At this year’s Design Automation Conference (DAC), TSMC unveiled more details about the design enablement platforms that were introduced at their 23[SUP]rd[/SUP] annual TSMC Technology Symposium earlier this year. I attended a presentation on TSMC’s Automotive Enablement Platform held at the Cadence Theater where TSMC’s… Read More
 Why TSMC is Known as the Trusted FoundryTaiwan Semiconductor Manufacturing Company (TSMC) is widely regarded…Read More
Why TSMC is Known as the Trusted FoundryTaiwan Semiconductor Manufacturing Company (TSMC) is widely regarded…Read More Journey Back to 1981: David Patterson Recounts the Birth of RISC and Its Legacy in RISC-VIn a warmly received keynote at the RISC-V…Read More
Journey Back to 1981: David Patterson Recounts the Birth of RISC and Its Legacy in RISC-VIn a warmly received keynote at the RISC-V…Read More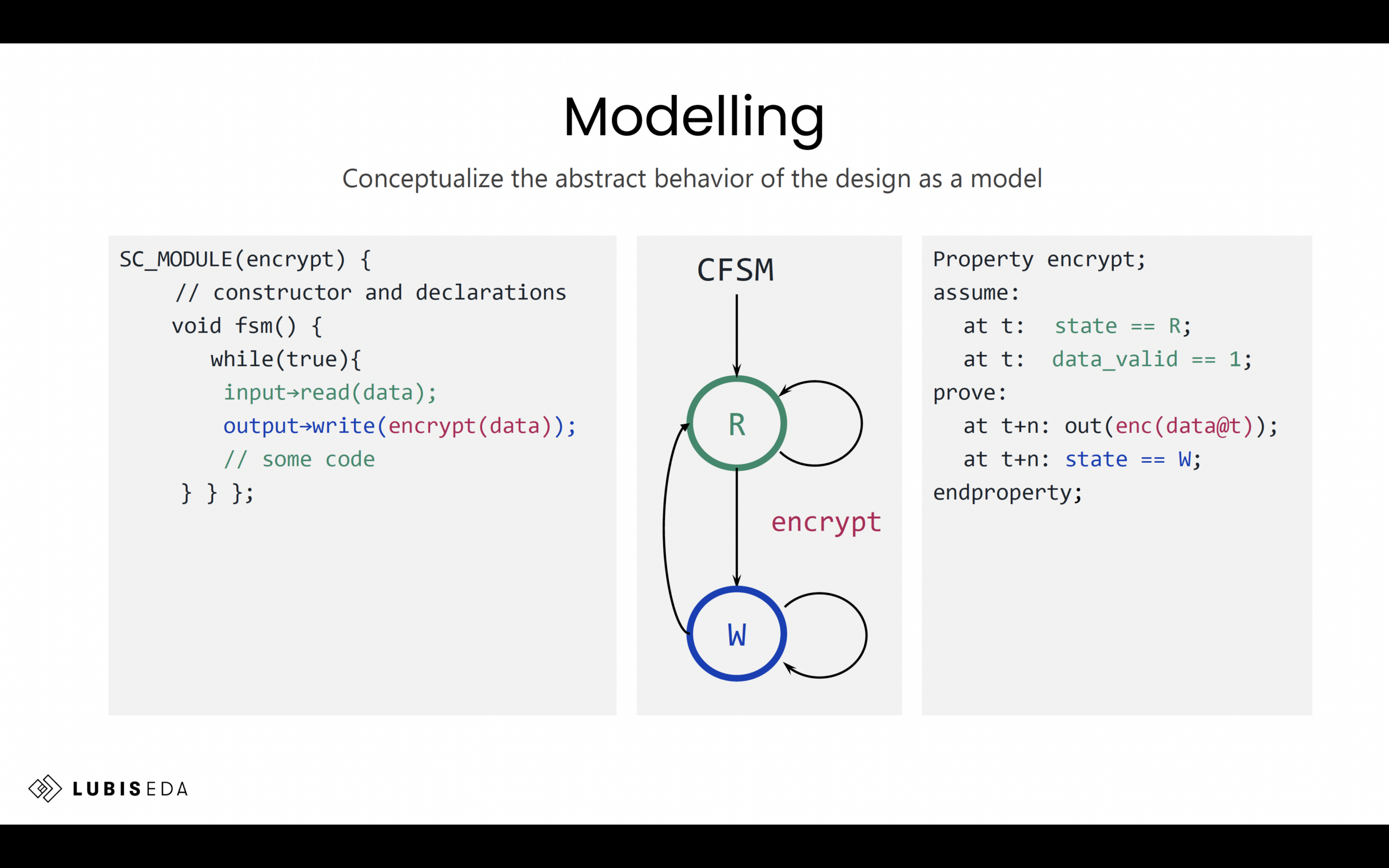 Assertion-First Hardware Design and Formal Verification ServicesGenerative AI has transformed software development, enabling entire…Read More
Assertion-First Hardware Design and Formal Verification ServicesGenerative AI has transformed software development, enabling entire…Read More TSMC's Customized Technical Documentation Platform Enhances Customer ExperienceTaiwan Semiconductor Manufacturing Company, the world's leading dedicated…Read More
TSMC's Customized Technical Documentation Platform Enhances Customer ExperienceTaiwan Semiconductor Manufacturing Company, the world's leading dedicated…Read MoreDAC 2017: How Oracle does Reliability Simulation when designing SPARC
Last week at #54DAC there was a talk by Michael Yu from the CAD group of Oracle who discussed how they designed their latest generation of SPARC chips, with an emphasis on the reliability simulations. The three features of the latest SPARC family of chips are:
- Security in silicon
- SQL in silicon
- World’s fastest microprocessor
New Concepts in Semiconductor IP Lifecycle Management
Right before #54DAC I participated in a webinar with Methodics on “New Concepts in Semiconductor IP Lifecycle Management” with Simon Butler, CEO of Methodics, Michael Munsey, Vice President of Business Development and Strategic Accounts, and Vishal Moondhra, Vice President of Applications. Thewebinar introduced… Read More
Open-Silicon SerDes TCoE Enables Successful Delivery of ASICs for Next-generation, High-Speed Systems
