Tuple Technologies delivers Tropos, a platform automating IT infrastructure across Cloud, Hybrid or On-prem and DevSecOps for semiconductor IC, FPGA, and system design, optimizing costs and cybersecurity.
Attendees who step into the Tuple Technologies booth during DAC (Booth #1237) will see demonstrations of its Tropos … Read More
Dan is joined by Dr. Andreas Kuehlmann, Executive Chairman and CEO at Cycuity. He has spent his career across the fields of semiconductor design, software development, and cybersecurity. Prior to joining Cycuity, he helped build a market-leading software security business as head of engineering at Coverity which was acquired… Read More
RSAC 2025by Admin on 01-27-2025 at 3:09 pm
Unite. Innovate. Shine. Join the RSAC 2025 Community.
At RSAC 2025, you’re not just attending a conference—you’re stepping into a vibrant, thriving community of thinkers, innovators, and achievers. Though we come from different corners of the cybersecurity world, we are united by a common mission: to foresee … Read More
Many of you are already familiar with Silicon Catalyst and the value it brings to semiconductor startups, the industry and the electronics industry at large. Silicon Catalyst is an organization that supports early-stage semiconductor startups with an ecosystem that provides tools and resources needed to design, create, and… Read More
Secure-IC is a global leader in end-to-end cybersecurity solutions, specializing in the domain of embedded systems and connected devices. With an unwavering commitment to pushing the boundaries of security innovation, Secure-IC has established a remarkable track record. Its credentials include active involvement in new… Read More
The automotive industry is undergoing a remarkable transformation, with vehicles becoming more connected, automated, and reliant on software. While these advancements promise convenience, comfort and efficiency to the consumers, the nature and complexity of the technologies also raise concerns for functional safety … Read More
For decades, the concept of flying cars has captivated our imagination, fueling visions of a future where we can soar above the ground, free from the constraints of traffic and congestion. While once considered purely the stuff of science fiction, recent advancements in technology have brought us closer to turning this fantasy… Read More
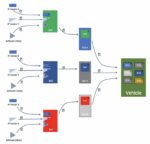
Dan is joined by Michael Ichiriu, Vice President of Marketing at Zentera Systems. Prior to Zentera Mike was a senior executive at NetLogic Microsystems where he played a critical role in shaping the company’s corporate and product strategy. While there, he built the applications engineering team, and helped lead the organization… Read More
Dan is joined by Hassan Triqui who has over 20 years of experience in the technology sector. Prior to spearheading Secure-IC’s development into a major player in embedded cybersecurity solutions, Hassan was a former senior executive at Thales (Talles) and Thomson.
Dan explores Secure-IC’s vision and strategy to deploy… Read More