Smart card business is now more than 25 years old, we can assess that the semiconductor industry is able to protect the chips used for smart card or SIM application with a very good level (unfortunately, it’s very difficult to get access to the fraud percentage linked with smart cards, as bankers really don’t like to communicate on this topic!). The various techniques and algorithms to protect chips against attacks have proven to be efficient, but just keep in mind that security experts like Alain Merle (Dr of security with CEA-LETI) evaluate the weight of good security level to be 50% of the IC total cost, for a smart card or SIM.
Now the problem is moving from a single chip dedicated to SIM (or smart card), that we know how to best protect against fraud, to the embedded version of this chip, integrated as one of the functions integrated into an application processor SoC. We are talking about embedded SIM (eSIM) and any function supporting mobile payment being integrated into a SoC targeting mobile, IoT and automotive applications. How to best protect it from the various possible attacks?
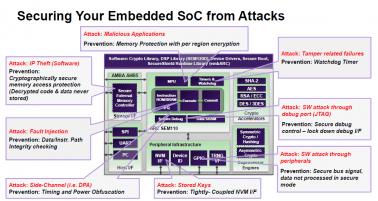
Synopsys has developed pre-verified DesignWare ARC Secure IP Subsystem to provide a trusted hardware and software SoC environment. This subsystem is created around the new ARC SEM110, or ARC SEM120D (the D stands for DSP extension).
The ARC SEM is an ultra-low power security processor with SecureShield technology, enabling creation of Trusted Execution Environment (TEE) and protecting against side-channel attacks and data breaches. Synopsys offers cryptography options to accelerate encryption for a range of algorithms including AES, SHA-256, RSA and ECC. To protect the instruction code and data, the code and data are stored encrypted in the memories, embedded or external and secured instruction and data controllers provide external memory access protection and runtime tamper detect. This secure external memory controller is a licensable product option.
SoC architect can implement security at S/W level only, using subsystem software including NIST-validated crypto library (for non US: NIST stand for National Institute of Standard Technology), secure boot and SecureShield runtime library (embARC), or complement with H/W engines like Symmetric Crypto/Hashing or Asymmetric Crypto coprocessors.
ARC SEM110 and SEM120D are well suited for secure element implementations, like eSIM or eUICC. UICC being the new generation of SIM, able to support multiple applications, like USIM (to identify you and your phone plan to your service provider) or ISIM (to secure mobile access to multimedia services, and non-telecom applications such as payment).
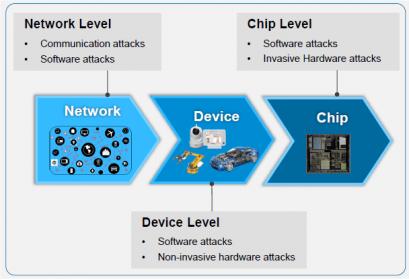
At the chip level, the number of potential attacks is vast, as we can see on the above picture. During communication, we can mention sniffing of sensitive data like passwords, direct remote attacks via backdoors or indirect via remotes nodes. Software is well-known for the sensibility to malware (viruses or rootkits), but it can also a vector to exploit buffer/stack overflows, or for privilege level tampering. Hardware can be sensible to invasive attacks like decapsulation or probing (even if these can also be used by analyst!) and non-invasive like side-channel of access to the inside by using debug ports.
ARC SEM security processor has been designed to be immune to these attacks, hardware or software. SecureShield offers multiple isolated execution context. Side-channel protection is realized by defining an uniform instruction timing, and via timing and power randomization. The processor pipeline is made tamper-resistant by in-line instruction, data and address scrambling. Error detection and parity has been implemented for memories and registers. Even the debug functionality has been secured to prevent non-invasive side-channel attacks. Integrated watchdog timer detects system failures, including tampering.
You shouldn’t be surprised to learn that ARC SEM has been the analysts’ choice in 2016 for the Linley Group Best Processor IP award!
The ARC Secure IP Subsystem is available now.
- Learn more about DesignWare ARC Subsystems
- Learn more about ARC SEM Processors and SecureShield technology
- Learn more about Synopsys DesignWare Security IP Solutions
From Eric Esteve from IPnest
Share this post via:






Comments
There are no comments yet.
You must register or log in to view/post comments.