The automotive industry is undergoing a remarkable transformation, with vehicles becoming more connected, automated, and reliant on software. While these advancements promise convenience, comfort and efficiency to the consumers, the nature and complexity of the technologies also raise concerns for functional safety and security. The ISO 26262 standard was established for ensuring a systematic approach to functional safety in the automotive industry. This standard provides a comprehensive framework for managing functional safety throughout the entire product development lifecycle, including concept, design, implementation, production, operation, maintenance, and decommissioning. It offers guidance on hazard analysis, risk assessment, safety goals, safety mechanisms, and verification and validation processes to ensure that electronic systems function as intended and maintain safety even in the presence of faults or errors.
The ISO 26262 standard addresses impact to safety due to faults and failures. What about addressing factors such as cybersecurity? The soaring adoption of electronics in the automotive sector has led to a corresponding expansion in the cybersecurity threat landscape. As vehicles become more connected and reliant on software-driven functionality, the attack surface expands significantly. This convergence of technological advancement and risk underscores the critical importance of cybersecurity-aware development practices. Road vehicles rely heavily on communication between components and external systems, making them susceptible to various cyber risks. Over-the-Air (OTA) software updates dramatically increase cybersecurity risks. Hackers could potentially manipulate sensor data, compromise vehicle control systems, or gain unauthorized access to sensitive personal information. The ISO/SAE 21434 Road Vehicles—Cybersecurity Engineering standard was established to address the security challenges posed by cyberthreats to road vehicles.
Synopsys has recently published a whitepaper that delves into the ISO 21434 driven best practices for cybersecurity-aware SoC development. Anyone involved in the development and post-production support of automotive related products and systems would find this whitepaper very informative. Following are some excerpts.
Key Aspects of ISO 21434
The ISO 21434 standard provides a structured approach to identifying, assessing, and mitigating cybersecurity risks throughout the development of automotive products, including components like SoCs. This comprehensive framework builds upon similar principles of ISO 26262 to address the cybersecurity dimension. The alignment between these two standards not only streamlines the integration of cybersecurity practices but also establishes a common vocabulary, ensuring seamless adaptation for organizations already compliant with ISO 26262.
Organizational Responsibilities
ISO 21434 follows in the footsteps of ISO 26262 by delineating roles and responsibilities across various stages of product development. This includes the commitment of executive management, the establishment of standardized roles between suppliers and supply chain entities, the creation of distinct phases within the product life cycle, and the formulation of Threat Analysis and Risk Assessment (TARA) processes equivalent to Hazard Analysis and Risk Assessment (HARA) in ISO 26262.
Cybersecurity Risk Assessment and Management
Cybersecurity hinges on a thorough assessment of a product’s inherent risks and its vulnerabilities when deployed. Four critical factors govern the severity of a cybersecurity risk, enabling an informed approach to risk mitigation. These four key factors are the Threat Scenario, Impact, Attack Vector, and Attack Feasibility. Together, these factors determine the potential harm, enabling a structured evaluation of the risk’s impact and the need for intervention. In essence, the Threat Scenario and its Impact gauge potential damage, the Attack Vector factor maps how an attack could be executed, while the Feasibility factor evaluates the ease of enacting the attack. ISO 21434 offers techniques for calculating the risk score from these four factors and elucidates a structured approach for fostering a proactive stance against cyberattacks.
Security by Design
The Secure Development Lifecycle (SDL) process championed by Microsoft to address cybersecurity permeates all facets of production development. SDL orchestrates a number of measures during the design phase to safeguard products against potential vulnerabilities. At the heart of this phase lies the mandate to generate concrete evidence affirming the integration of secure practices the team has been trained for. This evidence encompasses a spectrum of reviews and metrics, from security design reviews and verification plan assessments to privacy design reviews. Tools such as Synopsys Coverity and Black Duck play pivotal roles, generating code coverage and composition analysis reports. These reports help gauge the codebase’s maturity while flagging vulnerabilities in third-party components.
