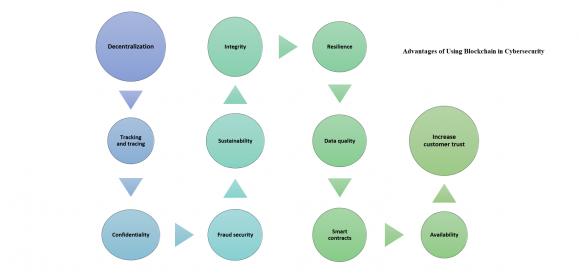
In the first part we covered AI as the first line of defense for cybersecurity, the goal was to keep the cyber-criminals at bay, but in case they managed to get-in and infiltrate the network we need to initiate the second line of defense; #Blockchain. With the fact that cybercrime and cyber security attacks hardly seem to be out of the… Read More
Tag: blockchain
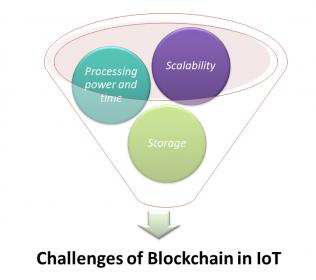
IoT and Blockchain: Challenges and Risks
The Internet of Things (IoT) is an ecosystem of ever-increasing complexity; it’s the next wave of innovation that will humanize every object in our life, and it is the next level of automation for every object we use. IoT is bringing more and more things into the digital fold every day, which will likely make IoT a multi-trillion dollar… Read More
12 Myths about Blockchain Technology
Blockchain, the “distributed ledger” technology, has emerged as an object of intense interest in the tech industry and beyond. Blockchain technology offers a way of recording transactions or any digital interaction in a way that is designed to be secure, transparent, highly resistant to outages, auditable, and… Read More
IoT Value chains now and in the future!
Today, when a company decides to roll out an IoT solution to improve operational efficiency, the management hires a system integrator (SI) to develop and deploy the system. The SI will create and deliver a wholly owned end-to-end solution by externally sourcing all the components required to sense, analyse and decide. There is… Read More
Calling on #IoTman to save humanity!
We, in the hi-tech community, tend to gravitate towards the technology, the API, the device, the platform, the processes node and to forget the goal behind all of those items. We have all noticed the platform wars and cloud API struggle for #IoT market domination. Someone needs to bring back the discussion to the top level, to why … Read More
IoT and Blockchain Convergence
The Internet of Things (IoT) as a concept is fascinating and exciting, but one of the major challenging aspects of IoT is having a secure ecosystem encompassing all building blocks of IoT-architecture. Understanding the different building blocks of IoT, identifying the areas of vulnerability in each block and exploring technologies… Read More
7 Trends of IoT in 2017
IoT is one of the transformational trends that will shape the future of businesses in 2017 and beyond. Many firms see a big opportunity in #IoT uses and enterprises start to believe that IoT holds the promise to enhance customer relationships and drive business growth by improving quality, productivity, and reliability on one … Read More
Predictions for the IOT in 2017
Although we are a far cry from Nostradamus, there are some fairly reliable predictions that can be made about 2017 and beyond.
The first bold prediction is that 2017 will see a bump in security, and a demand for skilled workers. Since there will be a growing demand for AI and the containers that are utilized to transmit information,… Read More
Cybercriminals Next Targets: Long Term Prizes (part 2 of 2)
In the previous blog, Cybercriminals Next Targets: Short Term Dangers (part 1 of 2), I outlined how cybercriminals will use the holiday season to victimize unwary consumers and target businesses. They will also dive deeper into leveraging Internet-of-Things (IoT) devices. The longer-term outlook expands their reach to more… Read More
#IoT: Internet of Tomatoes
In a previous post we looked at how we are going to scale #IoT deployments. The conclusion was that we needed the notions of trust and privacy to be in place for that to happen. In a follow up post, we looked at using a middle man to provider a broker platform that would mediate transactions between server side service applications and… Read More