News of hackers breaking into systems is becoming common place these days. While many of the breaches reported to date may have been due to security flaws in software, vulnerabilities exist in hardware too. As a result, the topic of security is getting increased attention within the semiconductor industry around system-on-chip (SoC) and high-speed data interfaces. The goal is to make sure that data that moves across these interfaces is protected from being accessed or manipulated by unauthorized agents.
One type of interface that is proliferating rapidly is related to memories. High-bandwidth interfaces such as DDR continue to increase in transfer speeds with every new generation. It is imperative to secure off-chip dynamic random-access memory (DRAM) interfaces which are vulnerable to certain types of attacks. With increasingly complex systems, securing data should be an integral part of hardware design.
DRAM-specific Vulnerabilities
DRAM-specific vulnerabilities include Row hammer, RAMBleed, and cold-boot attacks. Row hammer attacks are executed by repeatedly reading data in a memory row at high speed. This activity causes bits in adjacent rows to flip, enabling the attacker to gain read-write access to the entire physical memory. RAMBleed uses the same principles as Row hammer but reads the information instead of modifying it to extract information from DRAM, thus threatening the confidentiality of the data stored in memory. With cold-boot attacks, attackers can reset a system, access pre-boot physical memory data to retrieve encryption keys and cause damage. The consequences of these attacks can be severe including identity theft, fraud, financial losses, and the liability expenses to clean up the damage. The attacks can compromise the overall system and its data, resulting in significant reputational damage as well.
Securing Against Above Vulnerabilities
Encryption prevents Row hammer attacks by making it more difficult for an attacker to gain access to physical memory locations. Encrypted data is more difficult to manipulate since it is not in its original form, which makes it harder for the attacker to create a Row hammer attack. Furthermore, authentication, can be used to protect the integrity of data, which makes it more difficult for an attacker to alter the contents of memory locations. Authentication can also be used to ensure controlled access to specific memory locations, which can help in preventing unauthorized access.
To safeguard memory interfaces by design, designers can turn to high-performance, low-latency memory encryption solutions, such as AES-XTS based encryption that can be augmented with cryptographic hashing algorithms, to address both the confidentiality and integrity of data. Encryption covers all the bits, making it nearly impossible to create Row hammer patterns. Refreshing keys and memory encryption can also protect against RAMBleed and cold-boot attacks.
Challenges
Implementing memory encryption comes with a cost, including overhead that impacts power, performance, area (PPA), and latency. Designers must consider the tradeoffs and ensure that security is integrated into the design from the beginning. It is critical for keys to be generated and managed in a trusted/secure area of the SoC and distributed via dedicated channels to the encryption module. Control configuration and readback protection of keys should also be part of the overall security architecture.
Optimal Solution Strategy
DDR and LPDDR interfaces would benefit from inline memory encryption (IME) security just as PCI Express® (PCIe®) and Compute Express Link (CXL) interfaces benefitted from integrity and data encryption (IDE). The IME solution should tightly couple the encryption/decryption inside the DDR or LPDDR controller, allowing for maximum efficiency of the memory and lowest overall latency. The solution should also allow for ongoing adaptation of an ever evolving security threat.
Figure: Secure DDR5 Controller with Inline Memory Encryption (IME)
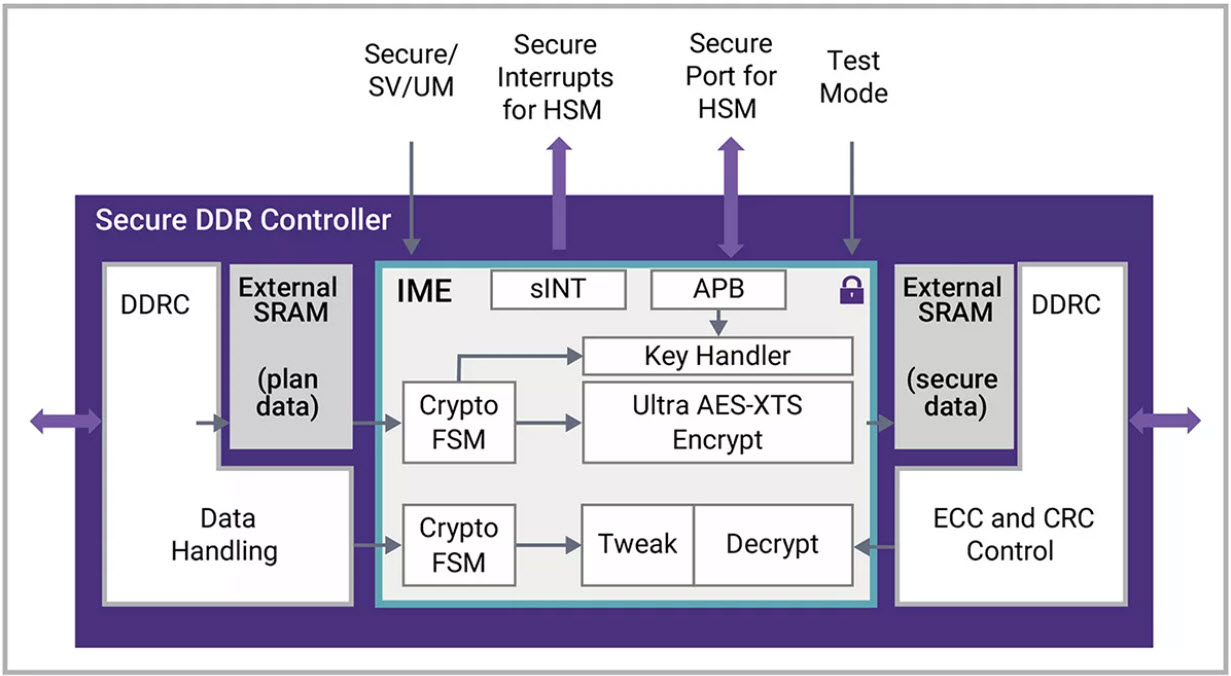
IME Security Module for DDR/LPDDR
Synopsys IME Security Module provides data confidentiality for off-chip memory over DDR/LPDDR interfaces, supporting both write and read channels with AES-XTS encryption. It seamlessly integrates with Synopsys DDR/LPDDR controllers, reducing risk and accelerating SoC integration with ultra-low latency of just two cycles. The module is scalable, FIPS 140-3 certification ready, and supports different datapath widths, key sizes, and encryption modes. It also offers efficient key control, SRAM zeroization, and mission mode bypass. With its standalone or integrated solution, the IME Security Module provides optimal PPA and latency for secure and compliant SoC designs.
For more details, refer to Synopsys IME Security Module page.
Summary
Incorporating security into SoCs is a fundamental requirement for fulfilling privacy and data protection requirements of electronic systems users. Securing the high-speed interfaces is key to addressing this requirement. The deployed mechanisms need to be highly efficient with optimal latency. Authentication and key management in the control plane and integrity and data encryption in the data plane are essential components of a complete security solution. Synopsys provides complete solutions to secure SoCs, their data, and communications.
Also Read:
Power Delivery Network Analysis in DRAM Design
Intel Keynote on Formal a Mind-Stretcher
Multi-Die Systems Key to Next Wave of Systems Innovations
Share this post via:





Comments
3 Replies to “Securing Memory Interfaces”
You must register or log in to view/post comments.