The rate of product development is facing very real challenges as the pace of silicon technology evolution begins to slow. Today, we are squeezing the most out of transistor physics, which is essentially derived from 60-year-old CMOS technology. To maintain the pace of Moore’s law, it is predicted that in 2030 we will need transistors… Read More
 TSMC’s CoWoS® Sustainability Drive: Turning Waste into WealthIn a significant example of how high-tech manufacturing…Read More
TSMC’s CoWoS® Sustainability Drive: Turning Waste into WealthIn a significant example of how high-tech manufacturing…Read More Taming Advanced Node Clock Network Challenges: Duty CycleAs process nodes advance, circuit behavior becomes progressively…Read More
Taming Advanced Node Clock Network Challenges: Duty CycleAs process nodes advance, circuit behavior becomes progressively…Read MoreAn Important Step in Tackling the Debug Monster
If you’ve spent any time at all in the semiconductor industry, you’ve heard the statement that verification consumes two-thirds or more of the total resources on a chip project. The estimates range up to 80%, in which case verification is taking four times the effort of the design process. The exact ratio is subject to debate, but… Read More
Navigating Memory Choices for Your Next Low-Power Design
Choosing a memory architecture can be a daunting task. There are many options to choose from, each with their own power, performance, area and cost profile. The right choice can make a new design competitive and popular in the market. The wrong choice can doom the whole project to failure.
Vadhiraj Sankaranarayanan, senior technical… Read More
Mentor Helps Mythic Implement Analog Approach to AI
The entire field of Artificial Intelligence (AI) has resulted from what is called “first principles thinking”, where problems are re-examined using a complete reassessment of the underlying issues and potential solutions. It is a testament to how effective this can be that AI is being used for a rapidly expanding number of applications… Read More
Thermal Issues and Solutions for 3D ICs: Latest Updates and Future Prospect
At DesignCon 2020, ANSYS held a series of sponsored presentations. I was able to attend a couple of them. These were excellent events with the material delivered by talented and high-energy speakers. The DesignCon technical program has many dimensions beyond the conference tracks. One of the presentations dealt with 3D ICs.… Read More
Hybrid Verification for Deep Sequential Convergence
I’m always curious to learn what might be new in clock domain crossing (CDC) verification, having dabbled in this area in my past. It’s an arcane but important field, the sort of thing that if missed can put you out of business, but otherwise only a limited number of people want to think about it to any depth.
The core issue is something… Read More
Webinar – FPGA Native Block Floating Point for Optimizing AI/ML Workloads
Block floating point (BFP) has been around for a while but is just now starting to be seen as a very useful technique for performing machine learning operations. It’s worth pointing out up front that bfloat is not the same thing. BFP combines the efficiency of fixed point operations and also offers the dynamic range of full floating… Read More
Build Custom SoC Assembly Platforms
I’ve talked with Defacto on and off for several years – Chouki Aktouf (CEO) and Bastien Gratreaux (Marketing). I was in a similar line of business back in Atrenta. Now I’m just enjoying myself, I’ve written a few blogs for them. I’ll confess I wondered why they wouldn’t struggle with the same problems we’d had. Script-driven RTL editing,… Read More
China Chip Equip Embargo just got real
Worst Case Scenario now possible!
- Embargo could extend beyond China to Taiwan (TSMC)
- Likely backs up ASML pressure & Huawei indictment
- “Maximum Pressure” campaign similar to Iran
- Not likely to go away through trade negotiations
US to restrict chip equipment sales to Huawei producers
The Wall Street Journal… Read More
Semiconductor Recovery in 2020?
Semiconductors down 12% in 2019
World Semiconductor Trades Statistics (WSTS) reported the world semiconductor market in 2019 was $412 billion, a 12.1% decline from $469 billion in 2018. Most of the decline was in the memory market (primarily DRAM and Flash) which was down a third from a year ago. However overall semiconductor … Read More


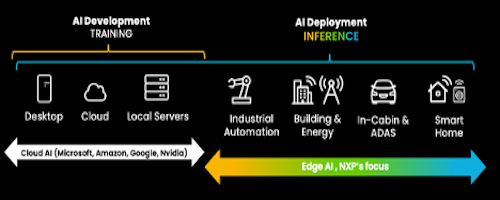







Website Developers May Have Most to Fear From AI