 Yesterday was the Mentor users’ group U2U. As usual, Wally Rhines gave the keynote, this year entitled Secure Silicon, Enabler for the Internet of Things. Wally started off saying it was a challenge to find a new angle. The number of news articles on cloud computing has exploded from nothing to 72,000 last year. On IoT from nothing to 42,000 last year. Cybersecurity from nothing to 67,000. In fact, if you want to really fill up your calendar then you can go to a conference on one of these subjects pretty much every day between now and the end of the year.
Yesterday was the Mentor users’ group U2U. As usual, Wally Rhines gave the keynote, this year entitled Secure Silicon, Enabler for the Internet of Things. Wally started off saying it was a challenge to find a new angle. The number of news articles on cloud computing has exploded from nothing to 72,000 last year. On IoT from nothing to 42,000 last year. Cybersecurity from nothing to 67,000. In fact, if you want to really fill up your calendar then you can go to a conference on one of these subjects pretty much every day between now and the end of the year.
Estimates of the size of the IoT market range from $300B to $14.4T (quite a range) and for cybersecurity from $113B to $3T. Is that really plausible? Well, to take just one famous example, the Target credit card theft:
- 40M credit card numbers stolen
- 70M credit cards stolen with address, email and phone
- -30% drop in Target’s business after security breach
- -46% drop in Target’s profits in Q4 2013 (YoY)
- $200M estimated cost for banks to reissue 21M credit cards (not sure why the number of cards is so much lower than the number stolen)
- $100M estimated cost for Target to update terminals to chip-and-PIN cards

Earlier in the week I wrote about your refrigerator attacking you. It turns out that the security weakness at Target was not a refrigerator but surprisingly close: they accessed the network through an air-conditioning subcontractor. This is just one well-known security breach. There are lots more: Stuxnet worm in the Iranian centrifuges, Syrian army hacking Forbes, AP’s Twitter account hacked and a multi-billion drop in the stock market on a fake tweet about Obama being injured in explosions at the White House.
I wrote a joke article about a Sonics/eSilicon chip recently here. But all the security stuff in it is real: the NSA did steal all the PIN card passwords for millions of mobile phones, people do get across air gaps using compromised thumb drives and so on. In fact, Wally had some data on a test done by the Department of Homeland Security where they dropped thumb drives in the parking lots of government buildings. Result: 60% were picked up and plugged into computers in the buildings and if the thumb drive had a DHS logo on it then a staggering 90% were plugged in.
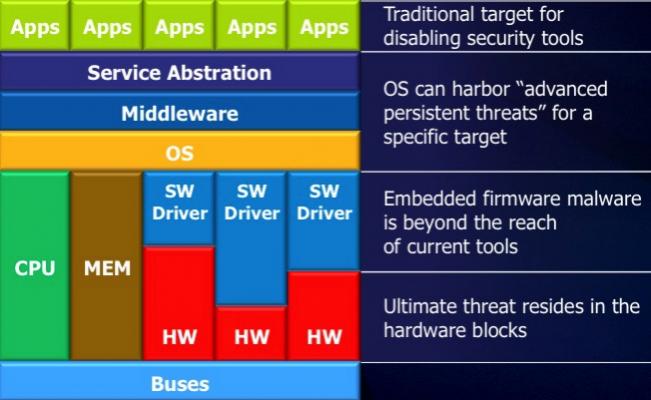
There are three main levels of security that designers need to worry about:
 Firstly there are side-channel attacks, which is extracting information (typically encryption keys) from chips using either passive approaches such as differential power analysis or electromagnetic analysis. By inspecting the thermal and electric aspects of the chip, or by inducing faults with lasers or electro-magnetically. To date, most of the attacks have been focused on the chips inside credit cards in most of the world, finally starting to come into mainstream use in the US too. But there are also attacks on set-top boxes and apparently the manufacturers judge how good their security is by how long it takes before cracked boxes are available on eBay. If they make it to two years that is regarded as the gold standard.
Firstly there are side-channel attacks, which is extracting information (typically encryption keys) from chips using either passive approaches such as differential power analysis or electromagnetic analysis. By inspecting the thermal and electric aspects of the chip, or by inducing faults with lasers or electro-magnetically. To date, most of the attacks have been focused on the chips inside credit cards in most of the world, finally starting to come into mainstream use in the US too. But there are also attacks on set-top boxes and apparently the manufacturers judge how good their security is by how long it takes before cracked boxes are available on eBay. If they make it to two years that is regarded as the gold standard.
