I am delighted to share my technical insights into RISC-V in this article to inspire and prepare the next generation of chip designers for the future of the open era of computing. If you understand how we build complex electronic devices like desktops and smartphones using processors, you would be more interested in learning and exploring the Instruction Set Architectures.
Usually, we prefer Complex Instruction Set Computer, CISC for desktops/laptops, and Reduced Instruction Set Computer, RISC for smartphones. The OEMs like Dell and Apple have been using x86 CISC processor for their laptops. Let me explain here the laptop design approach. The motherboard has a multicore CISC processor as the main component, which is connected to GPUs, RAM, storage memory, and other subsystems and I/O interfaces. The operating system runs multiple applications in parallel on the multicore processor, managing the memory allocation and I/O operations.
This is how we can realize any electronic system using a processor. However, we prefer System-On-a-Chip using RISC processor for smartphones as it helps us reduce the motherboard’s size and power consumption. Almost the entire system with multi-core RISC CPUs, GPUs, DSPs, Wireless and interface subsystems, SRAMs, Flash memories, and IPs is implemented on an SoC. The OEM Apple is following this smartphone’s SoC design approach even for their MAC books as an OEM trendsetter. All the latest MAC books use their M-series SoCs that use ARM’s RISC processor.
So, it’s evident that the proprietary ISAs Intel’s x86 or ARM’s RISC processors have been the choice of OEMs like Apple, Dell, Samsung, and others, but now why do we need an open ISA like RISC-V beyond all these well-proven proprietary ISAs.
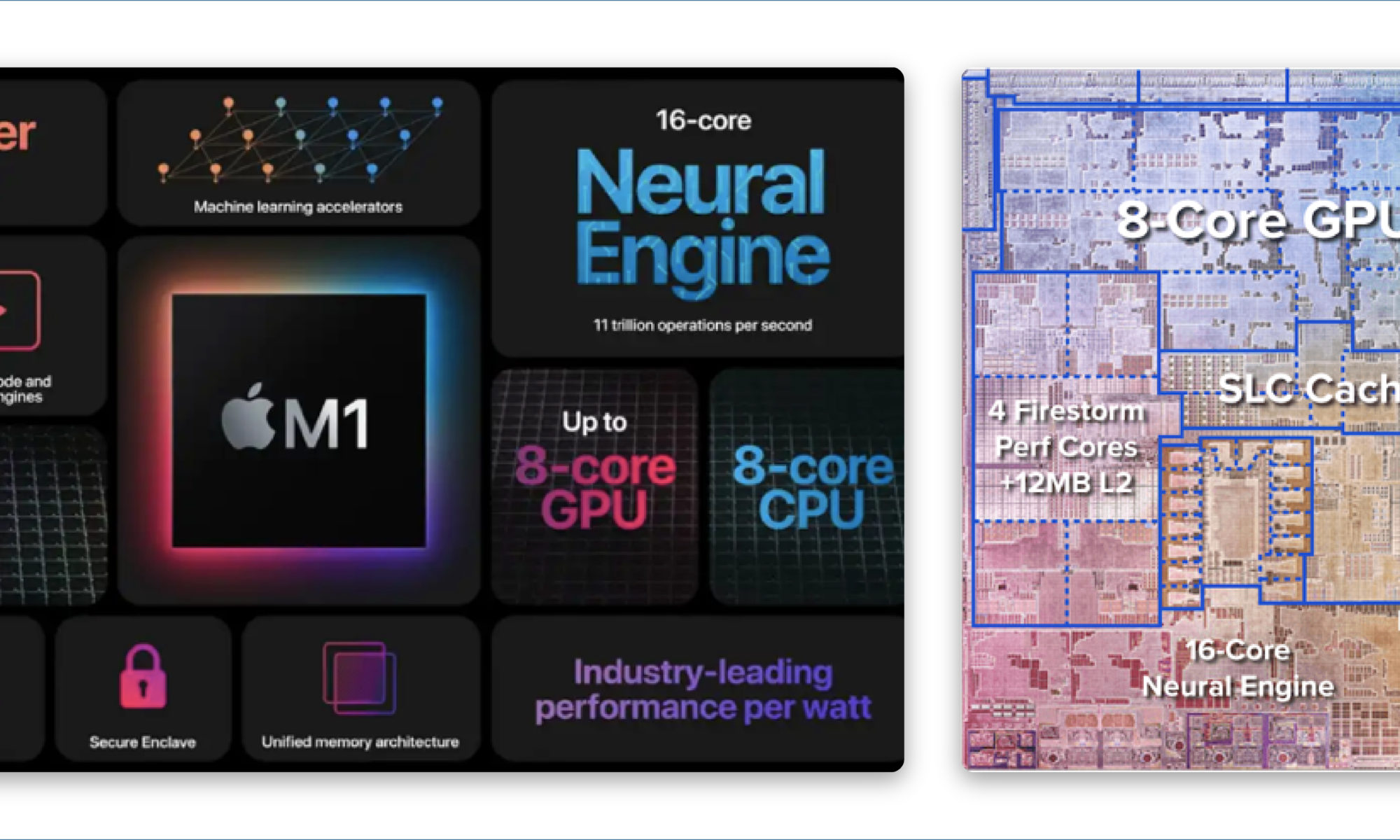
In today’s situation, everyone uses SoCs for their laptops and smartphones. This kind of complex SoC demands both general-purpose and specialized processors. To realize chips like Apple’s M-series SoCs, we need different kinds of processors like RISC CPUs, GPUs, DSPs, Security Processors, Image processors, Machine Learning accelerators, Security and Neural engines, based on various general purpose and specialized ISAs from multiple IP vendors, as shown in figure1.
