I first met Jason Oberg, CEO and one of the co-founders of Tortuga Logic, several years ago when I was still at Atrenta. At that time Jason and Jonny Valamehr (also a co-founder and the COO) were looking for partners. The timing wasn’t right, but we’ve stayed in touch, for my part because their area of focus (security) is hot and likely… Read More
Webinar: RISC-V IoT Security IP
Disruptive technology and disruptive business models are the lifeblood of the semiconductor industry. My first disruptive experience was with Artisan Components in 1998. The semiconductor industry started cutting IP groups which resulted in a bubble of start-up IP companies including Artisan, Virage Logic, Aspec Technologies,… Read More
Semiconductor, EDA Industries Maturing? Wally Disagrees
Wally Rhines (President and CEO of Mentor, A Siemens Business) has been pushing a contrarian view versus the conventional wisdom that the semiconductor business, and by extension EDA, is slowing down. He pitched this at DVCon and more recently at U2U where I got to hear the pitch and talk to him afterwards.
What causes maturing is… Read More
5 Ways to Gain an Advantage over Cyber Attackers
Asymmetric attacks, like those in cybersecurity, benefit the aggressor by maintaining the ‘combat initiative’. That is, they determine who is targeted, how, when, and where attacks occur. Defenders are largely relegated to preparing and responding to the attacker’s tempo and actions. This is a huge advantage.… Read More
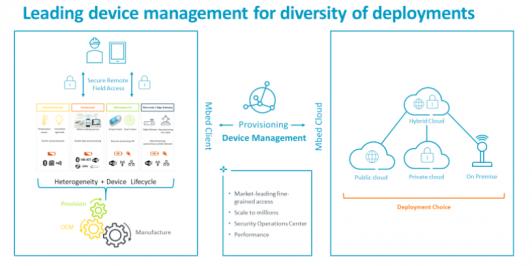
ARM IoT Mbed Update
Normally press release events with ARM tend to be somewhat arms-length – a canned pitch followed by limited time for Q&A. Through a still unexplained calendar glitch I missed a scheduled call for a recent announcement. To make up I had the pleasure of a 1-on-1 with Hima Mukkamala, GM of IoT cloud services at ARM. Hima is a heavy … Read More
Will the Rise of Digital Media Forgery be the End of Trust?
Technology is reaching a point where it can nearly create fake video and audio content in real-time from handheld devices like smartphones.
In the near future, you will be able to Facetime someone and have a real-time conversation with more than just bunny ears or some other cartoon overlay. Imagine appearing as a person of your … Read More
Data Breach Laws 0-to-50 States in 16 Years
It has taken the U.S. 16 years to enact Data Breach laws in each state. California led the way, with the first, in 2002 to protect its citizens. Last in line was Alabama, which just signed their law in March 2018. There is no overarching consistent data breach law at the federal level. It is all handled independently by each state. This… Read More
FlexE at SoC IP Days with Open Silicon
On Thursday April 5th the Design and Reuse SoC IP days continues in Santa Clara at the Hyatt Regency (my favorite hangout). SemiWiki is a co-sponsor and I am Chairman of the IP Security Track. More than 400 people have registered thus far and I expect a big turnout, if you look at the program you will see why. You should also know that registration… Read More
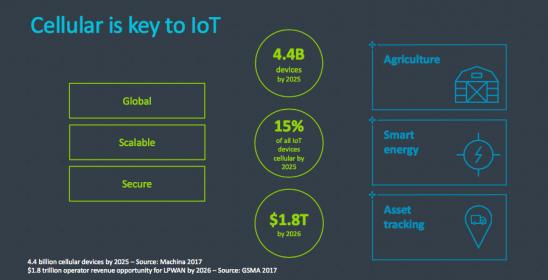
ARM and embedded SIM
It seems that a hot ticket at Mobile World Congress this year was embedded SIM announcements. As a reminder of why this space is hot, cellular communication for provisioning and data uploads is a very real option for many IoT devices. In agricultural, smart energy and asset tracking applications for example, near-range options… Read More
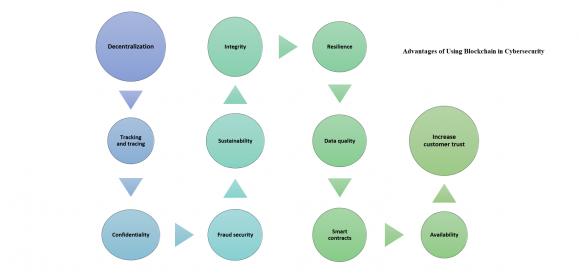
Second Line of Defense for Cybersecurity: Blockchain
In the first part we covered AI as the first line of defense for cybersecurity, the goal was to keep the cyber-criminals at bay, but in case they managed to get-in and infiltrate the network we need to initiate the second line of defense; #Blockchain. With the fact that cybercrime and cyber security attacks hardly seem to be out of the… Read More









Memory Matters: Signals from the 2025 NVM Survey