By now you have probably realized that 5G is a lot more than an incremental change from previous 3G and 4G cellular technology. For instance, 5G will be used to connect our phones in completely new ways, such as with microcells in urban areas using mm-wavelength signals. 5G will also include two low power protocols that are intended for use by IoT devices. One is Narrowband IoT (NB-IoT), which is intended for indoor use, with low power and long battery life. The other is LTE-M, which has a higher data rate and range than NB-IoT. However, it is still intended for machine to machine (M2M) links. GSA reports that as of March 2019 104 operators in 53 countries have already deployed or launched one or both of NB-IoT or LTE-M technologies.
While they may be different than the protocols used for voice handsets, NB-IoT and LTE-M will share the high security offered by SIM (subscriber identification module) technology. Many of today’s IoT devices are now living in a wild west type of security environment. Understandably, the move to a robust identification will be welcome indeed.
SIM conjures up images of those hardware modules that are inserted into our phones to enable devices to work on carrier networks. Today cell phone and mobile hot spot users need to fumble with SIM cards when it comes time to switch carriers, or devices. Inserting and removing SIM cards might be fine for the devices we keep on our person, but IoT deployments often consist of many devices, which might be far flung and/or difficult to access. Simply put, swapping SIM cards is a non-starter for IoT deployments in the future.
A SIM card is not just a machine-readable serial number. It’s an application running on a processor and storage in the card itself. The physical card is called a Universal Integrated Circuit Card (UICC). The UICC has storage for user specific information such as a phone book and text messages, in addition to the unique identifier for the wireless customer. Because the UICC is self-contained, it can be securely manufactured to ensure security. In order to replace the SIM card with something embedded in the connected device, remote provisioning protocols were developed by the GSMA. This new embedded UICC is called eSIM or eUICC and is frequently a small chip that is soldered into the IoT or mobile device when it is manufactured. However, this still adds to the BOM, requires extra steps in manufacturing and takes up precious space in the device.
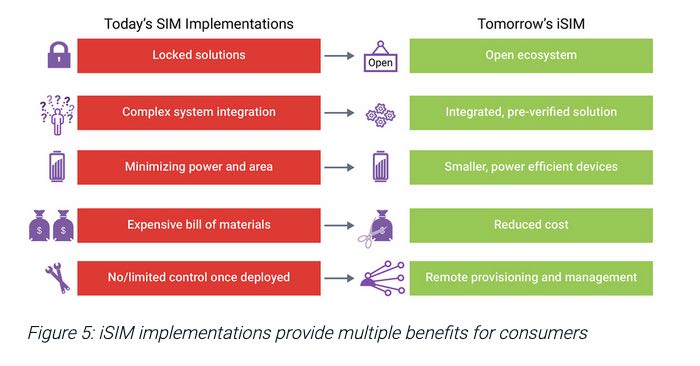
The next step in this evolution is a fully integrated UICC, called iSIM, that can be designed right into the device’s SOC. Extra care must be taken to provide a secure execution environment for the iSIM. Synopsys has recently published a write up on their website that goes into the topic of putting together a complete solution for iSIM, including hardware IP, application software and remote provisioning capability. iSIMs can be used with any service provider, but there is still a need for a commercial solution to transfer Profiles for any carrier into the iSIM. Synopsys has partnered with Truphone for this service and has completely integrated the process to eliminate boot strap issues in the field.
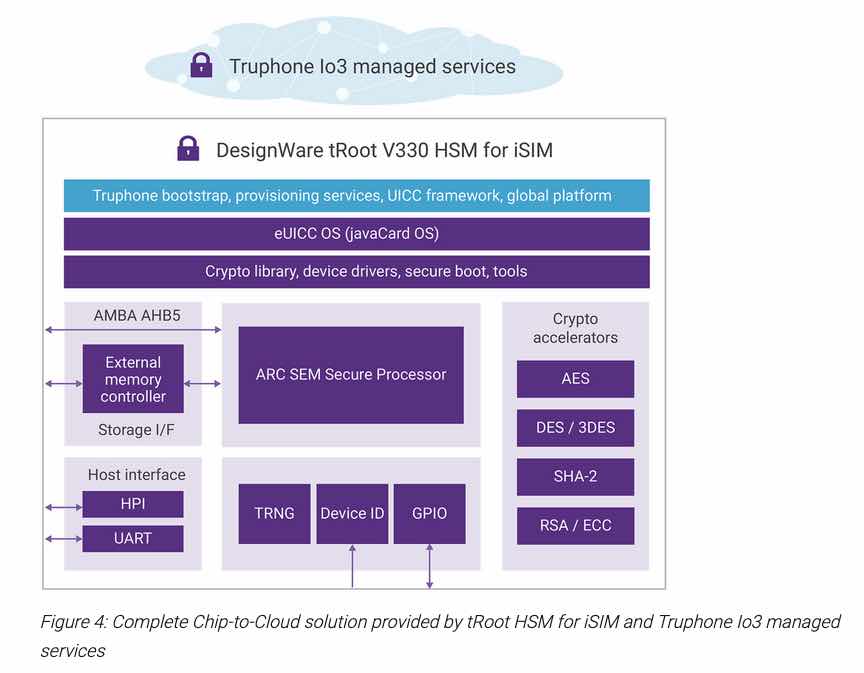
Designers can start with Synopsys DesignWare tRoot Fx Hardware Secure Modules (HSMs) and add their own preferred eSIM/eUICC solution, which could be from an internal source, a Synopsys partner or any third party. The Synopsys HSM contains all the hardware modules needed to build a secure working iSIM. Alternatively, Synopsys offers the tRoot V330 HSM for iSIM that is a complete solution.
Reference: Move the IoT from WiFi to Global Cellular – Securely
Share this post via:






Comments
There are no comments yet.
You must register or log in to view/post comments.