Typically, there is an existential rift between the on-chip access requirements for test and the need for security in SoCs. Using traditional deterministic scan techniques has meant opening up full read and write access to the flops in a design through the scan chains. Having this kind of access easily defeats the best designed functional mode security. With so many new applications requiring security, it is essential to eliminate any security holes created because of test.
Furthermore, test has moved from being something done only during manufacture, to an ongoing requirement to monitor chip operation. New approaches are needed to fulfill expanding needs and at the same time close down any avenues that might compromise chip security. Siemens EDA has written a white paper that outlines how a wide range of techniques can be utilized separately or together to provide security in depth. Interestingly many of these techniques are already extremely desirable from a strictly test perspective.
The white paper titled “High-quality test and embedded analytic solutions for secure applications” written by Lee Harrison talks about the need for secure test and illustrates a series of techniques that are very useful. At the core of each of these techniques is the notion that there should be no direct connection between the external test pins and the internal scan chain. Without this separation the chip can be probed and even controlled with ease. Fortunately, many of the innovations for test to meet speed, capacity and flexibility requirements have the added benefit of abstracting access to the scan chains themselves.
The Siemens white paper describes a progression of techniques, starting with logic built-in self test (LBIST) that secure the scan mechanisms on SoCs. The benefits of LBIST are multifold, offering in system test, speeding up test time and comes with added benefit that it seals off the scan chain from direct external access. However, LBIST without a BIST bypass mode can limit the ability to diagnose failures. So additional methods such as adding security features to the test access point (TAP) controllers may be needed.
Test compression is another effective way to limit direct access to the scan chains. Conveniently it also is useful for other directly related test improvements, such as reducing tester data transfer volume. Tessent TestKompress is already widely used for testing chips for smart cards and defense related designs where it adds a layer of security. Test compression screens both the input and output of the scan chains.
Further isolation and encapsulation of the scan chains is achieved through the Tessent Streaming Scan Network (SSN). Here all of the scan data is packetized and transmitted through a dedicated on-chip test network. Of course, as above, there are many practical benefits and reasons to deploy an SSN. It offers full isolation of the scan chains which can only be accessed electrically by the SSN nodes embedded within the chip.
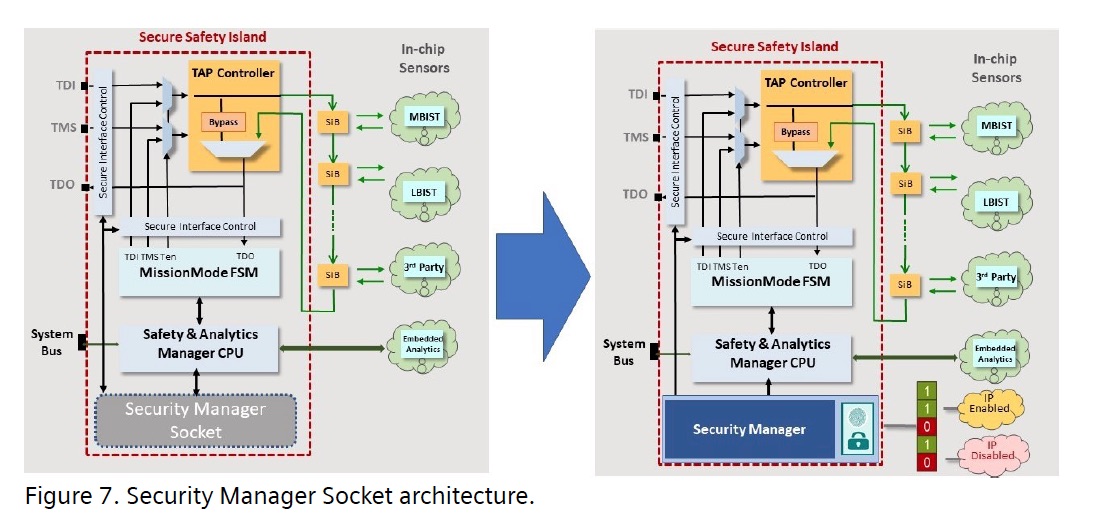
The Siemens white paper provides insights into several other methods that can improve security while meeting the needs of testability. Foremost among these is upgrading the interface to the TAP controller so that it is in a safety island. This safety island can use a state-of-the-art security manager to limit access based on security needs. It also makes it possible to offer different levels of secure access depending on whether the chip is still on-premise during manufacture or deployed in the field as part of a system.
The white paper makes good reading and offers useful information for anyone looking to tighten up security through this potentially risky portion of their design. The white paper can be downloaded here through the Siemens website.
Also read:
Siemens EDA on the Best Verification Strategy
Scalable Verification Solutions at Siemens EDA
Power Analysis in Advanced SoCs. A Siemens EDA Perspective
Share this post via:






Comments
There are no comments yet.
You must register or log in to view/post comments.