In the fast moving world of data communications, the appetite for high speed data transfers is accompanied by a growing need for data confidentiality and integrity. The wildly popular PCIe interface standard for connectivity has not only been increasing data transfer rates but has also introduced an Integrity and Data Encryption (IDE) security option. The introduction of IDE features in PCIe enables the processing of higher data bandwidths while encrypting the data to maintain its integrity.
Siemens EDA has a published a whitepaper that discusses the encryption flow used in IDE Transaction Layer Packets (TLPs) in PCIe and the underlying software stack. The paper explains how IDE ensures security against digital attacks on TLPs transferred from the transmitter to the receiver, including link-to-link connections and devices connected through switches. The TLPs are encrypted using keys exchanged during IDE key management. Furthermore, the whitepaper explains the underlying protocols used in IDE, including data object exchange (DOE), component measurement and authentication (CMA), and security protocol and data model (SPDM).
Data Object Exchange (DOE)
Data Object Exchange (DOE) in PCIe is an extended capability introduced to transfer various types of data objects between devices. Each vendor can define specific data objects, which are identified by a vendor ID assigned by PCI-SIG. Data are transferred as data objects, one double word (32-bits) at a time, forming packets through configuration write transactions in PCIe. The transmitting device sets the DOE go bit after sending the entire length of the data object. The receiving device consumes the data and begins forming a response. Once the response is ready, the receiving device sets the DOE data object ready bit in its configuration space. The transmitter reads the response one double word at a time until the data object ready bit is high. This process enables the transfer of data from one device to another.
Component Measurement and Authentication (CMA)