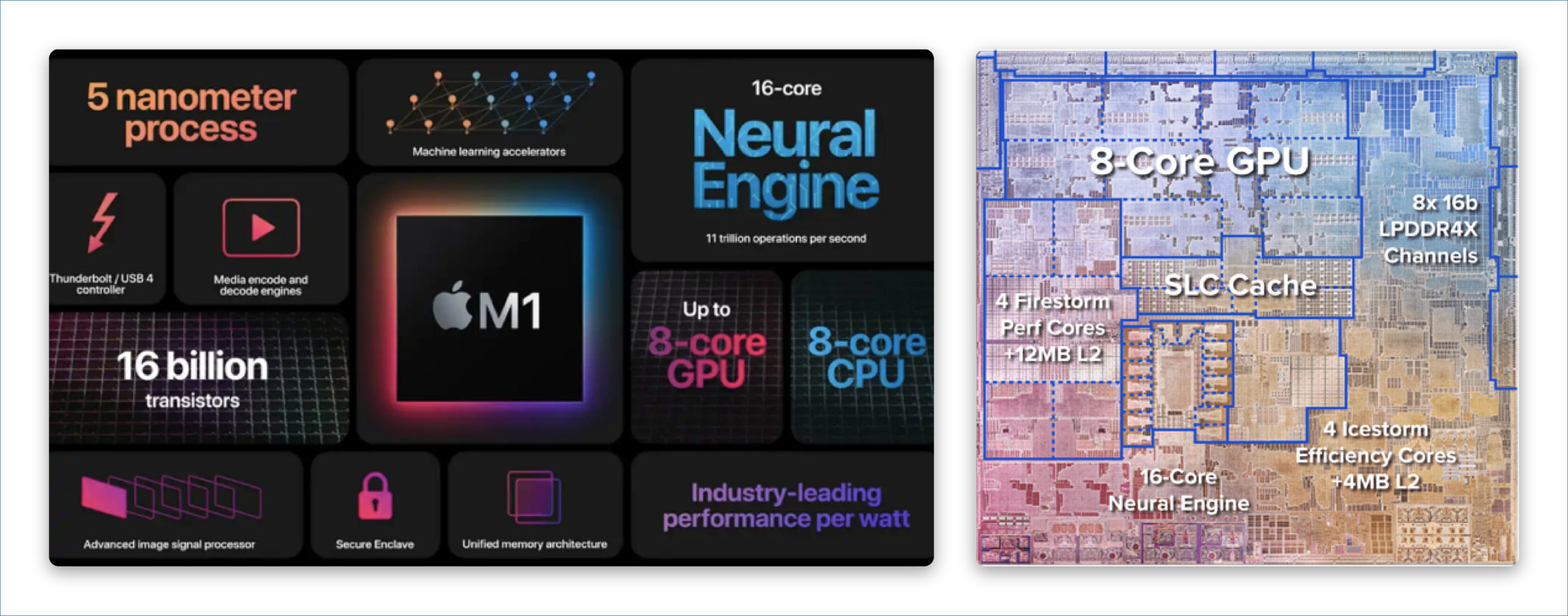
In this scenario, the major challenges would be:
- Choosing and working with multiple IP vendors
- Different IP vendors may have different IP licensing schemes, and the engineers will not have the freedom to customize the ISAs and design as they prefer to meet their design goals.
- All specialized ISAs will not last/survive for long, affecting the long-term product support plans and roadmaps.
- Also, the software/application development and updates involving multiple ISAs and toolchains would be challenging.
RISC-V is a general-purpose license-free open ISA with multiple extensions. It is an ISA separated into a small base integer ISA, usable as a base for customized accelerators and optional standard extensions to support general-purpose software development.
You can add your own extensions to realize your specialized processor or customize the base ISA if needed because it’s open. No license restrictions. So, in the future, we could create all general-purpose and specialized processors using only one RISC-V ISA and realize any complex SoC.
1. What’s RISC-V, and how it’s different from other ISAs?
RISC-V is a fifth major ISA design from UC Berkeley. It’s an open ISA maintained by a non-profit organization, RISC-V international, that involves all the stakeholders’ community to implement and maintain the ISA specifications, Golden reference models, and compliance test suites.
