundamental requirement for complying with international laws and regulations and satisfying privacy and data protection requirements of electronic systems users. Synopsys offers the industry’s broadest secure interfaces built for various applications such as HPC, Mobile, Automotive and IoT. For more details on Synopsys’ secure interface IP products, visit the product page.
Also Read:
Synopsys Crosses $5 Billion Milestone!
Configurable Processors. The Why and How
New ECO Product – Synopsys PrimeClosure
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.