Methbot is a state-of-the-art ad fraud infrastructure, capable of hosting legitimate videos and serving them to 300 million fake viewers a day. Each view earns the criminals about $13, translating to around four million dollars a day. Over the past few months, Methbot has pulled in an estimated $180 million. It represents one … Read More
 EDA Has a Value Capture Problem — An Outsider’s ViewBy Liyue Yan (lyan1@bu.edu) Fact 1: In the…Read More
EDA Has a Value Capture Problem — An Outsider’s ViewBy Liyue Yan (lyan1@bu.edu) Fact 1: In the…Read More WEBINAR: How PCIe Multistream Architecture is Enabling AI ConnectivityIn the race to power ever-larger AI models,…Read More
WEBINAR: How PCIe Multistream Architecture is Enabling AI ConnectivityIn the race to power ever-larger AI models,…Read More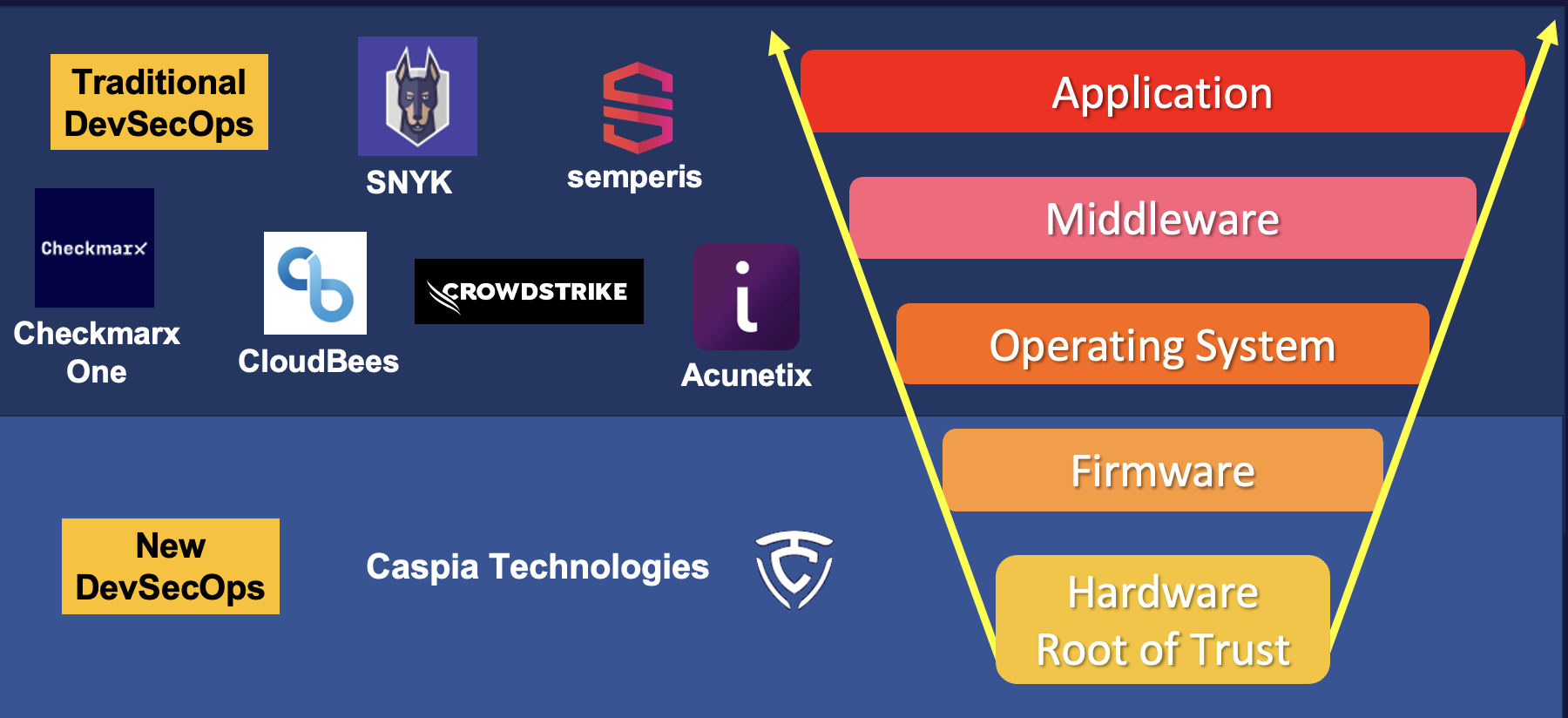 A Six-Minute Journey to Secure Chip Design with CaspiaHardware-level chip security has become an important topic…Read More
A Six-Minute Journey to Secure Chip Design with CaspiaHardware-level chip security has become an important topic…Read More Lessons from the DeepChip Wars: What a Decade-old Debate Teaches Us About Tech EvolutionThe competitive landscape of hardware-assisted verification (HAV) has…Read More
Lessons from the DeepChip Wars: What a Decade-old Debate Teaches Us About Tech EvolutionThe competitive landscape of hardware-assisted verification (HAV) has…Read More Think Quantum Computing is Hype? Mastercard Begs to DisagreeJust got an opportunity to write a blog…Read More
Think Quantum Computing is Hype? Mastercard Begs to DisagreeJust got an opportunity to write a blog…Read MoreAI vs AI
You might think that one special advantage of AI systems is that they should be immune to attacks. After all, their methods are so complex and/or opaque that even we can’t understand how they work, so what hope would a hacker have in challenging these systems? But you would be mistaken. There’s nothing hackers like better than a challenge.… Read More
IBM Demonstrates Blockchain Progress and Clients
IBM must have laid off its lawyers or something since never before has the company seemed so ready to reveal clients by name and the projects they’re engaged in. That has been going on for months and recently it has accelerated. Credit IBM’s eagerness to get blockchain established fast and show progress with the open community HyperLedger… Read More
NetSpeed Bridges the Gap Between Architecture and Implementation
