Privacy and security have always been a concern when it comes to computing. In prior decades for most people this meant protecting passwords and locking your computer. However, today more and more users are storing sensitive data in the cloud, where it needs to be protected at rest and while in motion. In a Synopsys webinar Dana Neustadter, Senior Marketing Manager for Security IP, cites figures from Skyhigh Networks that show as much as 21% of files uploaded to file sharing services contain sensitive data, such as medical, financial or personal information.
While we all feel that data centers and related infrastructure are secure, if you have ever watched a video of a “penetration tester”, you will see just how easy it is for bad actors to physically access some sites. If you want to see one of these videos, search for “pen tester” on Youtube. Fortunately, the industry is responding to this issue by adding security to specifications such as PCIe and CXL (Computer eXpress Link). These additions go a long way toward meeting the requirements of new laws and regulations which are creating requirements for system security where there is sensitive data.
Security for data in motion in PCIe and CXL, of course, depends on proper on chip security within SOCs. A trusted execution environment should offer power-on, runtime and power off security, through a Hardware Security Module (HSM). The real key to PCIe and CXL security is the addition of an Integrity and Data Encryption (IDE) component. In the Synopsys webinar Dana does a thorough job of describing the function and operation of an IDE in conjunction with authentication and key management. The PCIe 5.0/6.0 and CXL 2.0/3.0 specifications call for this additional functionality to afford increased security.
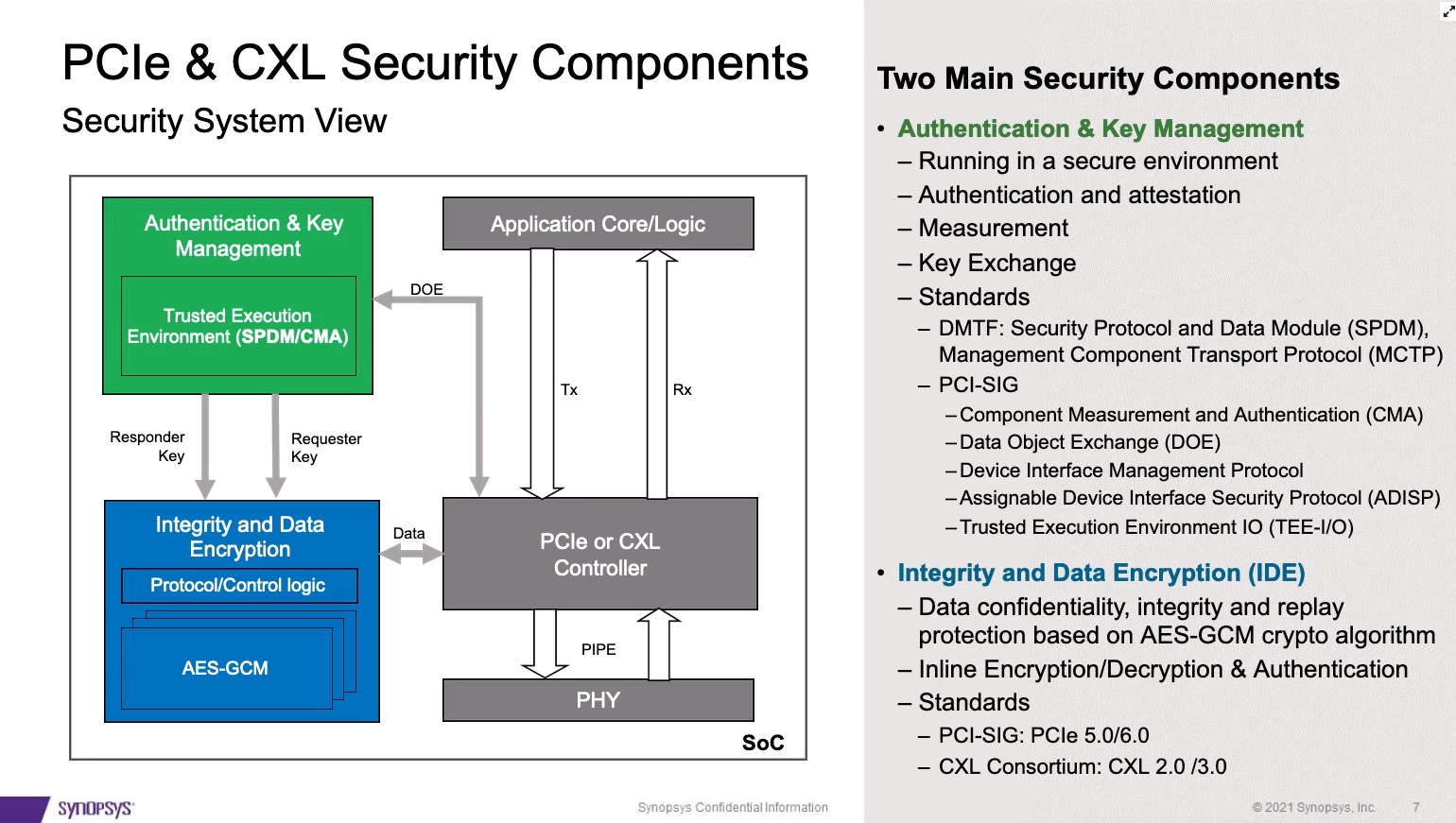
The IDE is intended to sit within the PCIe Transaction Layer. This is a critical aspect of the design, because while added security is an essential requirement, it needs to have minimal impact on latency and performance. Right now, the specs allow for IDEs in the handling of TLP streams. FLIT mode will be included in the PCIe 6.0 release. Packets are protected by AES-GCM with 256-bit keys and 96-bit MAC tags. Ideally the addition of IDE should be plug and play, and this is the case for the Synopsys PCIe IDE and Controller IP. Another important element is that FIPS 140-3 certification is becoming important in the industry and should be supported through a certification test mode.
CXL operation and support mirrors that of PCIe. Dana includes the flow for both PCIe and CXL when IDE is included. Of course, with CXL there are some differences because of the three types of protocols it supports. IP for the CXL IDE needs to include containment and skid modes, and additions for PCRC when running CXL.cache/mem. Dana also discusses the ins and outs of key management for the large number of streams that can be operating in a design.
This webinar is comprehensive in that it discusses the needs and requirements for PCIe and CXL security in cloud applications. It also goes in depth on the components, architecture and related standards that are supported in the Synopsys DesignWare IP. Near the conclusion of the webinar, Dana shows how several different SOCs for AI or networking can be constructed largely from IP available from Synopsys. The webinar is available for replay on the Synopsys website.
Also read:
High-Performance Natural Language Processing (NLP) in Constrained Embedded Systems
Lecture Series: Designing a Time Interleaved ADC for 5G Automotive Applications
Synopsys’ ARC® DSP IP for Low-Power Embedded Applications
Share this post via:





Comments
There are no comments yet.
You must register or log in to view/post comments.