The second Bay Area RISC-V Meetup event was held at the DoubleTree Hilton in Burlingame on June 19 with about 150 attendees. This event was hosted by SiFive and started with a networking session. The topics and speakers for the evening were:
- Commercial Software Tools – Larry Lapides, Imperas
- Securing RISC-V Processors –



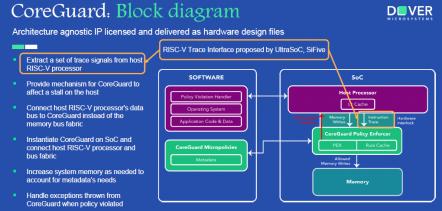
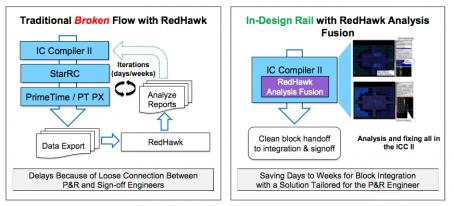


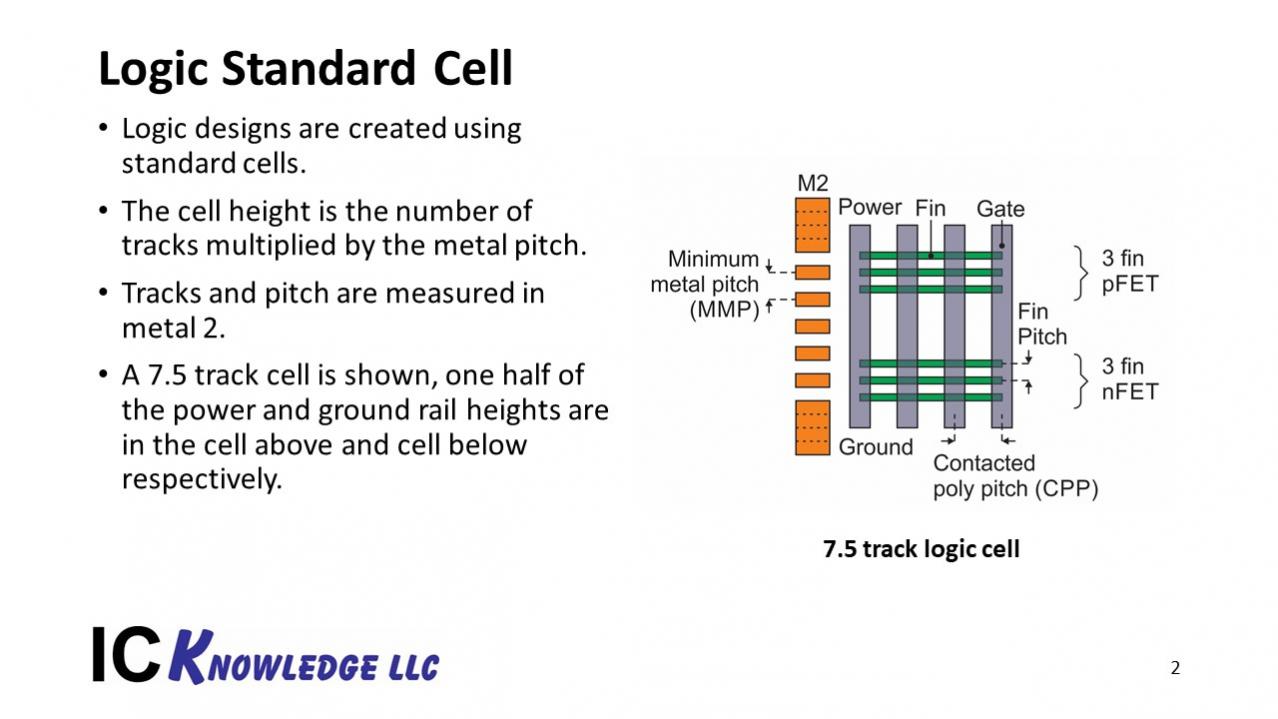



A Century of Miracles: From the FET’s Inception to the Horizons Ahead