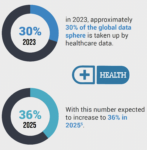
The rapid advancement of technology, including generative AI, IoT, and autonomous vehicles, is revolutionizing industries and enhancing efficiency. At the same time, such advances also generate huge amounts of data to be transmitted and processed to make sense and provide value to consumers and society as a whole. In essence,… Read More
SEMICON Japan 2024
SEMICON Japan is the premier event that brings together the semiconductor manufacturing supply chain for the latest insights, trends and innovations as the industry powers digital transformation. SEMICON Japan 2024 will highlight Smart applications powered by semiconductor technology such as automotive and Internet of… Read More