Collaboration and Communication
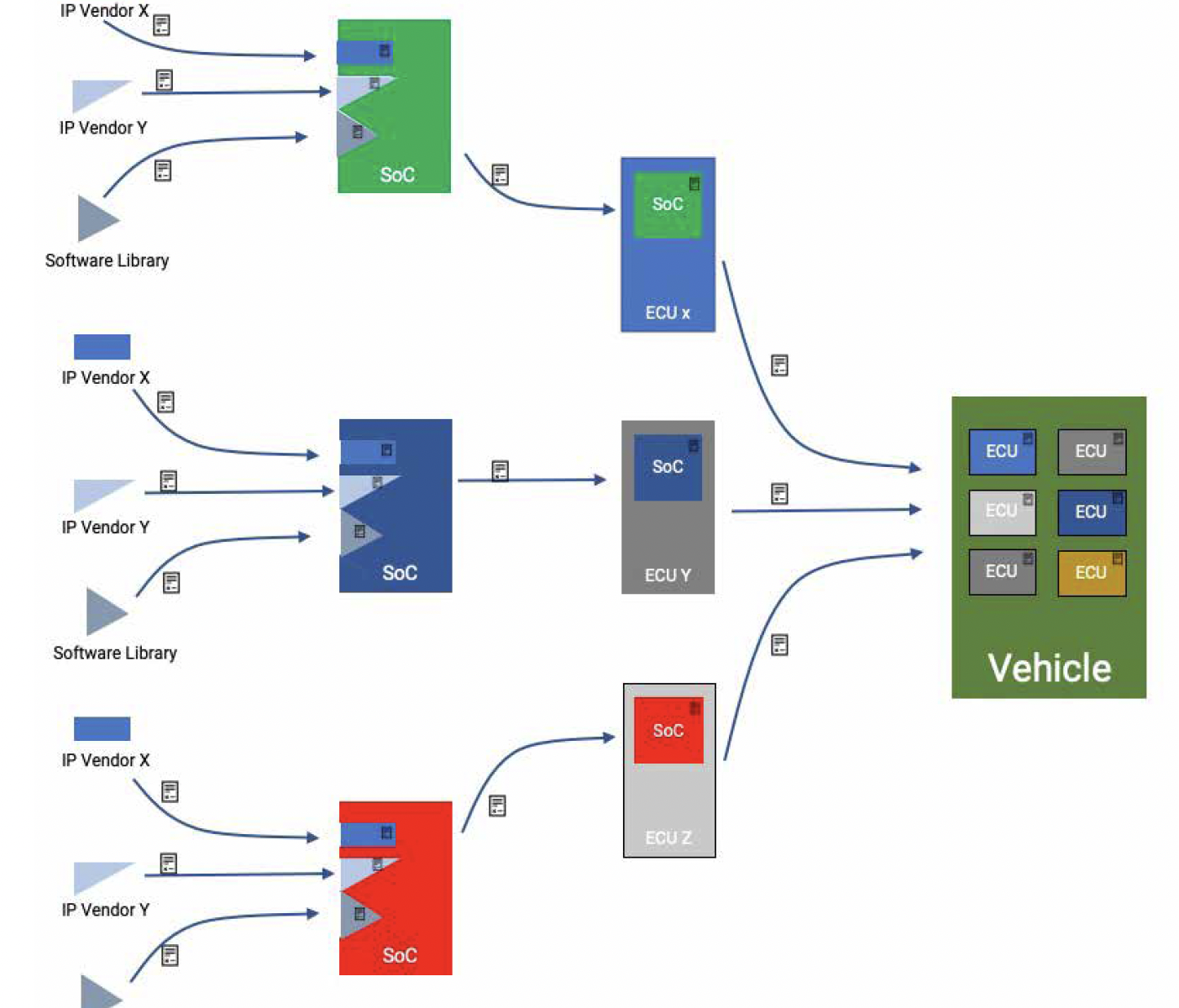
In the interconnected world of today’s product development, cybersecurity cannot operate in isolation. A collaborative approach is imperative, demanding a cohesive and cybersecurity-aware handshake between every link in the supply chain. The collaborative mindset guides the development cycles, necessitating an ongoing flow of cybersecurity information among supply chain entities.
