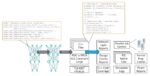
Git is a version control system that saves every change made to files. It offers powerful tools for managing these changes. This makes Git ideal for software development, as it lets you keep all project files in one place.
Software has grown in complexity, necessitating more collaboration among engineers across various time zones. Software tools advanced to handle the increased number of iterations, files, and data. Initially, tools like RCS and SCCS could only manage file revisions, not entire software projects. CVS is a version control system that allows multiple developers to work on a project simultaneously while keeping the project consistent. As development spread across various geographies and functional teams, systems like ClearCase, Perforce, and SVN became essential for managing the process. Eventually, Git and Mercurial emerged to support the distributed development of extensive open-source projects effectively.
Git has become the go-to solution for tracking changes and managing software development flows. However, it is worth exploring whether Git is the best choice for projects beyond software development, such as semiconductor chip design. This blog post examines whether Git can effectively manage workflows in different fields.
How is semiconductor design different?
Like software development flows, IC design involves an extensive collection of files. A team of engineers goes through numerous revisions during the product’s development, debugging, and enhancement stages. Naturally, they must distribute their updates efficiently and precisely among the team. As the project progresses, managing the data becomes more complex as teams seek to find the optimal configurations of IC schematics, layouts, and semiconductor Intellectual Property (IP Cores). Also, managing associated simulation and analysis data and meta-data is an additional challenge in hardware design flows.
In addition to the fundamental similarities, there are also several notable differences.
- Digital designs are commonly crafted using Verilog text files and edited with text editors. However, analog and mixed-signal (AMS) designs and packaging designs are created as binary files or groups of binary and text files to represent design objects such as schematics and layouts using specialized graphical editors.
- A software workflow is characterized by a cyclical process of editing, compiling, and debugging. In contrast, the workflow for semiconductor design is significantly more nuanced, involving various editors in creating the components.
- Various steps are required to complete the design, such as synthesis, place and route, different types of simulations, formal verification, timing analysis, etc. These tools and flows necessitate the collaboration of engineers with diverse specializations to generate binary files, which may require version management.
- Specific components, often called Intellectual Property (IP) blocks, might be repurposed entirely or partially. These IPs are frequently acquired from external suppliers and might come with limitations regarding the editing permissions within the more extensive system.
Git serves as a robust platform for overseeing software development processes. Individual engineers focus on creating new features or resolving problems. The platform’s proficiency in integrating modifications into text files facilitates highly effective collaborative development, particularly within open-source initiatives.
Nonetheless, it must address the specific needs of semiconductor development, especially within a company. We’ll investigate these needs and the areas where Git might not measure up.
In IC design, several large files, ranging from a few MBs to several GBs, are expected. The operational framework of Git, which involves users cloning the repository, results in each user duplicating all the repository files and their numerous revisions. This practice can incur significant expenses in a corporate setting where the bulk of design data resides on costly, high-reliability network storage systems.
In the realm of IC design, particularly within analog and custom domains, the creation of binary files is a standard practice. Due to the non-automatable nature of combining schematics and layouts, utilizing a centralized repository equipped with editing restrictions is the optimal strategy to circumvent the intricacies and potential errors associated with manual merging.
Designing involves teamwork among various engineers, including design, verification, and layout engineers. They need to work together and share frequent updates. A central repository model allows frequent updates and better collaboration than a distributed repository model, as engineers can track each other’s work and stay updated on changes.
Design teams work from different locations. For example, design engineers might be in one country, while layout engineers might be in another. They need to coordinate their work regularly. Technology such as cache servers helps them do this effectively, considering the large volume of design data that needs to be shared.
Design objects are typically grouped sets of files treated as a single entity rather than just a set of files. Access restrictions are essential because engineers have specific roles, like preventing a layout engineer from changing a schematic by mistake. Also, it’s crucial to restrict contractors from sensitive materials. Centralized management of project data is necessary to maintain these access controls.
Although data might be organized in a simple flat directory system, IC design usually follows a structured hierarchy of blocks, where each tier incorporates a block from the below level. An IC designer requires a configuration management system to retrieve and manipulate the design hierarchy.
Consider how difficult it would be for software developers if they couldn’t compare different versions of files to see the changes. It would be a huge task to check for updates or track down the source of a new error. Similarly, circuit designers and layout engineers should have access to tools to spot differences in schematics or layouts between versions.
Indeed, the engineers’ design tools must incorporate revision control and configuration management functionalities. This is not only a matter of convenience; the design tools must also know the configuration management system to ensure that adds, deletes, and changes are correctly recorded and represented in the tools.
The temptation is to look for existing tools and shoehorn them to meet similar needs in a different domain. Git and other software configuration management (SCM) tools, as the name suggests, were developed by software engineers to meet the needs of software engineers. Each domain may have some unique requirements that differ from those of software development. It makes sense to explore your development tools and methodology requirements before adopting a configuration management system you will work with for many years.
Keysight Data Management System (SoS)
Also Read:
Self-heating and trapping enhancements in GaN HEMT models