As Moore’s Law enables increased integration, the diversity of functionality in SoC designs has grown. Design teams are seeking to utilize outside technical expertise in key functional areas, and to accelerate their productivity by re-using existing designs that others have developed. The Intellectual Property (IP) industry… Read More
Semiconductor Intellectual Property
Safety in the Interconnect
Safety is a big deal these days, not only in automotive applications, but also in critical infrastructure and industrial applications (the power grid, nuclear reactors and spacecraft, to name just a few compelling examples). We generally understand that functional blocks like CPUs and GPUs have to be safe, but what about the … Read More
SiFive’s Design Democratization Drive
There is something endearing and refreshing in seeing a novel approach unfold in our Semi-IP-EDA ecosystem currently settled in its efficient yet, let us say it, unexciting ‘going through the motions’, constantly comparing, matching, competitively and selfishly sub-optimizing what the art of the possible can be.
Enter a new… Read More
Artificial Intelligence calls for Smart Interconnect
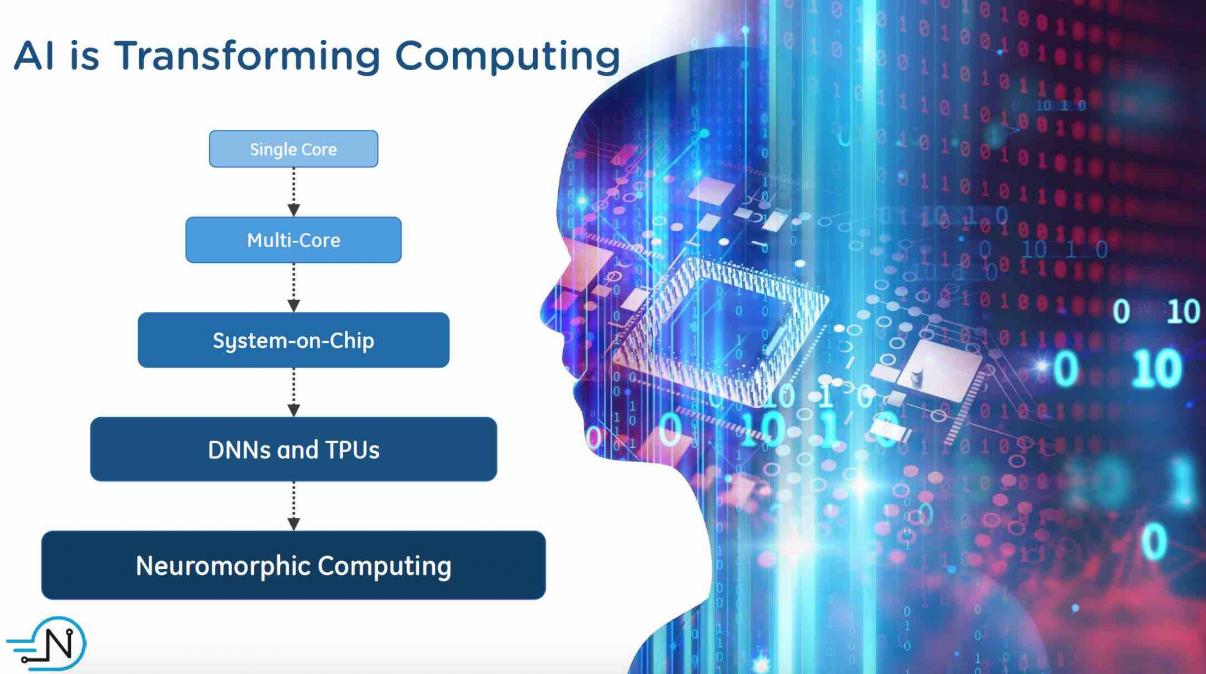
Artificial Intelligence based systems are driving a metamorphosis in computing, and consequently precipitating a large shift in SOC design. AI training is often done in the cloud and has requirements for handling huge amounts of data with forward and backward data connections. Inference usually occurs at the edge and must be… Read More
Tensilica 5th Generation DSP: Mix of Vision and AI
Cadence has launched the new Tensilica Vision Q6 DSP IP, delivering 1.5x more performance than the former Vision P6 DSP IP and 1.25X better power efficiency. According with Cadence, the mobile industry is moving from traditional feature-based embedded vision to AI-based algorithm, even if all use cases still have mix of vision… Read More
Enabling A Data Driven Economy
