Rapid advances in medical technology prolong patients’ lives and provide them with a higher standard of living than years past. But the increased interconnectivity of those devices and their dependence on wired and wireless networks leave them susceptible to cyberattacks that could have severe consequences.
Whether… Read More
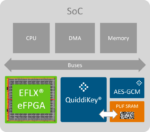
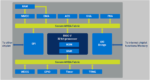
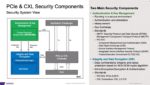
We have written about eFPGA and for six years now and security even longer so it is natural to combine these two very important topics. Last month we covered the partnership between Flex Logix and Intrinsic ID, and the related white paper. Both companies are SemiWiki partners, so we were able to provide more depth and color:
In the … Read More
While the ASIC market has always had its advantages over alternate solutions, it has faced boom and bust cycles typically driven by high NRE development costs and time to market lead times. During the same time, the FPGA market has been consistently bringing out more and more advanced products with each new generation. With very… Read More
Moving deep learning from the cloud to the edge is the holy grail when it comes to deploying highly accurate, low-power applications. Market demand for edge AI continues to grow globally as new hardware and software solutions are now more readily available, enabling any sized company to easily implement deep learning solutions… Read More
Discussions of chiplets has been on the rise, ever since the slowdown of Moore’s law benefits. Gartner Research projects semiconductor revenue from systems using chiplets to grow from $3.3 billion in 2020, to $50.5 billion in 2024. With any market opportunity, there are always challenges to overcome in order to realize the full… Read More
Remember when a pair of ethical hackers remotely took over a Jeep Cherokee as it was being driven on a highway near downtown St. Louis back in 2015? The back story is, those “hackers,” security researchers Charlie Miller and Chris Valasek, approached vehicle manufacturers several years before their high-profile feat, warning… Read More
Privacy and security have always been a concern when it comes to computing. In prior decades for most people this meant protecting passwords and locking your computer. However, today more and more users are storing sensitive data in the cloud, where it needs to be protected at rest and while in motion. In a Synopsys webinar Dana Neustadter,… Read More
Dan is joined by Dr. Alric Altoff, senior hardware security engineer at Tortuga Logic. The security risks associated with speculative execution are discussed along with scalable methods to address these risks.
Dr. Alric Altoff has over 15 years of experience in hardware security, hardware/software co-design, and applied … Read More
As I read both the popular and technical press each week I often see articles about computer systems being hacked, and here’s just a few vulnerabilities from this week:
…
Read More