This is part II of an article covering NetSpeed’s network-on-chip (NoC) offerings. This article dives a little deeper into what a NoC is and how NetSpeed’s network synthesis tool, NocStudio, helps system architects optimize a NoC for their system-on-a-chip (SoC) design.
Traditionally IC designers have used proprietary buses,… Read More
They Kill Pedestrians, Don’t They?
I came upon the scene of a crash investigation yesterday afternoon in my hometown of Herndon, Va. A mother and two children were hit by a 20-year-old motorist making a right turn at an intersection. I did not see the crash, but I strongly suspect the motorist was looking left to anticipate oncoming traffic and never noticed the pedestrians… Read More
Solving a Murder Case with IoT Devices
I watch a lot of Netflix and there are so many detective movies and series for me to enjoy where I try and match wits with the bad guys and figure out who is guilty a few seconds before the law enforcement characters do. On TV and with our movies there is often critical evidence extracted from desktop computers, laptops, hard drives, smart… Read More
3 Tips for Securing Home Cameras
Installing a home surveillance camera system can add great benefits but also may introduce new risks to privacy and network security. The goal is to increase the security and peace of mind, while avoiding cybersecurity threats. Here are three tips to consider when purchasing, installing, and configuring your new home camera … Read More
The 2017 Leading Edge Semiconductor Landscape
In early September of 2016 I published an article “The 2016 Leading Edge Semiconductor Landscape” that proved to be very popular with many views, comments and reposting’s. Since I wrote that article a lot of new data has become available enabling some projections to be replaced by actual values and new analysis… Read More
IoT and a few of my favourite things
I was at the 27th Hewlett Packard Colloquium on Information Security at Royal Holloway, University of London this week and met Alan Stockey of RiskingIT.com. Alan told me about a little ditty he wrote on IoT security to the tune of “My Favourite Things” from the Sound of Music. Amused me and he’s allowed me to share… Read More
Intel Spreadtrum ARM SoCs
In June of 2013 Edward Snowden copied and leaked classified information from the National Security Agency (NSA). His actions exposed numerous surveillance programs that many governments around the world reacted to, including China. In September of 2013 China Vice Premier Ma Kai declared semiconductors a key sector for the … Read More


AI RTL Generation versus AI RTL Verification