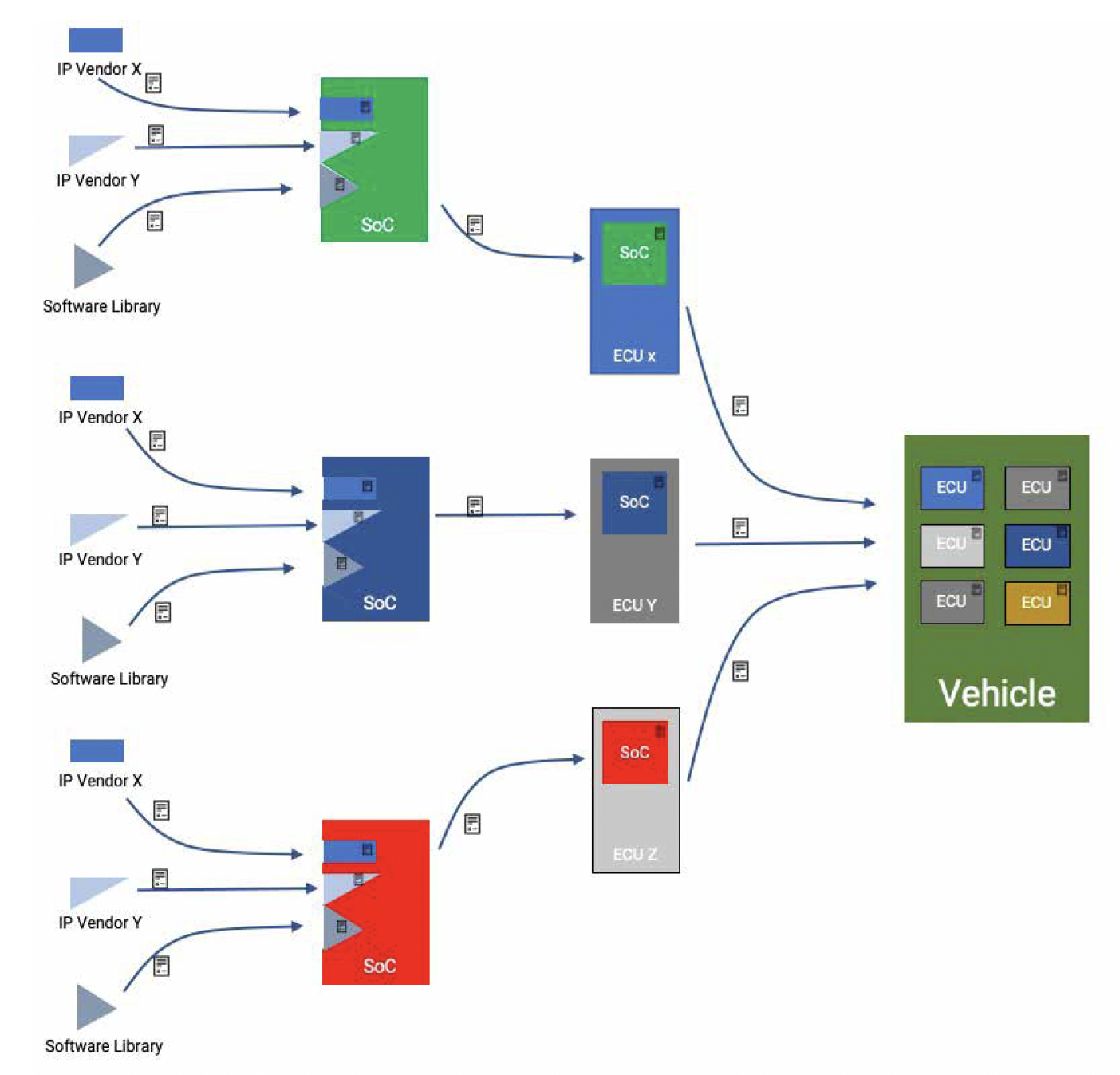
Cybersecurity agreement in supply chain
Continuous Monitoring and Updating
Continuously monitoring products to identify known vulnerabilities and updating, ensures cybersecurity from the product’s release to its decommissioning. Post-release support is a focal point in SDL’s continuum. It mandates the specification of requirements for post-production security controls. This meticulous preparation equips the product to navigate the complexities of its operational environment and supply chain.
Summary
Given the surge in electronics adoption into road vehicles and the evolving landscape of cyberattack threats, customers are demanding cybersecurity assurances. Cybersecurity impacts every level of the automotive supply chain starting with semiconductor SoCs. For component suppliers, embracing standardized cybersecurity principles and processes becomes a strategic imperative to remain competitive in the dynamic automotive market. By adhering to these evolving industry standards, suppliers can not only address the growing cybersecurity concerns but also cater to the mounting customer expectations for robust cybersecurity assurance.
During development of complex SoCs, partnering with an IP supplier with a structured ISO 21434 development platform minimizes cybersecurity risks and ensures highest levels of success. Synopsys develops IP products as per the ISO 21434 standard and rigorously follows cybersecurity policies, processes and procedures as promulgated in the standard. The company deploys cybersecurity teams through all levels of the organization.
