TSMC warns soft phone/crypto & flat capex!
Does this impact DRAM?
Can Intel keep Apple?
We love Tesla (Model 3)!… Read More
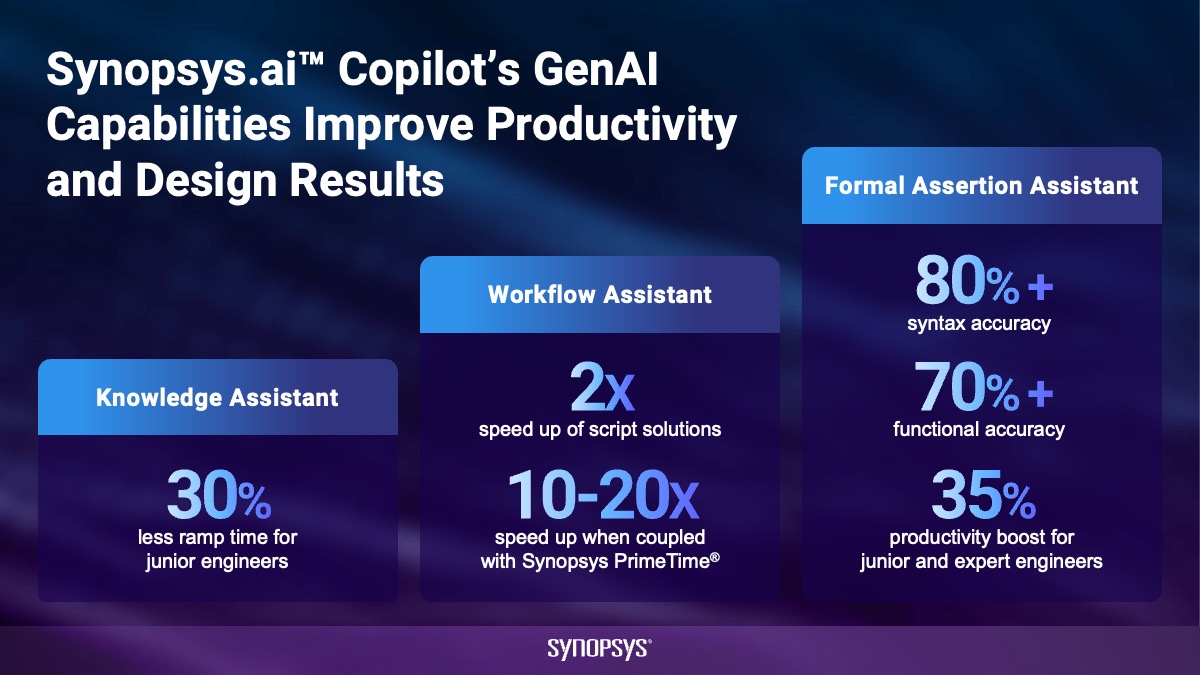 Synopsys Announces Expanding AI Capabilities and EDA AI LeadershipIn the fast-paced semiconductor industry Synopsys has redefined…Read More
Synopsys Announces Expanding AI Capabilities and EDA AI LeadershipIn the fast-paced semiconductor industry Synopsys has redefined…Read More Webinar Preview – Addressing Functional ECOs for Mixed-Signal ASICsAn engineering change order, or ECO in the…Read More
Webinar Preview – Addressing Functional ECOs for Mixed-Signal ASICsAn engineering change order, or ECO in the…Read More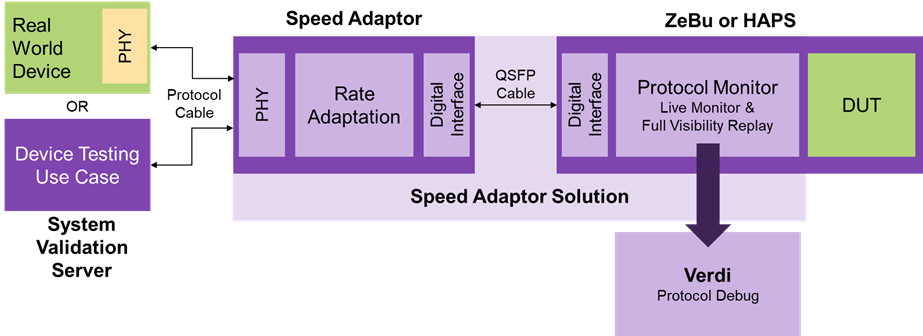 The Rise, Fall, and Rebirth of In-Circuit Emulation (Part 1 of 2)Introduction: The Historical Roots of Hardware-Assisted Verification The…Read More
The Rise, Fall, and Rebirth of In-Circuit Emulation (Part 1 of 2)Introduction: The Historical Roots of Hardware-Assisted Verification The…Read More Tessent MemoryBIST Expands to Include NVRAMThe concept of built-in self-test for electronics has…Read More
Tessent MemoryBIST Expands to Include NVRAMThe concept of built-in self-test for electronics has…Read More The Importance of Productizing AI. Everyday ExamplesKeeping up with the furious pace of AI…Read More
The Importance of Productizing AI. Everyday ExamplesKeeping up with the furious pace of AI…Read MoreWill the Rise of Digital Media Forgery be the End of Trust?
