The Netherlands has been the home for Hardwear.io since 2015.
We are very excited to host the industry from automotive, healthcare, semiconductor, IoT, industrial control systems and Govt/Defences Institutes to join us for Hardwear.io NL scheduled on 17th Nov to 21st Nov 2025 at Amsterdam Marriott Hotel
Learn, share, build,… Read More
The 34th USENIX Security Symposium will take place on August 13–15, 2025, at the Seattle Convention Center in Seattle, WA, USA. The USENIX Security Symposium brings together researchers, practitioners, system programmers, and others interested in the latest advances in the security and privacy of computer systems and networks.… Read More
Featured Speakers:
- Mike Borza, Scientist and Principal Security Technologist, Synopsys
- Dana Neustadter, Senior Director of Product Management, Synopsys
As AI systems become increasingly vital across industries, ensuring their security and integrity is more critical – and challenging – than ever.
Join Synopsys in this … Read More
DAC 2025by Admin on 05-12-2025 at 5:52 pm
About DAC
DAC is recognized as the global event for chips to systems. DAC offers outstanding training, education, exhibits and superb networking opportunities for designers, researchers, tool developers and vendors. The conference is sponsored by the Association for Computing Machinery (ACM) and the Institute of Electrical… Read More
RSAC 2025by Admin on 01-27-2025 at 3:09 pm
Unite. Innovate. Shine. Join the RSAC 2025 Community.
At RSAC 2025, you’re not just attending a conference—you’re stepping into a vibrant, thriving community of thinkers, innovators, and achievers. Though we come from different corners of the cybersecurity world, we are united by a common mission: to foresee … Read More
The moral of today’s story is that to succeed in a late-adopter market, sometimes you just have to wait for the market to catch up (assuming you have a strong early adopter market to buy your product today). I have been working with Arteris for 6+ years now promoting their NoC technology, and there was never any question that they offer… Read More
Mixed-signal and analog design are key aspects of modern electronics. Every chip incorporates some form of analog IP, as even digital logic is dependent on analog signals for critical functions. Many digital design engineers are known to be uncomfortable with the prospect of integrating analog components. However, the current… Read More
Semiconductor intellectual property (IP) plays a critical role in modern system-on-chip (SoC) designs. That’s not surprising given that modern SoCs are highly complex designs that leverage already proven building blocks such as processors, interfaces, foundational IP, on-chip bus fabrics, security IP, and others. This… Read More
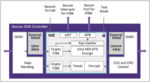
Security threats are a hot topic of discussion today as they can have a profound impact on the electronic infrastructure and devices that are the backbone of our global economies. It is also clear that these threats can be introduced during the design of the very devices that we rely on in our daily lives.
Chiplet-based design is … Read More
News of hackers breaking into systems is becoming common place these days. While many of the breaches reported to date may have been due to security flaws in software, vulnerabilities exist in hardware too. As a result, the topic of security is getting increased attention within the semiconductor industry around system-on-chip… Read More