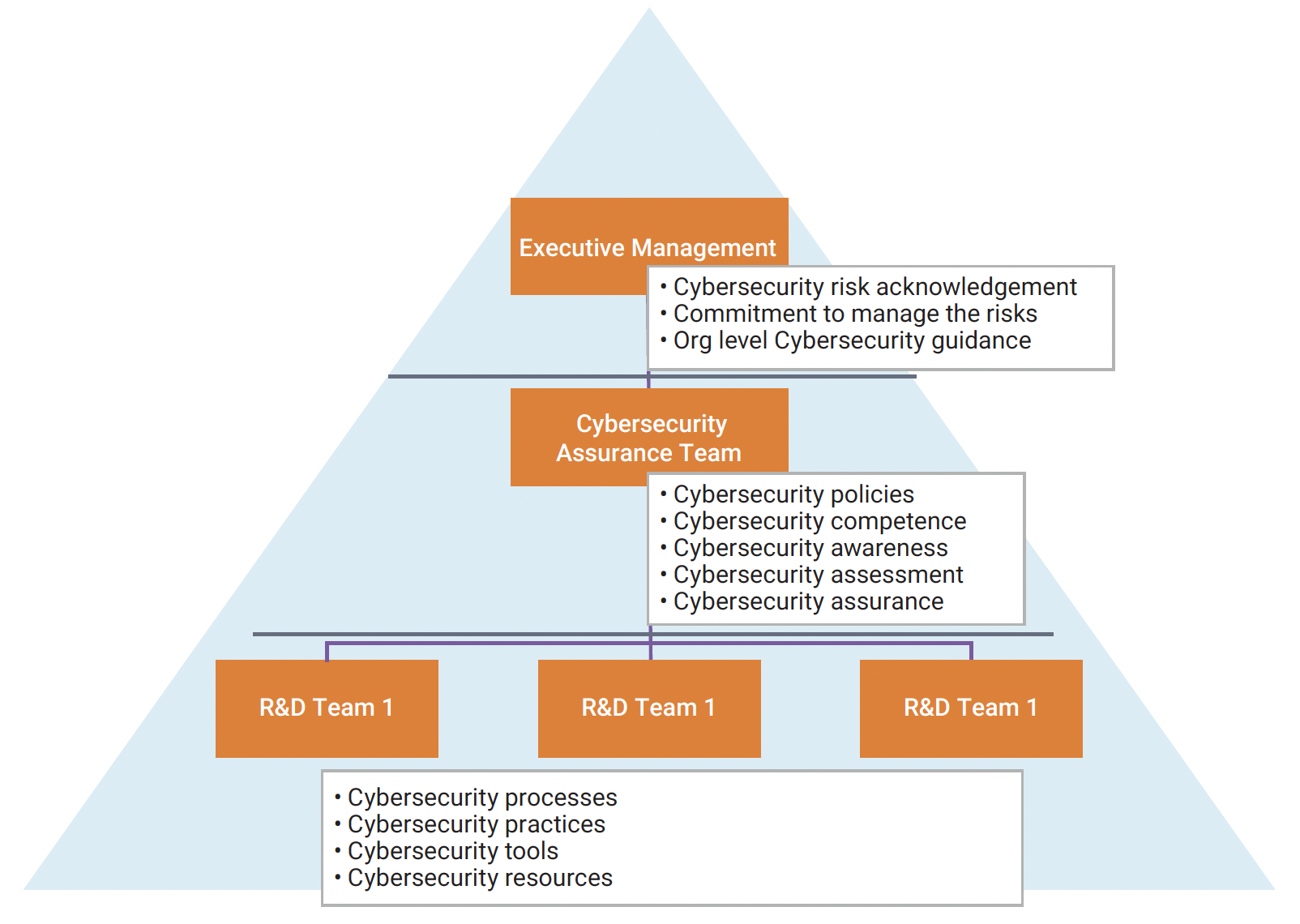
Cybersecurity teams through all levels of an organization
For more details, visit Accelerate Your Automotive Innovation page.
You can access the entire whitepaper here.
Also Read:
Key MAC Considerations for the Road to 1.6T Ethernet Success
AMD Puts Synopsys AI Verification Tools to the Test
WEBINAR: Why Rigorous Testing is So Important for PCI Express 6.0
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.