Life is full of convenience-security tradeoffs. Sometimes these are explicit, where you get to make an active choice about how secure or insecure you want things to be. Other times we are unaware of the choices we are making, and how risky they are for the convenience provided. If you leave your bike unlocked, you can expect it to be… Read More
Tag: security
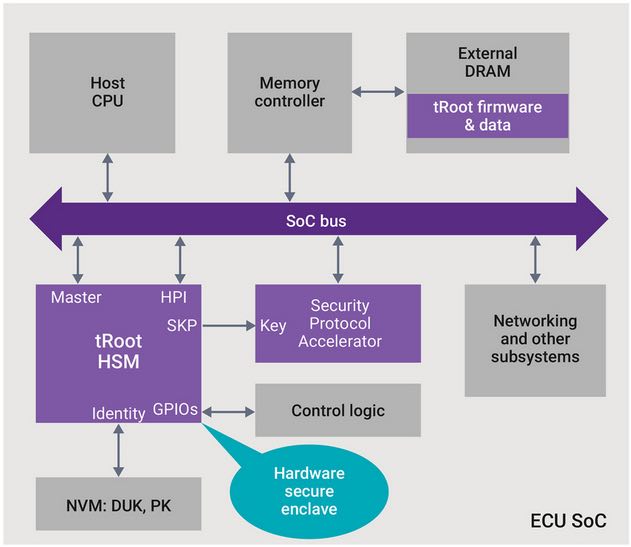
Car Vandals Eschew Crowbars
It used to be that automotive theft and crime was perpetrated with a crowbar. Now with increased electronics content, car designer and owners need to worry about electronic threats. Anywhere there is a communication link or a processor, there are potential threats to the security of the car. The range of these threats covers everything… Read More
Technology Transformation for 2019
Digital technology continues to connect and enrich the lives of people all over the globe and is transforming the tools of everyday life, but there are risks accompanying the tremendous benefits. Entire markets are committed and reliant on digital tools. The entertainment, communications, socialization, and many others sectors… Read More
IoT Security Process Variation to the Rescue
Unique device identities are at the core of all computer security systems. Just as important is that each unique identity cannot be copied, because once copied they can be used illegitimately. Unique device IDs are used to ensure that communications are directed to the correct device. And they also provide the ability to encrypt… Read More
Q4 Hiring remains strong Outlook for Q1 2019
Things are going quite well in the Valley, ESPECIALLY if traffic is any indication. I still remember the BUST with the empty office buildings and light traffic, back in the early 2000’s…while I wish for traffic like that always, I certainly prefer the busy times, guess you cannot have it all. The more traffic, the more jobs; they invariably… Read More
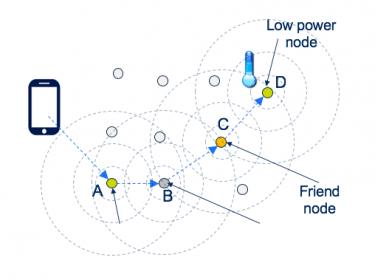
Mesh Networks, Redux
It isn’t hard to understand the advantage of mesh networking (in wireless networks). Unlike star/tree configurations in which end-points connect to a nearby hub (such as phones connecting to a conventional wireless access point), in a mesh nodes can connect to nearest neighbors, which can connect to their nearest neighbors… Read More
Data Management for SoCs – Not Optional Anymore
Design Management (DM) encompasses business decisions, strategies and processes that enable product innovations. It is the foundation for both effective collaboration and gaining competitive advantage in the industry. This also applies in the high-tech space we are in, as having a sound underlying SoC data management for… Read More
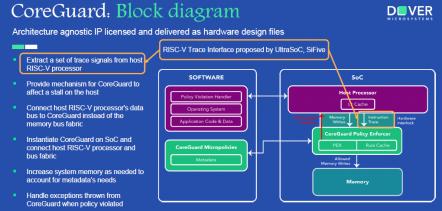
RISC-V Ready (Tools) Set (Security) Go (Build)
The second Bay Area RISC-V Meetup event was held at the DoubleTree Hilton in Burlingame on June 19 with about 150 attendees. This event was hosted by SiFive and started with a networking session. The topics and speakers for the evening were:
- Commercial Software Tools – Larry Lapides, Imperas
- Securing RISC-V Processors –
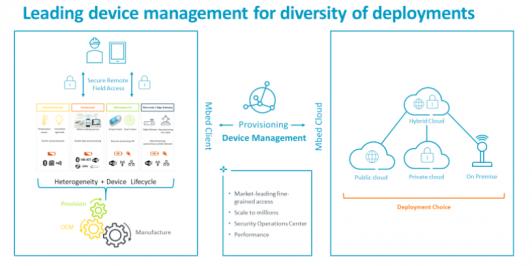
ARM IoT Mbed Update
Normally press release events with ARM tend to be somewhat arms-length – a canned pitch followed by limited time for Q&A. Through a still unexplained calendar glitch I missed a scheduled call for a recent announcement. To make up I had the pleasure of a 1-on-1 with Hima Mukkamala, GM of IoT cloud services at ARM. Hima is a heavy … Read More
CEVA and Local AI Smarts
When we first started talking about “smart”, as in smart cars, smart homes, smart cities and the like, our usage of “smart” was arguably over-generous. What we really meant was that these aspects of our daily lives were becoming more computerized and connected. Not to say those directions weren’t useful and exciting, but we weren’t… Read More