You don’t often hear about the inner workings of EDA tools and flows – the marketing guys much prefer telling us about all the exciting things their tools can do rather than the internal plumbing. But this matters for making design flows – and building these has largely been left to the users to sort out. That’s an increasing challenge as designs and EDA tools get more complex and it’s sometimes become necessary to run a part of one tool from within another. To enable that, EDA companies have to pick up their share of the work.
That’s particularly the case for point tools in largely integrated vendor design flows. Calibre is perhaps the best known point tool out there and one common to all major analog, digital and mixed signal design flows. So it’s interesting to hear what Siemens EDA is doing here with Calibre.
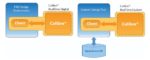
Calibre’s RealTime interface supports this closer flow integration and is an established presence in all major digital and custom implementation flows.
How modern design flows drive closer tool interactions
While the Siemens EDA white paper here (link at the end) spends some time discussing the costs and benefits of best-in-class tool flows (like most Calibre ones) versus full single-vendor flows, that’s really a subject in itself (interesting, but perhaps for a separate article). The reality today is that users frequently need some third party point tools to be integrated into flows and it’s likely that many will always demand this.
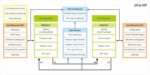
We used to think in terms of a serial design flow where each tool has a distinct flow step and there’s little overlap between the tools. Something like this example for place and route:
Of course, we’ve simplified a bit here – we check (verification) after each step and have frequent iterative loops back to try things like alternative placements.
With today’s huge, hierarchical designs, leaving the entirety of signoff steps like DRC and LVS to the end of the flow is inefficient and puts signoff schedules at risk. Many of these checks can be done earlier in the flow. We just need an efficient way to do it. Similarly, it’s often helpful to do some local resynthesis within placement to minimise total flow run time.
What we’re looking for here might be called “on demand checking” (or implementation) – doing a local operation on a part of a design exactly when we need to, by pulling forward functionality from one tool to run within an earlier one in the flow. As ever, we want to run things as early as we possibly can – what Siemens call shift left.
It’s a real change in how we think about tools and flows.
How APIs help us here
We’ve always been able to add custom menus in tool GUIs and inject custom Tcl scripts into tool run scripts to access other tools. What’s usually been lacking is being able to call external tool functionality with the lowest interfacing delay and smallest memory footprint with clean, documented reliable integration that regular users can configure. We certainly don’t want to pass the entire design or invoke all the functionality of another tool if we can possibly avoid it.
At first glance, this would appear to be a decisive advantage for more integrated single vendor flows and an increasing drag on integrating other vendor tools.
But that’s not necessarily the case.
Users can interface with EDA tools in a variety of ways, including:
- Native command shell (usually Tcl)
- Tool commands
- Direct database access (query, modification)
- GUI (sometimes menu customisation, sometimes GUI scripting interface)
- Reports (native, user-defined through scripting)
- Logs
Anyone who’s spent too much time with a tool has also run across some hidden (or private) settings and perhaps further, less documented interfaces with unusual naming styles. When a tool pulls the command side together into a more complete and consistent, documented interface, this becomes an Application Programming Interface (API).
The limiting factor in tool flow integration is often the quality, consistency and scope of the API and the inherent ability of the tool to support rapid surgical interventions on critical parts of a design – regardless of whether it’s a single or multi-vendor flow.
These are often determined in the initial tool architectural design when the core data structures and envisaged use models are considered (otherwise they’re shoehorned back in much later). As so often in engineering, it’s the interfaces that are critical. As these are so critical for point tools, they often get more attention. You soon learn what type of tool you have from the consistency of the interfaces (and single-vendor flows may not yet be quite as streamlined as we might assume).
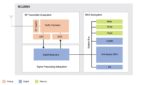
The white paper goes into more details about how this is implemented (Figure 1). Calibre functionality is added to a layout tool through both customisation of the GUI menus and a direct interface to the Calibre API through the layout tool scripting language.
Individual design groups can use an off-the-shelf Calibre integration (EDA vendors can do this through the Siemens EDA Partner Program) or quickly and easily fine tune an integration for their exact flow needs.
Putting this into practice, Calibre RealTime can provide on-demand signoff DRC checking with the signoff rule deck, giving designers a significant run time and productivity gain over running separate Calibre DRC checks.
Another application in use today is running Calibre SmartFill within the layout flow to get more accurate parasitics earlier in the flow.
Summary
There are many cases where design flows benefit from closer tool integration and we’ll likely need more and tighter interaction between what we used to think of as separate tools in a waterfall flow as we optimise design flows to run checks exactly where we want them, when we want them. But getting there requires determined efforts from EDA vendors improving tool usability with interfaces like APIs.
The Calibre RealTime interface shows what’s possible here. It’s being widely used in all major flows (Synopsys Fusion Compiler, Cadence Innovus and Virtuoso, as well as many others).
Find out more in the original white paper here:
Related Blogs and Podcasts
The Siemens EDA website contains a wealth of further material in white papers and videos:
https://eda.sw.siemens.com/en-US/ic/calibre-design/
This paper looks at the related importance of tool ease of use, again from a Calibre perspective:
You can also learn more about Calibre here:
https://www.youtube.com/@ICNanometerDesign
Also Read:
Cracking post-route Compliance Checking for High-Speed Serial Links with HyperLynx