GenAI, the most talked-about manifestation of AI these days, imposes two tough constraints on a hardware platform. First, it demands massive memory to serve large language model with billions of parameters. Feasible in principle for a processor plus big DRAM off-chip and perhaps for some inference applications but too slow … Read More
Tag: ethernet
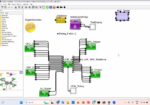
A Modeling, Simulation, Exploration and Collaborative Platform to Develop Electronics and SoCs
During the GOMACTech conference held in South Carolina last week I had a Zoom call with Deepak Shankar, Founder and VP Technology at Mirabilis Design Inc. to ask questions and view a live demo of VisualSim – a modeling, simulation, exploration and collaborative platform to develop electronics and SoCs. What makes VisualSim so … Read More
Key MAC Considerations for the Road to 1.6T Ethernet Success
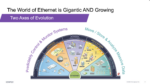
Ethernet’s continual adaptation to meet the demands of a data-rich, interconnected world can be credited to the two axes along which its evolution has been propelled. The first axis emphasizes Ethernet’s role in enabling precise and reliable control over interconnected systems. As industries embrace automation… Read More
Why Secure Ethernet Connections?
While web browsing I constantly glance for the padlock symbol to indicate that the site is encrypting any of my form data by using the https prefix, which means that an SSL (Secure Sockets Layer) certificate is being used by the web hosting company. I have peace of mind knowing that my credit card information cannot be easily stolen… Read More
Driving the Future of HPC Through 224G Ethernet IP
The need for speed is a never-ending story when it comes to data communications. Currently there are a number of trends such as cloud computing, artificial intelligence, Internet of Things (IoT), multimedia applications and consumer expectations driving this demand. All of these trends are accelerating the growth in high-performance-computing… Read More
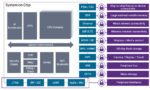
How to Efficiently and Effectively Secure SoC Interfaces for Data Protection
Before the advent of the digitized society and computer chips, things that needed protection were mostly hard assets such as jewelry, coins, real estate, etc. Administering security was simple and depended on strong guards who provided security through physical means. Then came the safety box services offered by financial … Read More
Stop-For-Top IP Model to Replace One-Stop-Shop by 2025
…and support the creation of successful Chiplet business
The One-Stop-Shop model has allowed IP vendors of the 2000’s to create a successful IP business, mostly driven by consumer application, smartphone or Set-Top-Box. The industry has dramatically changed, and in 2020 is now driven by data-centric application (datacenter,… Read More
Benefits of a 2D Network On Chip for FPGAs
The reason people love FPGAs for networking and communications applications is because they offer state of the art high speed interfaces and impressive parallel processing power. The problem is that typically a lot of the FPGA fabric resources are used simply to move the data on or off and across the chip. Achronix has cleverly … Read More
Demand for High Speed Drives 200G Modulation Standards
Right now, the most prevalent generation of Ethernet for data centers is 400 Gbps, with the shift to 800 Gbps coming rapidly. It is expected that by 2025 there will be 25 million units of 800 Gbps shipped. Line speeds of 100G are used predominantly for 400 Gbps Ethernet – requiring 4 lanes each. Initially 800 Gbps will simply … Read More
Controlling the Automotive Network – CAN and TSN Update
Cars are hotbeds of systems innovation. I’ve been fortunate to be asked to write about many of these areas, from the MEMS underlying sensors to ISPs and radars, intelligent imaging and sensor fusion. And many aspects of design for safety within the SoCs around a car. But I haven’t written much about the networks connecting these … Read More