RISC-V is not a CPU implementation. It is an open ISA for both general-purpose and specialized processors. A completely open ISA that is freely available to academia and industry
RISC-V ISA is separated into a small base integer ISA, usable by itself as a base for customized accelerators or educational purposes, and optional standard extensions to support general-purpose software development
RISC-V supports both 32-bit and 64-bit address space variants for applications, operating system kernels, and hardware implementations. So, it is suitable for all computing systems, from embedded microcontrollers to cloud servers, as mentioned below.
Simple embedded microcontrollers
Secure embedded systems that run RTOS
Desktops/Laptops/Smartphones that run operating systems
Cloud Servers that run multiple operating systems
2. RISC-V Base ISA
RISC-V is a family of related ISAs: RV32I, RV32E, RV64I, RV128I
What RV32I/ RV32E/ RV64I/RV128I means:
RV – RISC-V
32/64/128 – Defines the Register width[XLEN] and address space
I – Integer Base ISA
32 Registers for all base ISAs
E – Embedded: Base ISA with only 16 registers
2.1 RISC-V Registers:
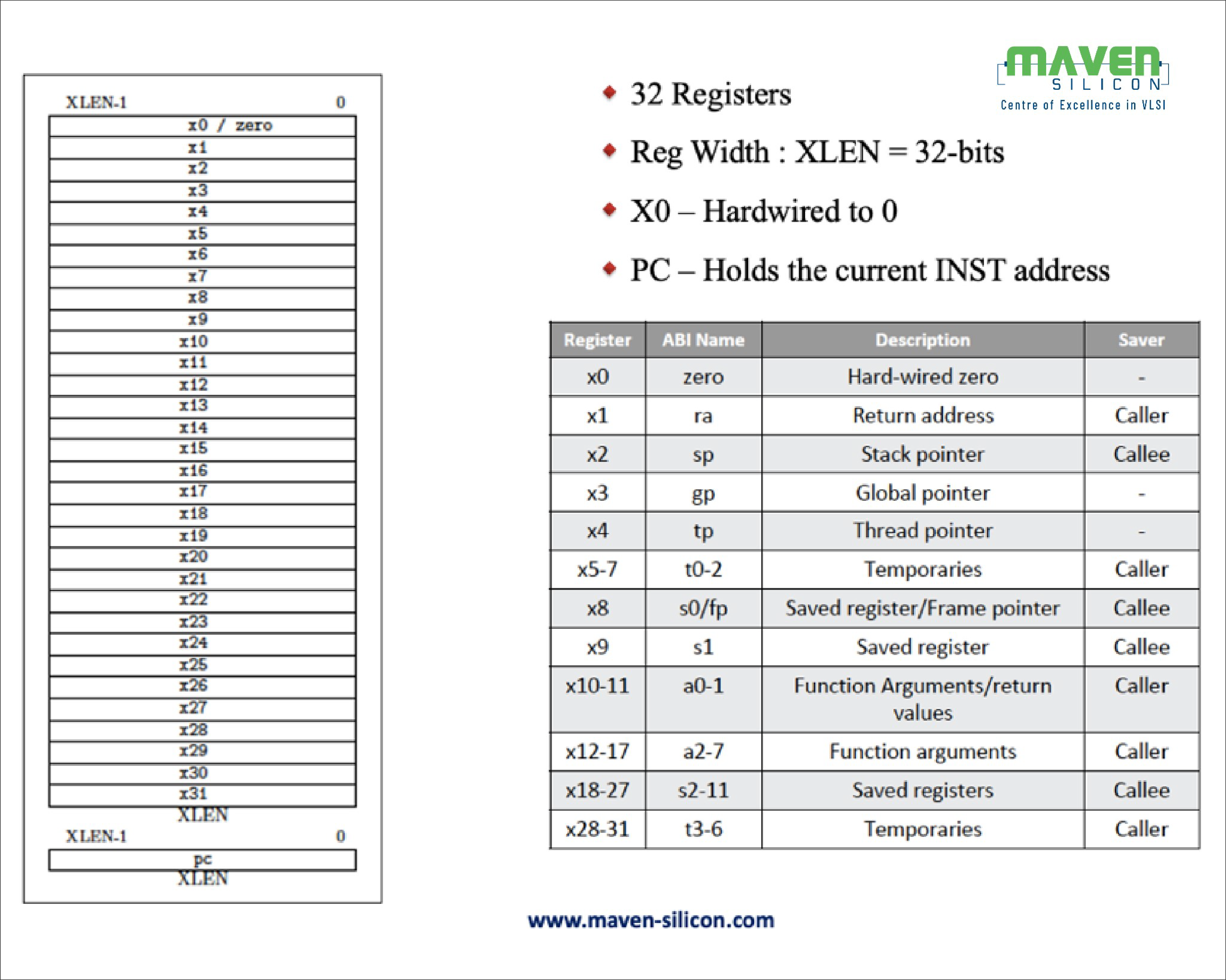
All the base ISAs have 32 registers as shown in the figure2, except RV32E. Only RV32E base ISA has only 16 Registers for simple embedded microcontrollers, but the register width is still 32 bits.
The register X0 is hardwired to zero. The special register called Program Counter holds the address of current instruction to be fetched from the memory.