Technology is reaching a point where it can nearly create fake video and audio content in real-time from handheld devices like smartphones.
In the near future, you will be able to Facetime someone and have a real-time conversation with more than just bunny ears or some other cartoon overlay. Imagine appearing as a person of your … Read More
Maybe it is time to #DeleteWhatsApp
WhatsApp differentiates itself from Facebook by touting its privacy and end-to-end encryption. “Some of your most personal moments are shared with WhatsApp”, it says, so “your messages, photos, videos, voice messages, documents, and calls are secured from falling into the wrong hands”. A WhatsApp founder expressed… Read More
EUV Continues Roll Out With Lumpy Quarters Ahead
ASML put up good results with revenues of Euro2.285B versus street of Euro2.22B and EPS of Euro1.26 versus street of Euro1.17. Guide is for Euro2.55B versus street of Euro2.46B but EPS of Euro1.16 versus street EPS of Euro1.35 on lower gross margins, slipping from 48% to 43%.
A couple of EUV systems have slipped out. This is not surprising… Read More
The Intention View: Disruptive Innovation for Analog Design
Intento Design builds responsive analog EDA. The ID-Xplore tool is used for analog design acceleration and technology porting at the functional level, helping companies move analog IP quickly between technology nodes and across business units. The Intention view is a simple, elegant, and powerful concept that gives the speed… Read More
Data Breach Laws 0-to-50 States in 16 Years
It has taken the U.S. 16 years to enact Data Breach laws in each state. California led the way, with the first, in 2002 to protect its citizens. Last in line was Alabama, which just signed their law in March 2018. There is no overarching consistent data breach law at the federal level. It is all handled independently by each state. This… Read More
Meltdown, Spectre and Formal
Once again Oski delivered in their most recent Decoding Formal session, kicking off with a talk on the infamous Meltdown and Spectre bugs and possible relevance of formal methods in finding these and related problems. So far I haven’t invested much effort in understanding these beyond a hand-waving “cache and speculative execution”… Read More
RDC – A Cousin To CDC
In a post-silicon bringup, it is customary to bring the design into a known state prior to applying further testing sequences. This is achieved through a Power-on-Reset (POR) or similar reset strategy which translates to initializing all the storage elements to a known state.
During design implementation, varying degrees of… Read More
Artificial Intelligence calls for Smart Interconnect
Artificial Intelligence based systems are driving a metamorphosis in computing, and consequently precipitating a large shift in SOC design. AI training is often done in the cloud and has requirements for handling huge amounts of data with forward and backward data connections. Inference usually occurs at the edge and must be… Read More
Tensilica 5th Generation DSP: Mix of Vision and AI
Cadence has launched the new Tensilica Vision Q6 DSP IP, delivering 1.5x more performance than the former Vision P6 DSP IP and 1.25X better power efficiency. According with Cadence, the mobile industry is moving from traditional feature-based embedded vision to AI-based algorithm, even if all use cases still have mix of vision… Read More









Rapidus, IBM, and the Billion-Dollar Silicon Sovereignty Bet