When I worked at Intel designing custom chips my management would often ask me, “Will first silicon work?” My typical response was, “Yes, but only for the functions that we could afford to simulate before tape-out.” This snarky response would always cause a look of alarm, quickly followed by a second … Read More
Checkout the Upcoming Synopsys Power Webinar
This is part 3 of a series of 4 on low power design, scheduled for September 21st at 10am. Kiran Vittal and Ken Mason will be discussing using the SpyGlass Power solutions (analysis and verification) to optimize power at RTL. Atrenta always had a leading position in this area; I expect a year following their acquisition by Synopsys,… Read More
Synopsys Webinar: MIPI Adoption Beyond Mobile, it’s now!
Some of the various MIPI specifications are now massively used in mobile (smartphone or tablet), especially the Multimedia related specs like Camera Serial Interface (CSI-2), Display Serial Interface (DSI) and D-PHY. You have to implement with CSI-2 or DSI controller a serial based physical interface, D-PHY specified up to… Read More
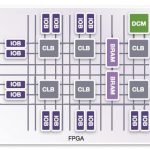
Did My FPGA Just Fail?
Designing DRAMs at Intel back in the 1970s I first learned about Soft Errors and the curious effect of higher failure rates of DRAM chips in Denver, Colorado with a higher altitude than Aloha, OR. With the rapid growth of FPGA-based designs in 2016, we are still asking the same questions about the reliability of our chips used for safety-critical… Read More
More on HAPS hybrid prototyping for ARMv8 with Linaro
A few weeks ago we previewed a Synopsys webinar describing how they are linking the ARM Juno Development Platform with the HAPS-80 and HAPS ProtoCompiler environment. I’ve had a look at the archived event and have some additional thoughts.… Read More
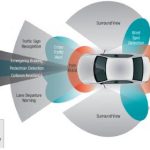
Foundation IP for Automotive: so Stringent Quality Requirements!
The Automotive IC market is not the largest segment, but is certainly the segments expected to grow with the highest CAGR, with 10.8% from 2013 to 2018, according with IC Insights (January 2015). If you consider the pretty long concept/design to production cycle time (7 years or more) as well as the numerous segments just emerging… Read More
Semi execs look at IoT tradeoffs a bit differently
What happens when you get a panel of four executives together with an industry-leading journalist to discuss tradeoffs in IoT designs? After the obligatory introductions, Ed Sperling took this group into questions on power, performance, and integration.… Read More
Catching low-power simulation bugs earlier and faster
I’ve owned and used many generations of cell phones, starting back in the 1980’s with the Motorola DynaTAC phone and the biggest usability factor has always been the battery life, just how many hours of standby time will this phone provide and how many minutes of actual talk time before the battery needs to be recharged… Read More
Webinar Alert – Helping Mixed Signal not be Mixed Up
Today’s profound statement: “don’t fall in love with your tools, figure out the biz process change first.” Mixed-signal SoC designers are having ample challenges with their design process and are in need of design management, but don’t want another tool to do it.… Read More
Radio Integration – the Benefits of Built-In
It’s always a pleasure when a vendor gives a really informative, vendor-independent presentation on what’s happening in some domain of the industry and wraps up with (by that point) a well-deserved summary of that vendor’ solutions in that space. Ron Lowman did just that at the Linley conference on Mobile and Wearables, where … Read More