As shown in figure-2, RISC-V Application Binary Interface, ABI defines standard functions for registers. The software development tools usually use ABI names for simplicity and consistency. As per the ABI, additional registers are dedicated for saved registers, function arguments and temporaries in the range X0 to X15, mainly for RV32E base ISA which needs only the top 16 registers for realising simple embedded microcontrollers. But the RV32I base ISA will have all 32 registers X0 to X31.
2.2 RISC-V Memory:
A RISC-V hart [Hardware Thread / Core] has a single byte-addressable address space of 2^XLEN bytes for all memory accesses. XLEN to refer to the width of an integer register in bits: 32/64/128.
Word of memory is defined as 32 bits (4 bytes). Correspondingly, a halfword is 16 bits (2 bytes), a doubleword is 64 bits (8 bytes), and a quadword is 128 bits (16 bytes).
The memory address space is circular, so that the byte at address 2^XLEN −1 is adjacent to the byte at address zero. Accordingly, memory address computations done by the hardware ignore overflow and instead wrap around modulo 2^XLEN.
RISC-V base ISAs have either little-endian or big-endian memory systems, with the privileged architecture further defining big-endian operation. Instructions are stored in memory as a sequence of 16-bit little-endian parcels, regardless of memory system endianness.
2.3 RISC-V Load-Store Architecture
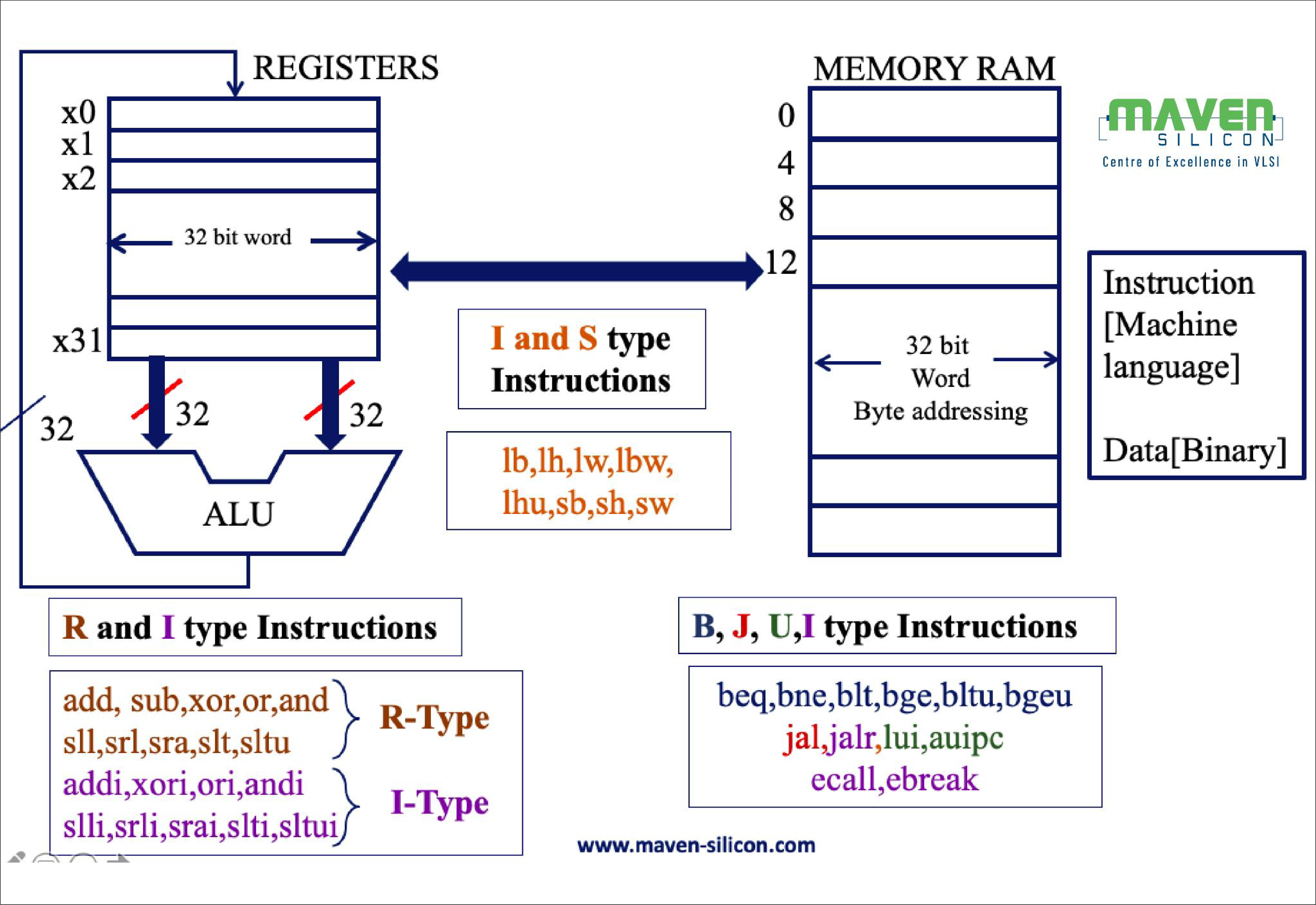
You can visualize the RISC-V load-store architecture that is based on RISC-V registers and memory, as shown below in figure3.