The Component Measurement and Authentication (CMA) feature in PCIe relies on the underlying Security Protocol and Data Model (SPDM) protocol. CMA utilizes the DOE feature to transfer packets for secure connection establishment. Within the CMA/SPDM framework, the authenticity of connected devices is verified using digital signatures and public key cryptography. This process ensures that the devices involved in the connection are genuine and trusted. Once the authenticity of the connected devices is established, a secure connection is formed between the requester and responder. The secure CMA/SPDM protocol is then utilized to transfer data objects securely. The data objects are transmitted using the negotiated algorithm that was employed during the establishment of the secure connection.
IDE Key Management
IDE key management is used to exchange keys that will be utilized to encrypt IDE TLPs. The process involves exchanging keys on a per sub-stream basis for both transmitting and receiving TLPs. There can be two sets of keys identified by the K bit in the IDE prefix, with each set containing different keys for the Tx and Rx directions. There are seven different types of packets involved in the IDE key management process, each identified by an object ID field. The full details are described in the whitepaper.
Integrity and Data Encryption (IDE)
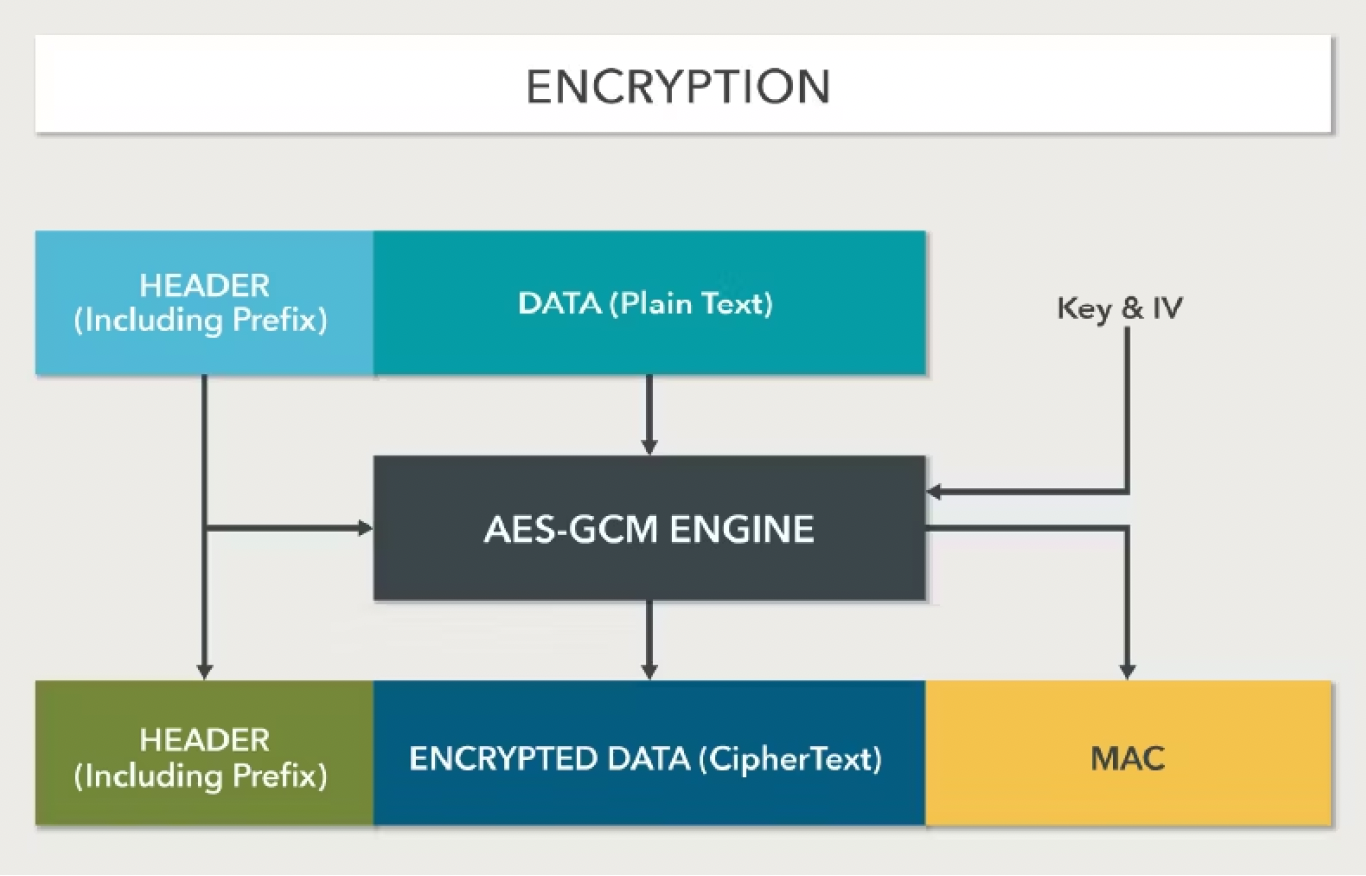
The goal of securing data transfers is to not only prevent unauthorized access but also to prevent tampering. Even with encryption, it is possible that attackers may be able to modify the data without the receiver’s knowledge unless there is a check for data integrity. The Message Authentication Code (MAC) feature of the IDE mechanism makes data integrity check possible. A secure state is achieved through the establishment of a secure connection using CMA/SPDM, configuration of keys using IDE key management, and enabling IDE by setting the IDE enable bit. The whitepaper goes into details of the transmit-receive data flow and the Advanced Encryption Standard-Galois/Counter Mode (AES-GCM) encryption/decryption process using keys and initialization vectors. Based on the MAC check, an IDE stream can be marked as being in secure state or insecure state. An IDE stream can transition from secure to insecure state if the security condition is compromised.