The theme of this year CDNLive Silicon Valley keynote given by Cadence CEO, Lip-Bu Tan evolves around data and how it drives Cadence to make a transition from System Design Enablement (SDE) to Data Driven Enablement (DDE). Before elaborating further, he noted on some CDNLive conference statistics: 120 sessions, 84% done by users,… Read More
A Turnkey Platform for High-Volume IoT
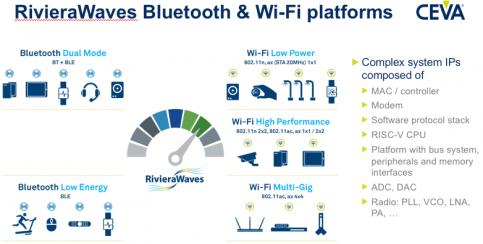
Innovation in smart homes, smart buildings, smart factories and many other contexts differentiates in sensing, in some cases actuation, implementation certainly (low power for example) and rolling up data to the cloud. It isn’t in the on-board CPU and I doubt any of those entrepreneurs want to create their own Bluetooth or Wi-Fi… Read More
Safety Critical Applications Require Onboard Aging Monitoring
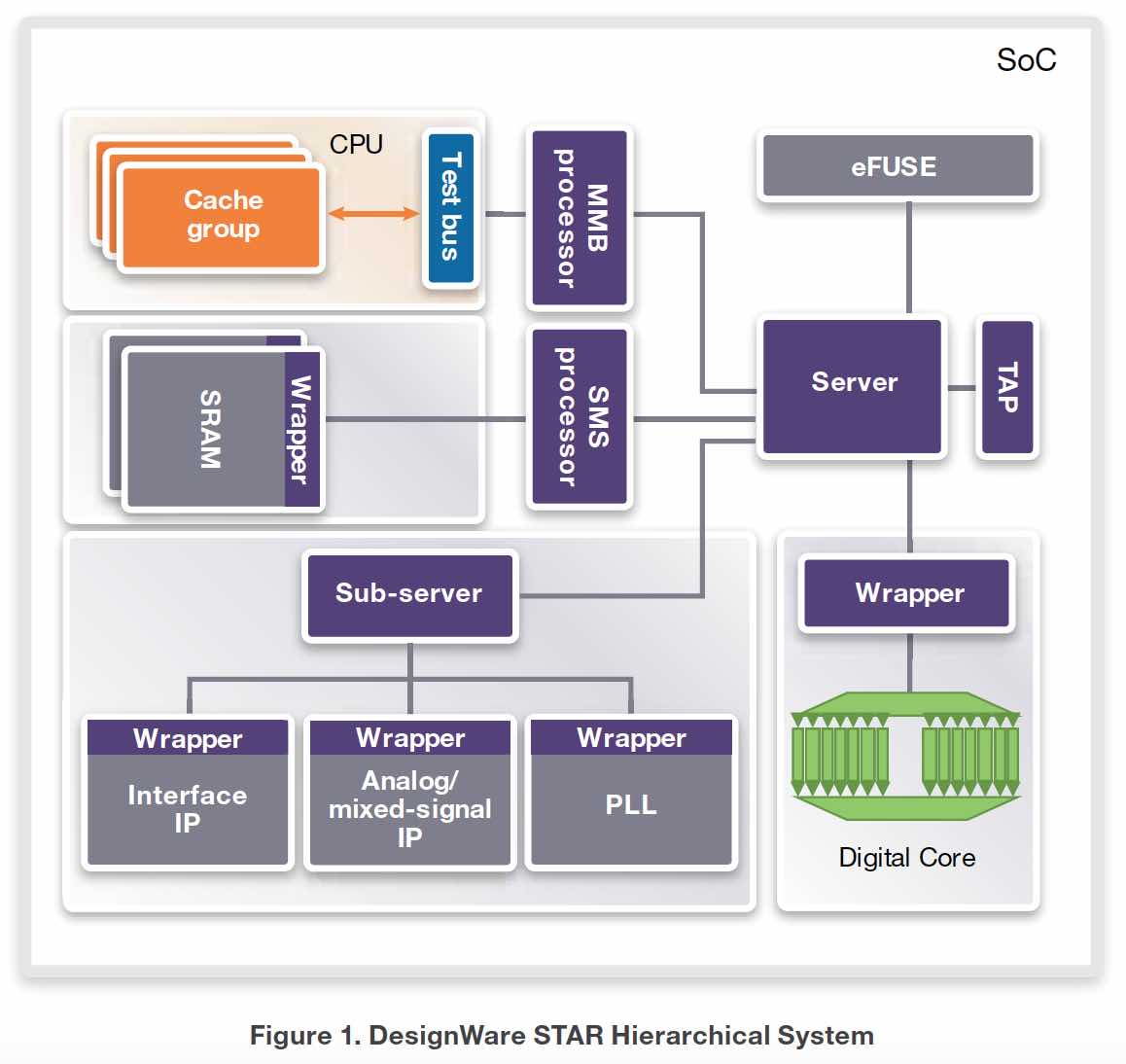
When it comes to safety, ISO 26262 is the spec that comes to mind for many people. However, there are layers of specifications that enable the level of safety required for automotive and other systems that need high reliability. For any application requiring safety, test is a critical element. A key spec for SOC test is IEEE 1500, … Read More
FlexE at SoC IP Days with Open Silicon
On Thursday April 5th the Design and Reuse SoC IP days continues in Santa Clara at the Hyatt Regency (my favorite hangout). SemiWiki is a co-sponsor and I am Chairman of the IP Security Track. More than 400 people have registered thus far and I expect a big turnout, if you look at the program you will see why. You should also know that registration… Read More
Webinar: Fastest Lowest-Cost Route to Developing ARM based Mixed Signal SoCs
When it comes to building edge devices for the internet-of-things (IoT), you don’t want to have to break the bank to prototype an idea before diving into the deep water. At the same time, if your idea is to shrink an edge device down to it’s smallest dimensions, lowest power and lowest cost, you really want to be able to prototype your… Read More







CES 2026 and all things Cycling