The RISC-V processor fetches/loads the instruction from main memory based on the address in PC, decodes the 32-bits instruction, and then the ALU performs Arithmetic/Logic/Memory-RW operations. The results of ALU would be stored back into its registers or memory.
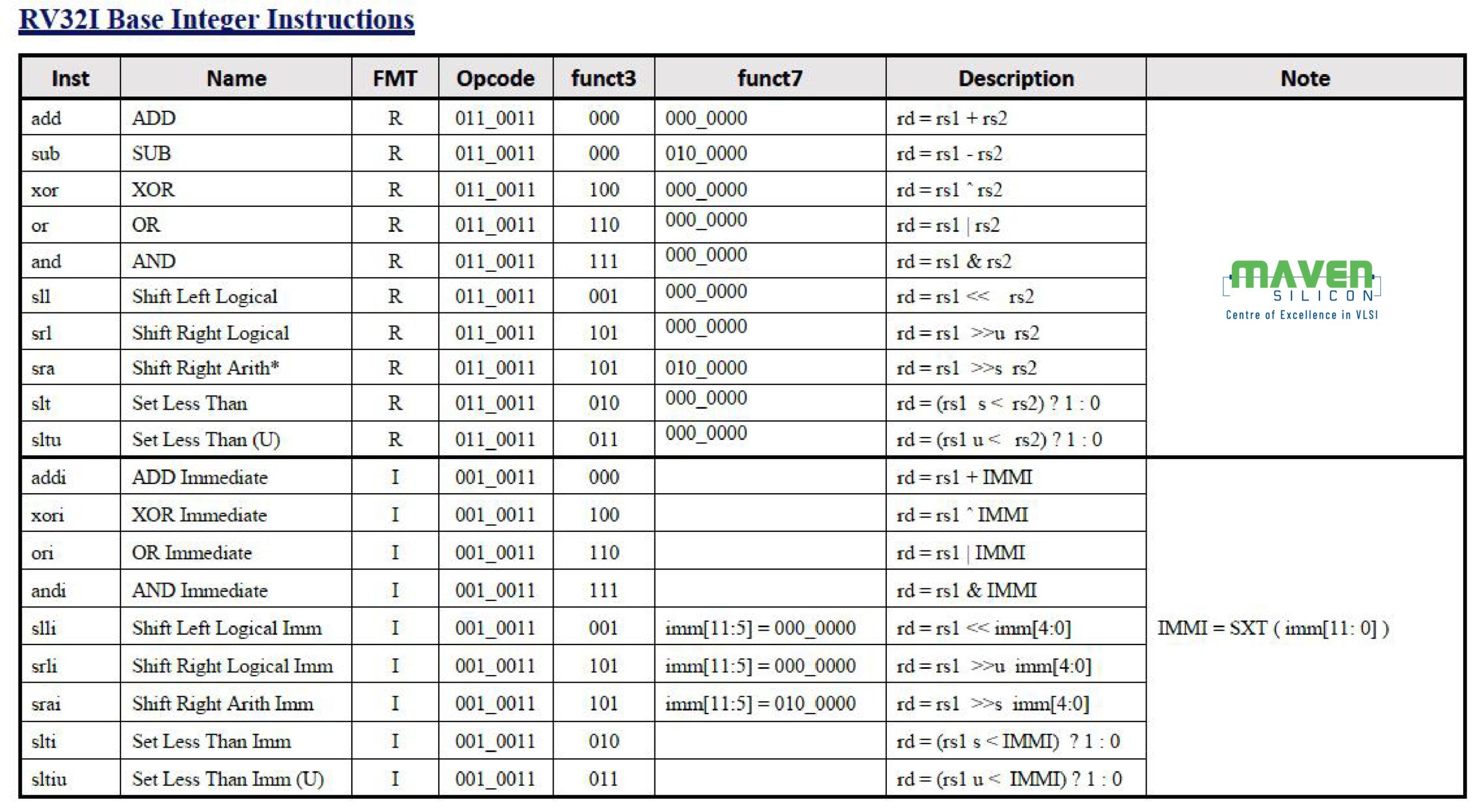
2.4 RISC-V RV32 I Base ISA:
RV32I base ISA has only 40 Unique Instructions, but a simple hardware implementation needs only 38 instructions. The RV32I instructions can be classified as:
R-Type: Register to Register instructions
I-Type: Register Immediate, Load, JLR, Ecall & Ebreak
S-Type: Store
B-Type: Branch
J-Type: Jump & Link
U-Type: Load/Add upper Immediate
2.5 RISC-V ISA for an optimized RTL Design:
Here I would like to explain how RISC-V ISA enables us to realize an optimized Register Transfer Level design to meet the low-power and high-performance goals.
