Hardware-assisted verification has been with us (commercially) for around 20 years and at this point is clearly mainstream. But during this evolution it split into at least two forms (emulation and prototyping), robbing us of a simple choice – to hardware-assist or not to hardware-assist (that is the question). Which in turn … Read More
 Accellera Strengthens Industry Collaboration and Standards Leadership at DVCon U.S. 2026At DVCon U.S. 2026, Accellera Systems Initiative reinforces…Read More
Accellera Strengthens Industry Collaboration and Standards Leadership at DVCon U.S. 2026At DVCon U.S. 2026, Accellera Systems Initiative reinforces…Read More Ceva Wi-Fi 6 and Bluetooth IPs Power Renesas’ First Combo MCUs for IoT and Connected HomeThe rapid expansion of IoT, smart home, and…Read More
Ceva Wi-Fi 6 and Bluetooth IPs Power Renesas’ First Combo MCUs for IoT and Connected HomeThe rapid expansion of IoT, smart home, and…Read More Why PDF Solutions Is Positioning Itself at the Center of the Semiconductor EcosystemThe semiconductor industry is on track to exceed…Read More
Why PDF Solutions Is Positioning Itself at the Center of the Semiconductor EcosystemThe semiconductor industry is on track to exceed…Read More Chiplets Reach an Architectural Turning Point at Chiplet Summit 2026The semiconductor industry’s transition toward chiplet-based architectures is…Read More
Chiplets Reach an Architectural Turning Point at Chiplet Summit 2026The semiconductor industry’s transition toward chiplet-based architectures is…Read MoreCTO Interview: Ty Garibay of ArterisIP
ArterisIP has been a SemiWiki subscriber since the first year we went live. Thus far we have published 61 Arteris related blogs that have garnered close to 300,000 visits making Arteris and NoC one of our top attractions, absolutely.
One of the more newsworthy announcements this week is the addition of Ty Garibay to the Arteris executive… Read More
Breakfast with Aart de Geus and the Foundries!
Being the number one EDA and the number one IP company does have its advantages and the resulting foundry relationships are a clear example. One of the DAC traditions that I truly enjoy is the Synopsys foundry breakfasts. Not only does Synopsys welcome scribes, they reserve a table up front for us and Synopsys CEO Aart de Geus has been… Read More
Project Management Tools for Analog IP Verification
Large SoC design teams typically have a cadre of project managers to oversee all facets of functional verification — e.g., specification, reviews, directed testbench development, automated (pseudorandom) testcase generation, HDL coverage measurement and reporting, and bug identification/tracking database management.… Read More
Embedding FPGA IP
The appeal of embedding an FPGA IP in an ASIC design is undeniable. For much of your design, you want all the advantages of ASIC: up to GHz performance, down to mW power (with active power management), all with very high levels of integration with a broad range of internal and 3[SUP]rd[/SUP]-party IP (analog/RF, sensor fusion, image/voice… Read More
Webinar: Mobile Device Companies Get New Sensor Interconnect Standard
I’ve been a mobile device user since the 1980’s when the Motorola brick phone was introduced, so I’ve seen an increasing amount of sensors added to each new generation of mobile phones over the years. One big challenge to both sensor companies and fabless semiconductor companies designing SoCs for mobile devices… Read More
CEO Interview: Michel Villemain of Presto Engineering, Inc.
One of the many advantages of being part of SemiWiki is the interesting people we get to meet. As I have mentioned before, the semiconductor industry is home to many brilliant and successful people and Dr. Michel Villemain is certainly one of them. Michel is the founder and CEO of Presto Engineering and it is interesting to note that… Read More
Fix Lauren: No War on Cars!
We have gotten to the point with automotive safety where we are happy to hear that ONLY 18,000 people died on the nation’s highways in the first six months of 2017. That’s right. That is good news – 100+ people were killed every day so far this year in, by or as a result of cars.
Apple iPhone Super Cycle Update!
In 2014 Apple released the iPhone 6 which included the first SoC built on a TSMC (20nm) process. This phone started what many call a “Super Cycle” of people upgrading. According to Apple, they now have more than 1 billion activated devices so this super cycle could be seriously super, absolutely.… Read More
Getting More Productive Coding with SystemVerilog
HDL languages are a matter of engineering personal preference and often corporate policy dictates which language you should be using on your next SoC design. In the early days we used our favorite text-based editor like Vi or Emacs, my choice was Vi. The problem with these text-based editors of course is that they really don’t… Read More

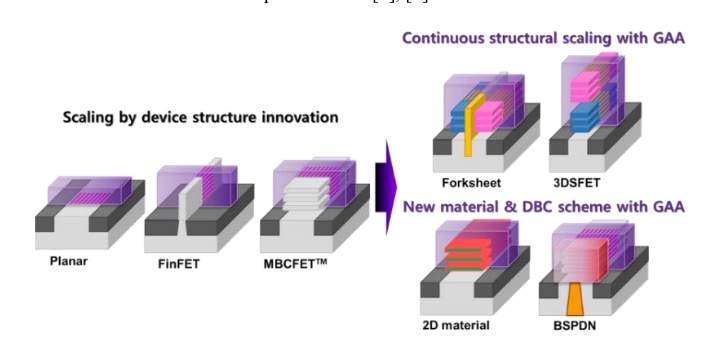




TSMC vs Intel Foundry vs Samsung Foundry 2026