With 5G cellular networks just around the corner, there is an ever-increasing number of companies working to bring faster communications chips to the market. Data centers are now deploying 100G to handle the increased bandwidth requirements, typically in the form of four 28Gbps channels and that means ASIC designers are looking… Read More
The Real Reason Siemens Bought Mentor!
The Siemens purchase of Mentor last year for a premium $4.5B was a bit of a shock to me as I have stated before. I had an inkling a Mentor acquisition was coming but Siemens was not on my list of suitors. The reviews have been mixed and the Siemens commitment to the IC EDA market has been questioned so I spent some time on this at #54DAC.
First… Read More
First Thoughts from #54DAC!
This was my 34[SUP]th[/SUP] DAC, yes 34. It is a shame blogging did not exist back then because I would have liked to have read thoughts from my eager young mind, or maybe not. The first thing that struck me this year is the great content. Before DAC I review the sessions I want to see and this year there were many more than I had time for. … Read More
Ransomware of $1 Million Crushes Company
A South Korean web hosting company struggles for survival after agreeing to pay a ransomware extortion of $1 million to hackers.
New Record for Ransomware
Nayana, the South Korean web hosting firm, suffered a ransomware attack that resulted in 153 infected Linux servers. The resulting data that was encrypted by the malware impacted… Read More
Safety EDA
It takes courage and perhaps even a little insanity to start a new EDA venture these days – unless you have a decently differentiated value proposition in a hot market. One company that caught my eye, Austemper, seems to measure up to these standards (though I can’t speak to the insanity part). They offer EDA tooling specifically… Read More
Amazon eating Whole Foods is nothing as entire industries are about to become toast
I doubt that Google and Microsoft ever worried about the prospect that a book retailer, Amazon, would come to lead one of their highest-growth markets: cloud services. And I doubt that Apple ever feared that Amazon’s Alexa would eat Apple’s Siri for lunch.
For that matter, the taxi industry couldn’t have imagined that a Silicon … Read More
Electronics upturn boosting semiconductors
Production of electronics has been accelerating in the last several months, contributing to strong growth in the semiconductor market. China, the largest producer of electronics, has seen three-month-average change versus a year ago (3/12 change) accelerate from below 10% for most of 2016 to 14.5% in April 2017. China’s April… Read More





Quantum Computing Technologies and Challenges