Integrated circuits, or chips, lie at the heart of today’s electronic systems that are mission critical for almost every sector of the economy – from healthcare, to banking, military equipment, cars, planes, telecommunications, and the internet itself. The data flowing through these systems is the lifeblood of modern life and we go to great lengths to protect it from unauthorized access.
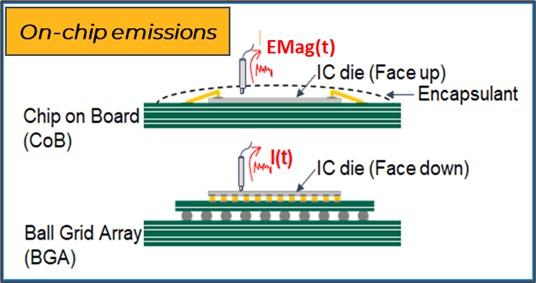
We are all familiar with security passwords, PIN codes, and two-factor authentication that aim to secure electronic systems against code viruses and software vulnerabilities. But there is also a completely different category of hacking vulnerabilities that are rooted in hardware, not software. This area of hardware security seeks to prevent unauthorized leakage of critical information carried out by so-called “side-channel attacks”. A side-channel can be any physical phenomenon that can be exploited to reveal the internal workings of a chip. Some of the most common side-channels are power noise, electromagnetic radiation, and thermal.
Power noise refers to the changes in power supply current drawn by a chip as it executes different instructions. By monitoring how much the supply current goes up and down it is possible to reveal a cryptographic key embedded in the chip. Similarly, an electromagnetic probe hovering a few millimeters above the surface of a chip can detect the switching activity of internal signals. Thermal side-channel attacks monitor the amount and location of heat produced by the chip. These are all examples of hardware security vulnerabilities that can be used to reveal secure data and cryptographic keys. A side-channel attack leaves no trace that the data has been compromised and may not even require any physical contact with the chip. It also cannot be defended against with traditional software security techniques.
Much of our modern infrastructure relies on cryptography to secure data storage and communication. The internet has moved to secure “https://” website addresses; credit card and online banking transactions are secured with encryption in silicon; healthcare data is kept confidential with encryption; and military units rely on encryption to communicate on the battlefield. Hardware security vulnerabilities have already been exploited in the real world with examples ranging from the cloning of car fobs to identified microprocessor security vulnerabilities called ‘Meltdown’, ‘Spectre’, and ‘Platypus’. Data security has become a pervasive concern for many leading companies and semiconductor designers are eager to strengthen their chips against hardware vulnerabilities.
Traditionally, side-channel vulnerabilities have been measured and evaluated in a lab by examining the actual device. While accurate and reliable, lab testing is expensive and slow and – most importantly – it is closing the barn door after the horse has bolted. There is no way to fix any detected vulnerability! Often millions of dollars have already been spent on creating photomasks and the chip has been manufactured. Any fixes will require an expensive redesign, more money for new photomasks, and months of extra delay. It would be better to be able to simulate and predict side-channel vulnerabilities at the design stage before manufacturing. Simulation is faster, cheaper, and more flexible than actual physical measurements. It requires less operator expertise, and it can point the way to improving and safeguarding the design before any money is spent on manufacturing.
Ansys and eShard Technologies are both leading experts in hardware security and have announced an agreement to collaborate to deliver a comprehensive solution that includes both pre-silicon and post-silicon security verification. eShard is a leading provider of chip security testing with the esDynamic™ testing platform for side-channel testing, fault injection, and failure analysis. With dozens of customers, including major semiconductor companies, eShard is able to deploy proven algorithms for verifying many advanced security algorithms, including AES, RSA, ECC, and HMAC. esDynamic has algorithms to efficiently evaluate the security for these standards in physical hardware and generate relevant metrics for the strength of the security implementation.
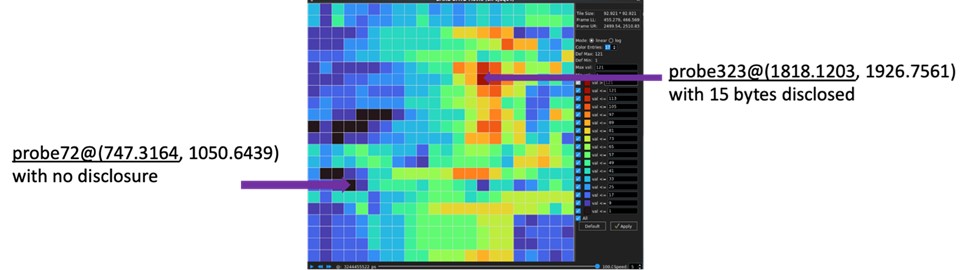
eShard’s agreement with Ansys allows Ansys RedHawk-SC Security™ to perform the same extensive suite of cryptographic analyses at the pre-silicon design stage and flag potential areas of weakness. RedHawk-SC Security is built on the foundry-certified Ansys RedHawk-SC™ golden signoff tool for power integrity analysis of digital chips. RedHawk-SC Security simulates pre-silicon layouts with Ansys’s industry-leading physics simulation engines for electromagnetic and power noise analysis. These pre-silicon predictions cover all anticipated usage modes by combining user-generated activity vectors, automatic ‘vectorless’ activity, and real-world activity based on actual software execution. RedHawk-SC Security ties into esDynamic’s platform for management of the entire security verification workflow.
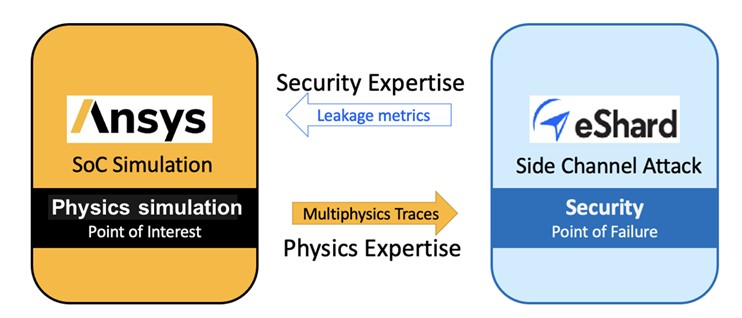
The collaboration brings together eShard’s expertise in security with Ansys’s foundry-certified expertise in physical simulation to deliver a uniquely broad and capable hardware security solution. This collaboration offers the joint advantages of pre-silicon simulation for fast, cost-effective problem avoidance, and post-silicon verification for the most reliable accuracy. Customers can now deploy an integrated solution platform that gives regular chip designers at all stages in the design flow – from RTL to layout – the expertise to verify a comprehensive suite of security protocols. This easy-to-use workflow and deliver proven levels of hardware security at every stage of semiconductor product development.
Marc Swinnen, Director of Product Marketing – Semiconductors Ansys
Also Read:
Ansys and NVIDIA Collaboration Will Be On Display at DAC 2024
Don’t Settle for Less Than Optimal – Get the Perfect Inductor Every Time
Simulation World 2024 Virtual Event
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.