Last Friday I attended a breakfast seminar organized by SEMI in Hillsboro, Oregon with fascinating speakers from several high-tech companies: Qorvo, Intel, Oregon Angel Fund, Kimera, Moonshadow Mobile and Yole Development. I recalled that Qorvo was created from the merger of TriQuint Semiconductor and RF Micro Devices back… Read More
 CEO Interview with Dr. Raj Gautam Dutta of Silicon AssuranceDr. Raj Gautam Dutta is the Co-Founder and…Read More
CEO Interview with Dr. Raj Gautam Dutta of Silicon AssuranceDr. Raj Gautam Dutta is the Co-Founder and…Read More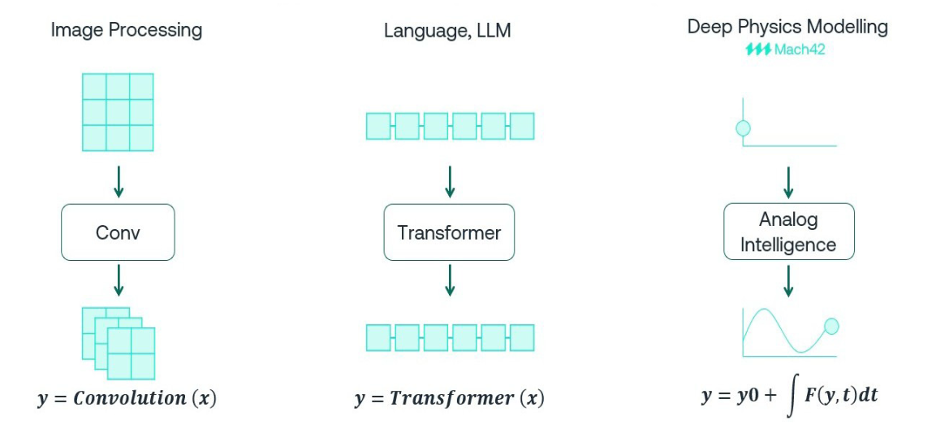 Beyond Transformers. Physics-Centric Machine Learning for AnalogPhysical AI is an emerging hot trend, popularly…Read More
Beyond Transformers. Physics-Centric Machine Learning for AnalogPhysical AI is an emerging hot trend, popularly…Read MoreScaling Enterprise Potential with ClioSoft’s designHUB platform
I’ve had the privilege over the years to be a part of a lot of great companies, teams and projects. Some of these efforts were quite successful while others were not. It begs the question of why is it so hard to enable design reuse and capture the untapped potential of the collective intelligence within our companies? Up till now, companies… Read More
Webinar – Next Generation DDRM Needs, Solutions
I’m a believer in product life-cycle management (PLM) for semiconductor design. It’s not an attention-grabbing topic like faster verification or improved PPA in implementation, but now massive IP-based design is routine, IP’s are sourced from multiple suppliers each cycling though multiple revisions and now that design … Read More
An Overview of Jama Software in the Semiconductor Industry
Portland, Oregon is a hotbed of innovation for software development companies and I tend to scan the headlines of my local newspaper the Oregonian, which is where I first started to read about Jama Software a few years back. Curiosity and opportunity drove me to meet with Trevor Smith of Jama in their Portland office. We chatted for… Read More
SEMICON Southeast Asia reflects strong equipment market
SEMICON Southeast Asia was held this week in Penang, Malaysia. Over 6500 people attended the conference to learn about the latest trends and equipment in semiconductor manufacturing.
Dr. Dan Tracy, Senior Director Industry Research and Statistics at SEMI, presented an optimistic outlook for the semiconductor equipment market… Read More
SPIE 2017 – imec papers and interview
At the SPIE Advanced Lithography Conference imec published a number of papers on EUV, multi-patterning and other lithography issues. In addition to seeing several of the papers presented I had a chance to sit down with imec’s director of advanced patterning, Greg McIntyre. In this article I will summarize my discussions… Read More
EDA CEO Outlook 2017
A long standing tradition has returned to EDA: The CEO Outlook sponsored by ESDA (formerly EDAC) which alone is worth the price of membership! Not only do you get a free meal, the event included quality networking time with the semiconductor elite. In the past, financial analysts moderated this event holding the CEO’s feet to the… Read More
IoT in the Cloud with Microsoft and Mentor
I cycle for fitness five days per week and use the Strava.com site to post my rides, analyze the ride data and chat with other cyclists, however in February this year the Amazon Web Services went down which crashed Strava, making me sad and nervous at the same time. Of course, there are alternatives to Amazon Web Services and the engineers… Read More
Lip-Bu on Opportunity
Given a chance to talk with someone as connected as Lip-Bu Tan (President and CEO of Cadence and Chairman of the VC firm Walden International), it is tempting to ask all the usual questions about industry growth and directions in cloud, automotive, IIoT, AI and so on. I wanted to try something different. If you make a living (or plan… Read More
Approaches for EM, IR and Thermal Analysis of ICs
As an engineer I’ve learned how to trade off using various EDA tools based on the accuracy requirements and the time available to complete a project. EDA vendors have been offering software tools to help us with reliability concerns like EM, IR drop and thermal analysis for several years now. Last week I attended a webinar … Read More

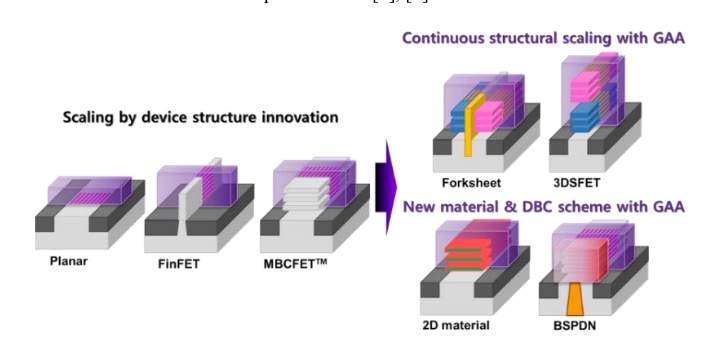






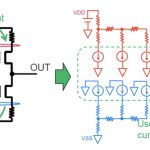
TSMC vs Intel Foundry vs Samsung Foundry 2026