SoCs face a lot of issues related to security and the Network-on-Chip (NoC) is in a good position to facilitate system-wide services. SoCs are now so complex that one of the challenges is to make sure that the chip does what it is meant to do and doesn’t do what it isn’t meant to do. Just as in software, security used to be … Read More
Tag: security
Somebody at the NSA has a sense of humor
We have to go way back in the annals of entertainment history to find the origin of the word “Jeep”, not just a term of endearment hung on a WWII utility vehicle. Pictured is Eugene the Jeep, a mystical creature belonging to the 4th Dimension, who first appeared to torment Popeye the Sailor in 1936.… Read More
Security Path Verification
Formal approaches and security are a perfect match since you really want to prove that there are no holes in your security, rather than just being fairly confident. At the recent Jasper User Group meeting, Victor Purri presented some case studies in security verification.
The Jasper Security Path Verification (SPV) App is used… Read More
New at DAC: IP, Automotive, Security
The deadline for panel sessions, workshops, tutorials and co-located conferences for DAC 2014 is October 21st. That’s next Monday!
DAC 2014 will not only focus on EDA and embedded systems and software but
also include:
- design methods for automotive systems and software
- hardware and embedded systems security
- IP (semiconductor
Security Needs in On-Chip Networks
I remember during my first ten years as a software developer, I used many different computers such as IBM mainframes, Apollo and Sun workstations, and VAX computers. During that time I also bought my first home computer, a Macintosh. I didn’t of course think of this at the time, but the one thing they all had in common was that they did… Read More
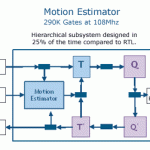
What Applications Implement Best with High Level Synthesis?
RTL coding using languages like Verilog and VHDL have been around since the 1980’s and for almost as long a time we’ve been hearing about High Level Synthesis, or HLS that allows an SoC designer to code above the RTL level where you code at the algorithm level. The most popular HLS languages today are C, C++ and SystemC.… Read More
Call for Papers: International Gathering for Application Developers!
SemiWiki would like to call you, your co-workers, and your company to participate at ERSA Conference in Las Vegas , July 16-19, 2012. I will be there and it would be a pleasure to work with you on this very important event!
ERSA, is Engineering of Reconfigurable Systems and Algorithms. Since this year, the emphasis will be on the commercial… Read More
Imera Virtual Fabric
Virtual fabric sounds like something that would be good for making the emperor’s new clothes. I talked today to Les Spruiell of Imera to find out what it really is.
Anyone who has worked as either a designer or as an EDA engineer has had the problem of a customer who has a problem but can’t send you the design since it is (a)… Read More