One of the Designer Track at this year’s DAC focused on the popular topic of automotive electronics. The title was particularly on-point, The Modern Automobile: A Safety and Security “Hot Zone”. The session was chaired by Debdeep Mukhopadhyay, a Professor at the Indian Institute of Technology in Kharagpur.
This special, invited session can be summarized as follows:
The advent of the Automotive 2.0 era has driven increased integration of electronics and networking into the conventional automobile. The modern electrified automobile can be simply viewed as a connected, embedded system on wheels. Not surprisingly, safety and security concerns are coming increasingly to the forefront. This special session will focus on answers to multiple questions related to automotive safety and security – what are the issues at the system level, what are the standards available today, how do safety and security co-exist (or collide!), and what does it mean to build and verify security in our chips.
Presenters included:
- Chuck Brokish, Director of Transportation Business Development, Green Hills Software LLC
- David Foley, Semiconductor Architect, Texas Instruments, Inc.
- Steve Carlson, Director, Cadence Design Systems
While all the presentations were relevant and on-point, I’d like to focus on the presentation from Steve Carlson at Cadence. I’ve known Steve for a long time. His career began at LSI Logic, arguably the birthplace of ASIC. Steve began by pointing out the magnitude of the cyber security problem. The attacks are ubiquitous, everything from shipping vessels to pacemakers. Governments are getting involved and we can expect lots more compliance requirements.
If one looks at the attack vectors for this problem, a lot of it is at the hardware or hardware/software interface level. So, EDA should be able to help. Said another way, after all the time and money invested in software security, it’s time for hardware to take center stage.