Solutions are starting to emerge by increasing randomness, fixed time algorithms, disguised structures to prevent reverse engineering and so on. But designers need to worry about simulating or emulating these attacks to defend against them before committing to silicon.
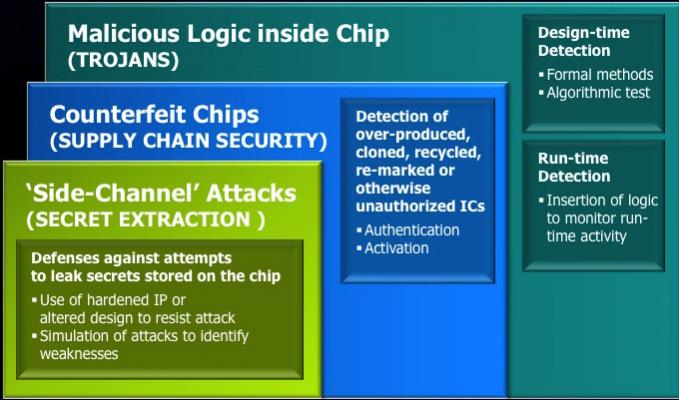
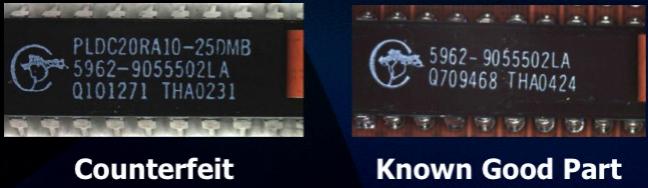
The second problem is counterfeit chips, which involves supply chain security. The problem is growing all the time and, despite people assuming it is a minor problem, it is already significant, and it doesn’t only affect high cost parts. The #1 reason it gets detected is when the parts do not work, but it is often very difficult to detect. Designers generally are not responsible for the supply chain management directly but there are things designers can do such as build on-chip odometers to measure use over time (so that fake chips cannot be recycled) or requiring chips to be activated with keys after manufacturing.
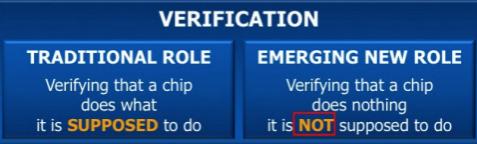
The biggest worry for designers is malicious logic getting inserted inside chips. Around a quarter of the IP blocks on the average SoC contains 3rd party IP along with 3rd party VIP. If the IP verifies with the VIP then the designer is happy. The block does what it is meant to. The new task that the designer is going to have to worry about is to check that the block does not do anything it is not meant to.
 The most vulnerable attack points that Wally identified were 3rd party IP and code re-use, complex 3rd party scripts (driving the EDA tools) and physical IP with the trojan already designed in.
The most vulnerable attack points that Wally identified were 3rd party IP and code re-use, complex 3rd party scripts (driving the EDA tools) and physical IP with the trojan already designed in.
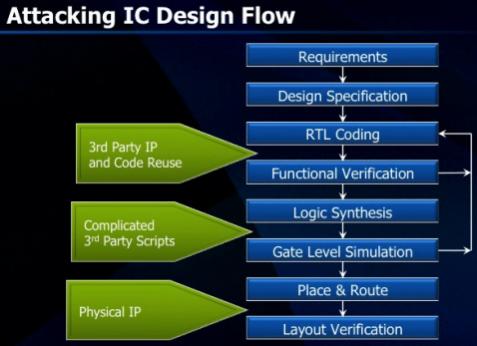
Wally reckons that the story will unfold like this:
- there is already an emerging customer demand for silicon authentication
- there are new standards that will force better validation, such as ISO 26262 for automotive
- but world will not change until there is a major event resulting in financial or physical harm, which will force
- semiconductor customers request certification from chip suppliers
- chip suppliers scramble to test and certify existing IC’s
- procedures implemented to screen IP blocks used in designs
- design methodologies modified to add countermeasures to most designs
- trojan detection and prevention becomes a design process
Perhaps the most worrying thing Wally said is that although you don’t read on the internet about trojans being inserted into hardware, when he meets people in the right US government departments they say it happens all the time. Wally’s assumption is that they are already doing it themselves, and they also assume the other guys are doing it. Given what we have learned about the NSA in the last year it would be more surprising if they were not. So it is not just a theoretical problem to worry about years in the future, it is already happening.
Share this post via:






Comments
0 Replies to “Are There Trojans in Your Silicon? You Don’t Know”
You must register or log in to view/post comments.