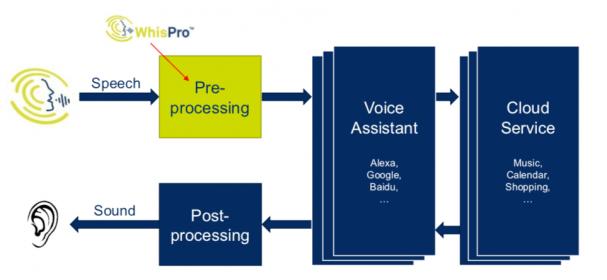
In the superheated world of AI and Neural Nets (NN), many of us are familiar with object recognition in images: cars, pedestrians, cats and dogs and thousands of other applications. But there’s another class of applications, also growing rapidly, around audio AI. Early generations for command recognition in infotainment systems… Read More
Semiconductor Intellectual Property
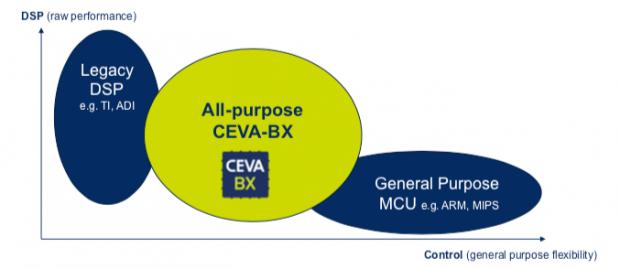
CEVA-BX: A Hybrid DSP and Controller
I’ve noticed hybrid solutions popping up recently (I’m reminded of NXP’s crossover MCU released in 2017). These are generally a fairly clear indicator that market needs are shifting; what once could be solved with an application processor or controller or DSP or whatever, now needs two (or more) of these. In performance/power/price-sensitive… Read More
IoT Devices Can Kill and What Chip Makers Need to Do Now
After the onslaught of IoT devices Christmas brought to the masses we really need to talk about security or lack thereof. Do me a favor and count how many IoT devices you have now? Our house IoT count is probably a bit higher than average due to my technology addiction but we are firmly in the double digits and the security breach stories… Read More
Disturbances in the AI Force
In the normal evolution of specialized hardware IP functions, initial implementations start in academic research or R&D in big semiconductor companies, motivating new ventures specializing in functions of that type, who then either build critical mass to make it as a chip or IP supplier (such as Mobileye – intially)… Read More
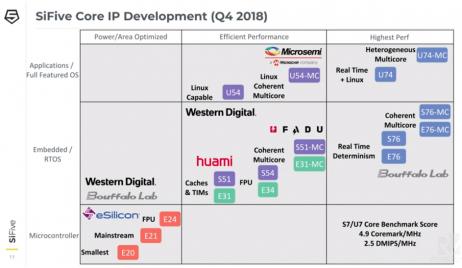
You Will Not Get Fired for Choosing RISC-V
These were the closing words Yunsup Lee, CTO, SiFive used at one of the December RISC-V Summit Keynotes entitled ‘Opportunities and Challenges of Building Silicon in the Cloud’. Fired up was more the mood among the 1000+ attendees of the RISC-V Summit held at the Santa Clara Convention Center and SiFive was among the companies showcasing… Read More
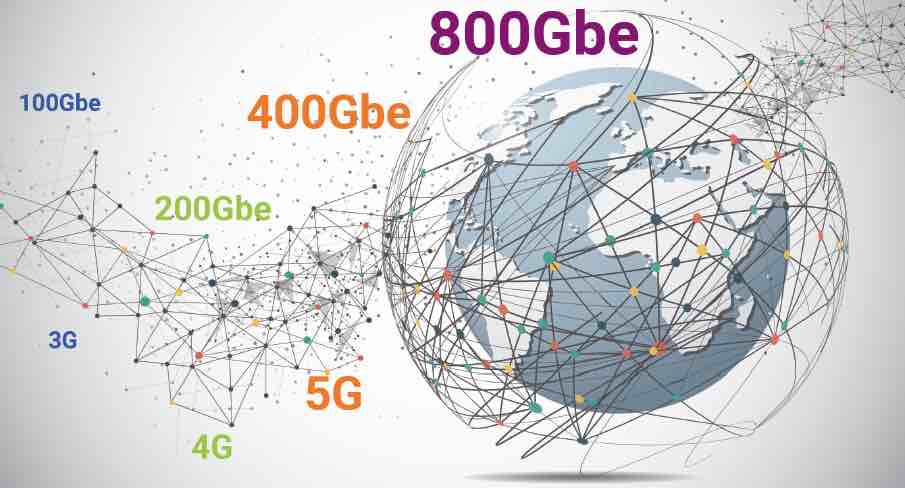
Ethernet Enhancements Enable Efficiencies
Up until 2016, provisioning Ethernet networks was a little bit like buying hot dogs and hot dog buns, in that you could not always match up the quantities to get the most efficient configuration. That dramatically changed when the specification for Ethernet FlexE was adopted by the Optical Internetworking Forum as OIF-FLEXE-01.0.… Read More
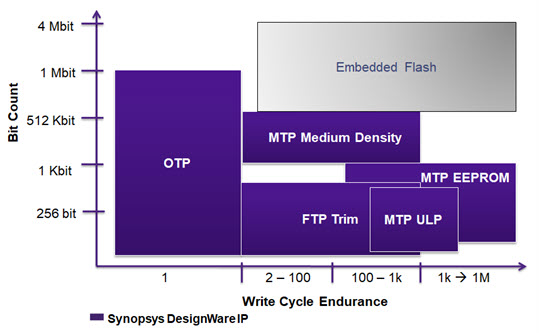
Synopsys Offers Smooth Sailing for OTP NVM
Nobody likes drama. Wait, let me narrow that down a bit. Chip designers really hate drama. They live in a world of risk and uncertainty, a world that tool and IP vendors spend considerable resources trying to make safer and more rational. It’s notable just how ironic that Sidense and Kilopass were duking out patent litigation in the… Read More
AI at the Edge
Frequent Semiwiki readers are well aware of the industry momentum behind machine learning applications. New opportunities are emerging at a rapid pace. High-level programming language semantics and compilers to capture and simulate neural network models have been developed to enhance developer productivity (link). Researchers… Read More
Ampere: More on Arm-Based Servers
Since I talked recently about AWS adding access to Arm-based server instances in their cloud offering, I thought it would be interesting to look further into other Arm-based server solutions. I had a meeting with Ampere Computing at Arm TechCon. They offer server devices and are worth closer examination as a player in this game.… Read More
56G and 112G SerDes Where the rubber meets the road
No matter how high the processing capability of a chip, its overall performance is limited by IO speed. This is very similar to a car with low performance tires, a powerful engine will not be able to transfer its energy to the ground effectively. There is quite literally a race going on between core processing and IO speeds for transferring… Read More




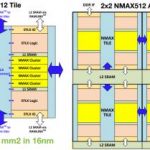

AI Bubble?