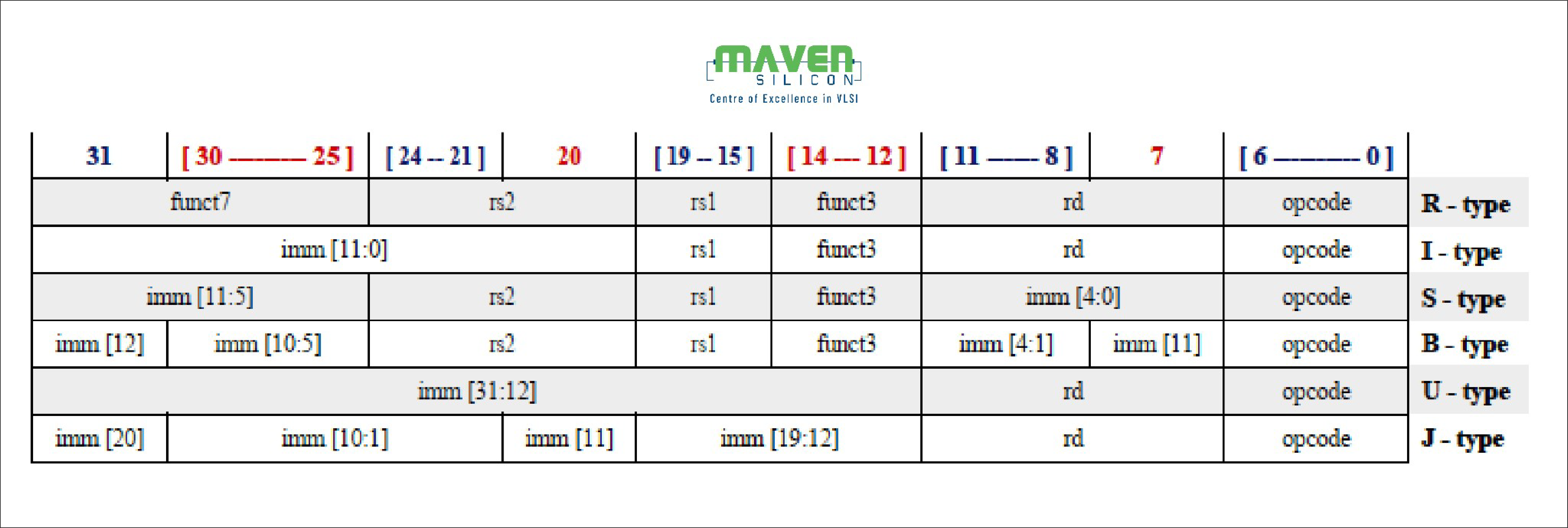
As shown in figure4, the RISC-V ISA keeps the source (rs1 and rs2) and destination (rd) registers at the same position in all formats to simplify decoding.
Immediates are always sign-extended, and are generally packed towards the leftmost available bits in the instruction and have been allocated to reduce hardware complexity. In particular,
the sign bit for all immediates is always in bit 31 of the instruction to speed sign-extension circuitry.
Sign-extension is one of the most critical operations on immediates (particularly for XLEN>32),
and in RISC-V the sign bit for all immediates is always held in bit 31 of the instruction to allow
sign-extension to proceed in parallel with instruction decoding.
To speed up decoding, the base RISC-V ISA puts the most important fields in the same place in every instruction. As you can see in the instruction formats table,
- The major opcode is always in bits 0-6.
- The destination register, when present, is always in bits 7-11.
- The first source register, when present, is always in bits 15-19.
- The second source register, when present, is always in bits 20-24.
But why are the immediate bits shuffled? Think about the physical circuit which decodes the immediate field. Since it’s a hardware implementation, the bits will be decoded in parallel; each bit in the output immediate will have a multiplexer to select which input bit it comes from. The bigger the multiplexer, the costlier and slower it is.
It’s also interesting to note that only the major opcode (bits 0-6) is needed to know how to decode the immediate, so immediate decoding can be done in parallel with decoding the rest of the instruction.
