In the early days of IP reuse and platform-based design there was a widely-shared vision of in-house IP development teams churning out libraries of reusable IP, which could then be leveraged in many different SoC applications. This vision was enthusiastically pursued for a while; this is what drove reusability standards and … Read More
 Hardware is the Center of the Universe (Again)The 40-Year Evolution of Hardware-Assisted Verification — From…Read More
Hardware is the Center of the Universe (Again)The 40-Year Evolution of Hardware-Assisted Verification — From…Read More Smarter ECOs: Inside Easy-Logic’s ASIC Optimization EngineEasy-Logic Technology Ltd. is a specialized Electronic Design…Read More
Smarter ECOs: Inside Easy-Logic’s ASIC Optimization EngineEasy-Logic Technology Ltd. is a specialized Electronic Design…Read More The Name Changes but the Vision Remains the Same – ESD Alliance Through the YearsThe Electronic System Design Alliance (ESDA) has been…Read More
The Name Changes but the Vision Remains the Same – ESD Alliance Through the YearsThe Electronic System Design Alliance (ESDA) has been…Read More TSMC Process Simplification for Advanced NodesIn the modern world, the semiconductor industry stands…Read More
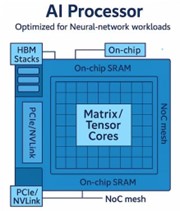
TSMC Process Simplification for Advanced NodesIn the modern world, the semiconductor industry stands…Read More CEO Interview with Juniyali Nauriyal of PhotonectJuniyali Nauriyal is the CEO and Co-Founder of…Read More
CEO Interview with Juniyali Nauriyal of PhotonectJuniyali Nauriyal is the CEO and Co-Founder of…Read MoreEmbedded FPGA IP update — 2nd generation architecture, TSMC 16FFC, and a growing customer base
Regular Semiwiki readers are aware that embedded FPGA (eFPGA) IP development is a rapidly growing (and evolving) technical area. The applications for customizable and upgradeable logic in the field are many and diverse — as a result, improved performance, greater configurable logic capacity/density, and comprehensive… Read More
RTL Correct by Construction
Themes in EDA come in waves and a popular theme from time to time is RTL signoff. That’s a tricky concept; you can’t signoff RTL in the sense of never having to go back and change the RTL. But the intent is still valuable – to get the top-level or subsystem-level RTL as well tested as possible, together with collateral data (SDC, UPF, etc)… Read More
PDA will exhibit at the 54th DAC
Platform Design Automation, Inc will exhibit at the 54th Design Automation Conference(DAC) on June 18-21 in Austin Convention Center, Texas, USA, in Booth #1929. What to Expect:… Read More
Consolidation and Design Data Management
Consensia, a Dassault Systemès channel partner, recently hosted a webinar on DesignSync, a long-standing pillar of many industry design flows (count ARM, Qualcomm, Cavium and NXP among their users). A motivation for this webinar was the impact semiconductor consolidation has had on the complexity of design data management,… Read More
Understanding Sources of Clock Jitter Critical for SOC’s
Jitter issues in SOC’s reside at the crossroads of analog and digital design. Digital designers would prefer to live in a world of clocks that are free from jitter effects. At the same time, analog designers can build PLL’s that are precise and finely tuned. However, when a perfectly working PLL is inserted into an SOC, things can … Read More
CEO Interview: Stanley Hyduke, founder and CEO of Aldec
Dr. Stanley Hyduke, founder and CEO of Aldec talks about how keeping pace with the evolution of FPGAs and listening to customers underpin the company’s success.… Read More
FD-SOI in Japan?
If you want to get your finger on the Japan FD-SOI pulse, registration is still open for a free, two-day workshop in Tokyo this week organized by the SOI Consortium. This is the 3rd Annual SOI Tokyo Workshop, and there’s a really interesting line-up of speakers.
In case you’re wondering, Japan is doing FD-SOI. In fact… Read More
Webinar -New Concepts in Semiconductor IP Lifecycle Management
The semiconductor IP market continues growing at a healthy rate, and IP reuse is a staple of all modern SoC designs. Along with the acceptance of IP reuse comes a host of growing challenges, like:
- Increase in design files
- Increase in meta-data
- More links between design members worldwide
- More links between data in multiple engineering
Three Major Challenges Facing IoT
The Internet of Things (IoT) — a universe of connected things providing key physical data and further processing of that data in the cloud to deliver business insights— presents a huge opportunity for many players in all businesses and industries . Many companies are organizing themselves to focus on IoT and the connectivity of… Read More






The Name Changes but the Vision Remains the Same – ESD Alliance Through the Years