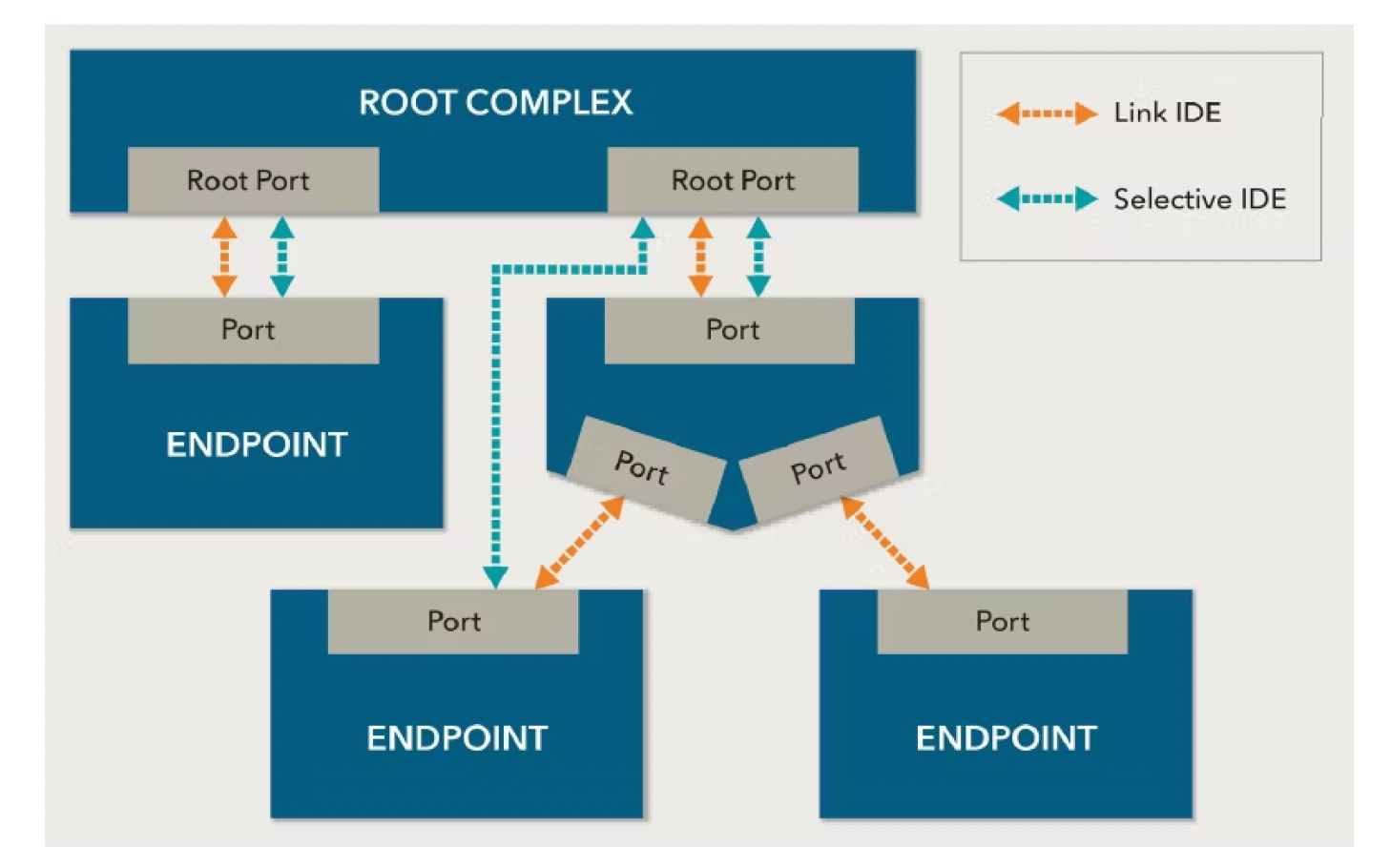
The IDE mechanism also provides flexibility in securing TLP transfers. The establishment of an IDE stream between two ports can be accomplished by connecting using Link IDE or Selective IDE. When a switch is present between the ports, selective IDE is used to encrypt the packets transferred between them. Link IDE and selective IDE can work independently or together for directly connected ports.
Verification of IDE Feature with Siemens EDA’s Questa VIP
Siemens QVIP serves as a comprehensive verification solution offering support for the entire IDE feature verification process. It includes stimulus generation, assertion checks, error injection capabilities, and extensive sequence libraries. The presence of debug and log features further enhances the efficiency and effectiveness of the verification process.
Summary
The whitepaper also goes into details of IDE TLP prefixes (M-bit, K-bit, T-bit and P-bit) and what purpose they serve. For example, the presence of the M bit in an IDE prefix indicates whether a MAC is present or not. The paper also covers TLP aggregation that allows multiple TLPs to be combined into a single unit for transmission for achieving increased throughput.
The whitepaper will be a valuable read for anyone involved in implementing data integrity and security for PCIe-based systems.
Also Read:
Emerging Stronger from the Downturn
Chiplet Modeling and Workflow Standardization Through CDX
Tessent SSN Enables Significant Test Time Savings for SoC ATPG
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.