Steve pointed out that we’ve seen a lot of work in the functional safety area regarding standards compliance and certification. These techniques will transfer now to the security domain. Steve talked about pre-silicon attack verification – basically a way to validate the robustness of security layers with simulated attacks on the design before tapeout. Formal methods hold great promise for this activity as they are not dependent on input vectors and the associated “blind spots” they can bring. More on this in a moment.
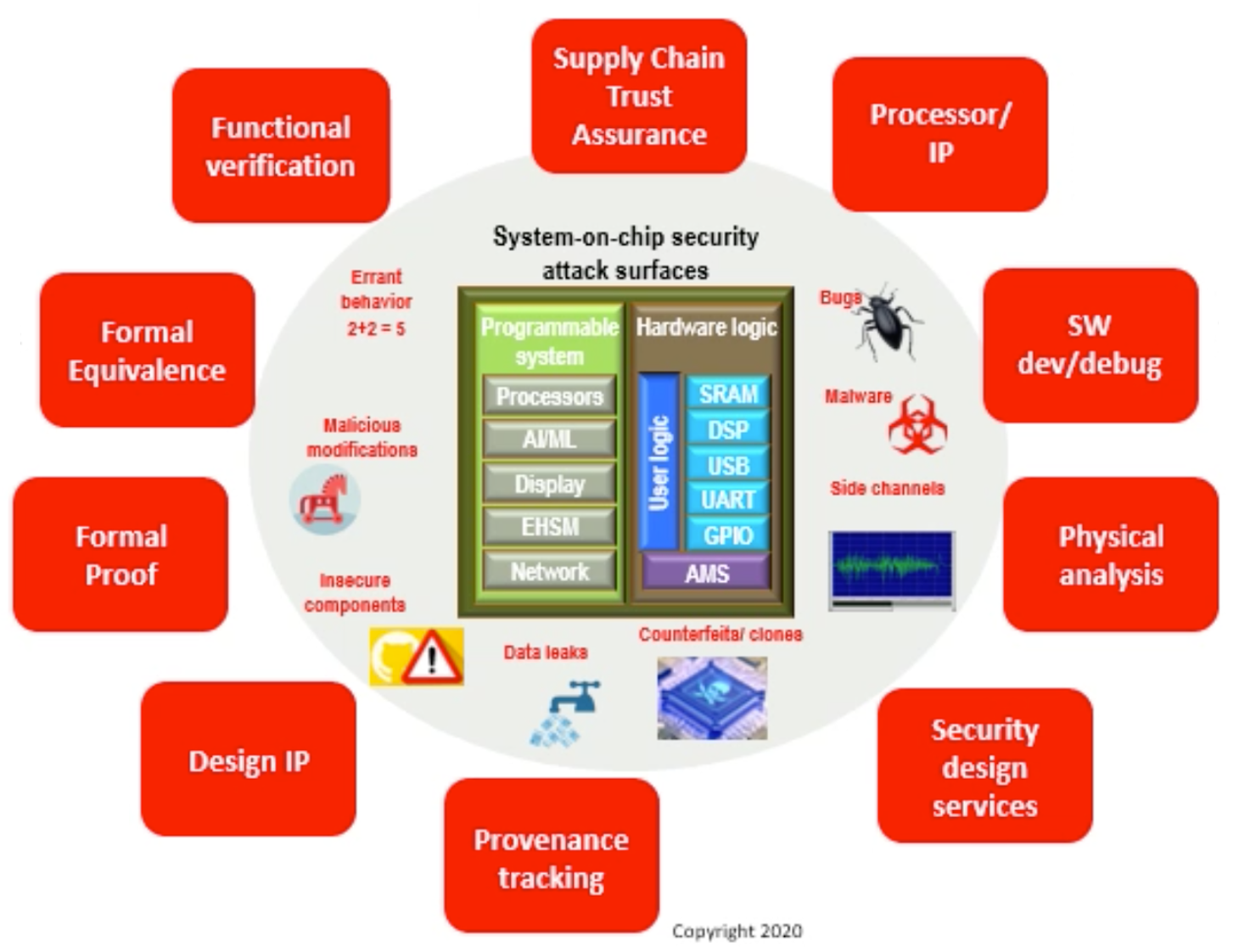
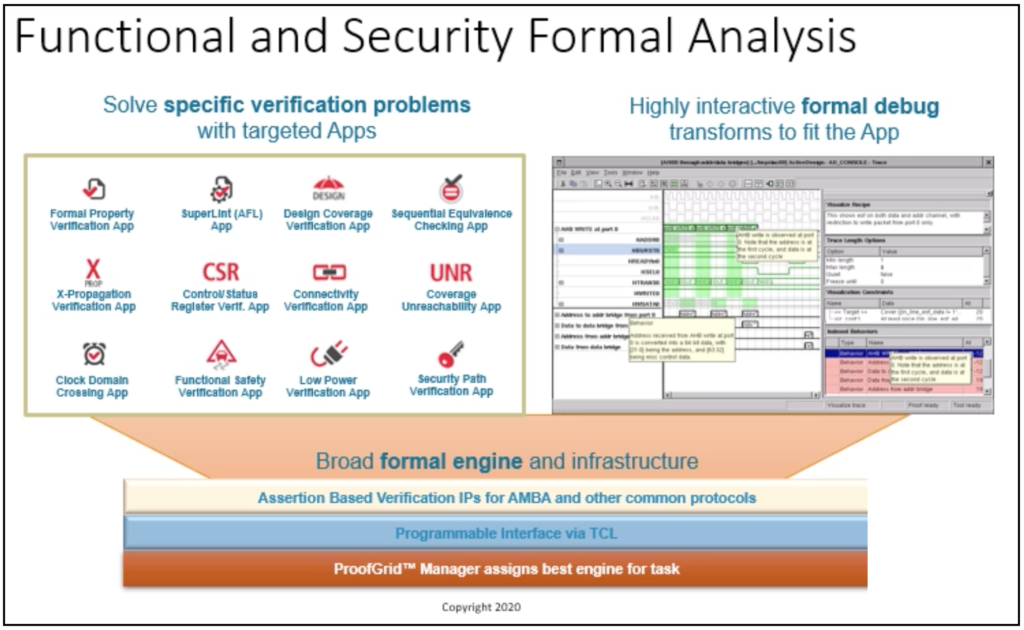
A comprehensive overview of the various attack vectors and the countermeasures EDA offers was presented. This diagram really drove home the breadth of the problem. It’s included at the top of this post. Rather than spend an hour on this chart (DAC presentations are short) Steve chose to focus on formal methods. It turns out there are a number of specialized formal security applications that can prove things like data integrity, so this is a promising approach to verify compliance. The breadth of this technology is summarized in the diagram below.
Steve ended his discussion with a vision of top-down verification of hardware security. Similar to approaches used for early hardware/software verification, he advocated a top-down approach to model the entire system in package, including the chip, interposer, package and board. This will allow the development of attack tests at a high level that can be used later in the design flow to verify the robustness of the system.
There are industry-level efforts to advance the cause as well. Cadence is working with several organizations to advance the state of testing and compliance, including Accellera. Security is a daunting task; it was good to hear about some positive momentum from Cadence.
If you have a DAC pass, I encourage you to watch this entire designer track session. I believe the material will be available online for an extended period of time. You can find this session on The Modern Automobile: A Safety and Security “Hot Zone” here.
Also Read
DAC Panel: Cadence Weighs in on AI for EDA, What Applications, Where’s the Data?
#57DAC – Panel Discussion of High Level Synthesis
Cadence Defines a New Signoff Paradigm with Tempus PI
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.