2.6 RV32I Base ISA Instructions
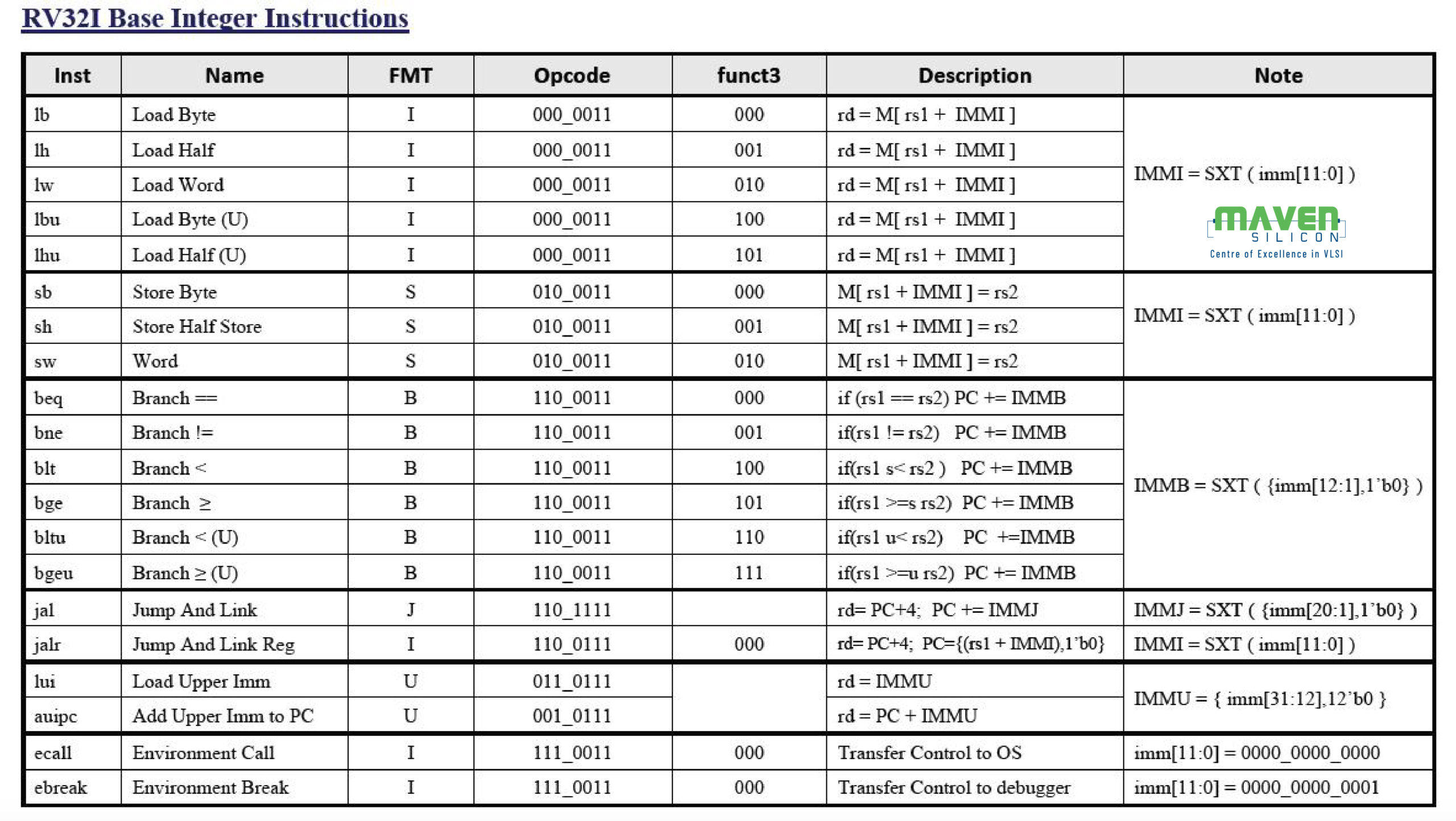
3. RISC-V ISA Extensions
All the RISC-V ISA extensions are listed out here:
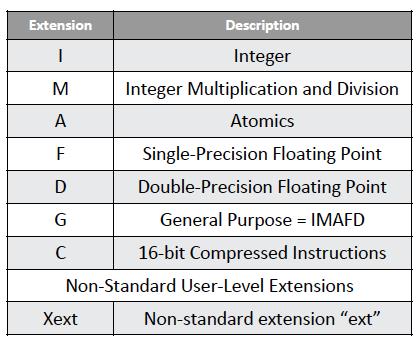
We follow the naming convention for RISC-V processors as explained below:
RISC-V Processors: RV32I, RV32IMAC, RV64GC
RV32I: Integer Base ISA implementation
RV32IMAC: Integer Base ISA + Extensions: [Multiply + Atomic + Compressed]
RV64GC: 64bit IMAFDC [G-General Purpose: IMAFD]
Integer 64 bits Base ISA + Extensions: [Multiply + Atomic + SP Floating + DP Floating + Compressed]
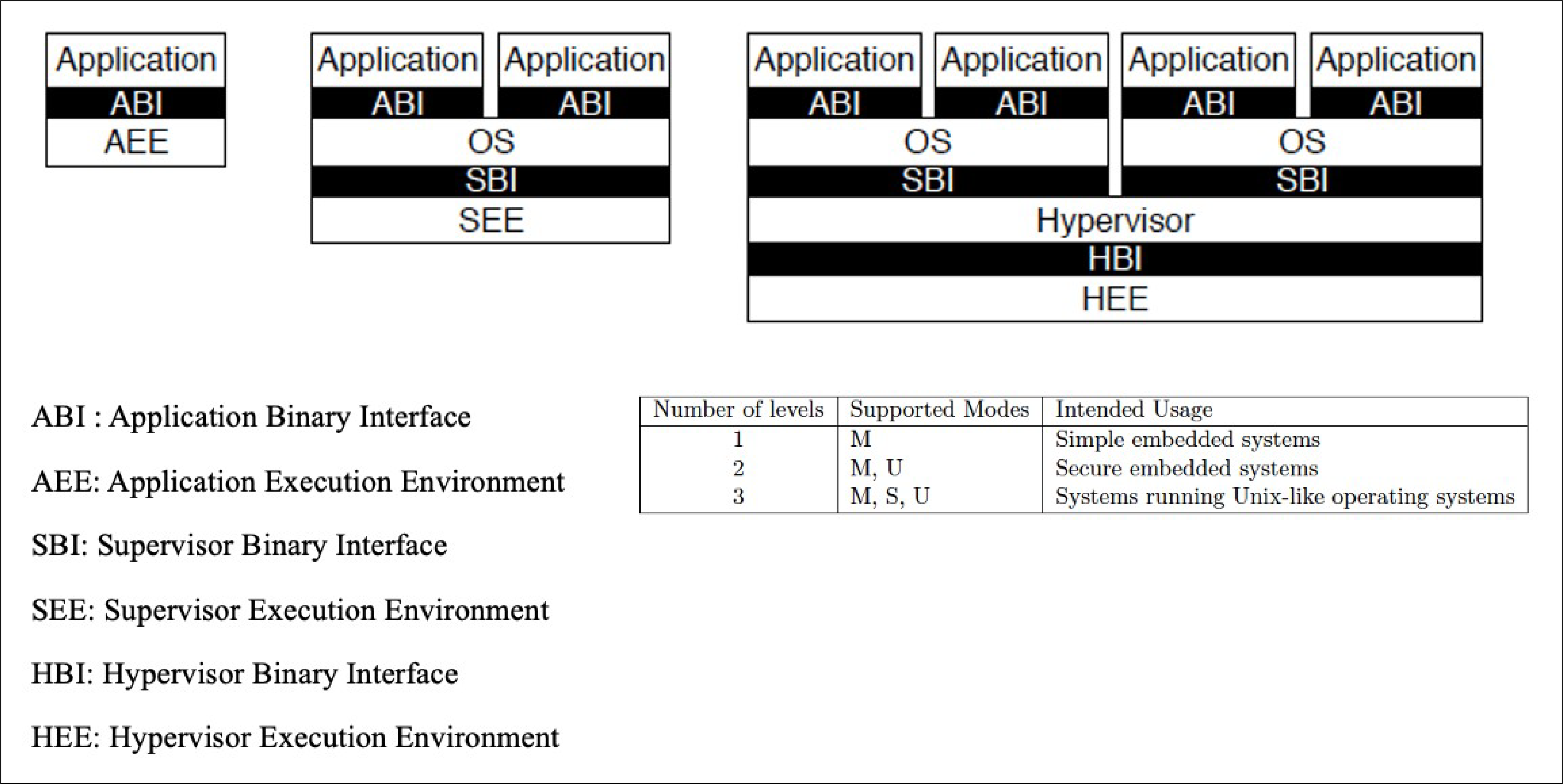
4. RISC-V Privileged Architecture
RISC-V privileged architecture covers all aspects of RISCV systems beyond the unprivileged ISA which I have explained so far. Privileged architecture includes privileged instructions as well as additional functionality required for running operating systems and attaching external devices.
As per the RISC-V privileged specification, we can realize different kinds of systems from simple embedded controllers to complex cloud servers, as explained below.
Application Execution Environment – AEE: “Bare metal” hardware platforms where harts are directly implemented by physical processor threads and instructions have full access to the physical address space. The hardware platform defines an execution environment that begins at power-on reset. Example: Simple and secure embedded microcontrollers
Supervisor Execution Environment – SEE: RISC-V operating systems that provide multiple user-level execution environments by multiplexing user-level harts onto available physical processor threads and by controlling access to memory via virtual memory.
Example: Systems like Desktops running Unix-like operating systems
Hypervisor Execution Environment – HEE: RISC-V hypervisors that provide multiple supervisor-level execution environments for guest operating systems.
Example: Cloud Servers running multiple guest operating systems
Also, the RISC-V privileged specification defines various Control and Status Registers [CSR] to implement various features like interrupts, debugging, and memory management facilities for any system. You may want to refer to the specification to explore more.
As explained in this article, we could efficiently realize any system, from simple IoT devices to complex smartphones and cloud servers, using a common open RISC-V ISA. With monolithic semiconductor scaling failing, specialization is the only way to increase computational performance. The open RISC-V ISA is modular and supports custom instructions making it ideal for creating a wide range of specialized processors and accelerators.
As we witnessed great success in chip verification from the emergence of IEEE standard Universal Verification Methodology, the open RISC-V ISA will also emerge as an industry-standard ISA by inheriting all good features from various proprietary ISAs and lead us to the future of an open era of computing. Are you ready with RISC-V expertise for this amazing future?
Author: P R Sivakumar, Founder and CEO, Maven Silicon
LinkedIn Profile: https://www.linkedin.com/in/sivapr/
Also Read:
CEO Interview: Sivakumar P R of Maven Silicon
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.