You are currently viewing SemiWiki as a guest which gives you limited access to the site. To view blog comments and experience other SemiWiki features you must be a registered member. Registration is fast, simple, and absolutely free so please,
join our community today!
WP_Term Object
(
[term_id] => 95
[name] => Automotive
[slug] => automotive
[term_group] => 0
[term_taxonomy_id] => 95
[taxonomy] => category
[description] =>
[parent] => 0
[count] => 777
[filter] => raw
[cat_ID] => 95
[category_count] => 777
[category_description] =>
[cat_name] => Automotive
[category_nicename] => automotive
[category_parent] => 0
[is_post] =>
)
The latest reliability report from Consumer Reports which dumped on domestics and rained glory upon Asian imports highlighted a conundrum facing car makers. The more effort car makers put into innovation, the greater the risk of consumer confusion, system failure and lousy reliability scores.
The picture is even worse if one… Read More
As new automotive Advanced Driver Assistance System (ADAS) based product releases intensifies while a more stringent set of safety requirements are mandated, it is not surprising that subsystem and electronic suppliers are looking for pre-designed and ISO 26262 certified IP that can address both imperatives of schedule and… Read More
The cybersecurity of automobiles has become an increasingly critical issue in the context of autonomous vehicle development. While creators of autonomous vehicles may have rigorous safety and testing practices, these efforts may be for naught if the system are compromised by ethical or unethical hackers.
Establishing cybersecurity… Read More
I think we’re all familiar with the cloud/edge debate on where intelligence should sit. In the beginning the edge devices were going to be dumb nodes with just enough smarts to ship all their data to the cloud where the real magic would happen – recognizing objects, trends, need for repair, etc. Then we realized that wasn’t the best… Read More
Tesla Motors CEO Elon Musk pulled a rabbit out of his hat last month making thousands of cars vanish and converting reports of production and delivery hell into market leadership for premium sedan deliveries. Following SEC legal action and a podcast where he appeared to be drinking scotch and smoking marijuana and after surrendering… Read More
In the wake of TSMC’s recent Open Innovation Platform event, I spoke to Frank Ferro, Senior Director of Product Management at Rambus. His presentation on advanced memory interfaces for high-performance systems helped to shed some light on the evolution of system memory for leading edge applications. System implementers now… Read More
Tom Dillinger and I attended the Silvaco SURGE 2018 event in Silicon Valley last week with several hundred of our semiconductor brethren. Tom has a couple blogs ready to go but first let’s talk about the keynote by Silvaco CEO David Dutton. David isn’t your average EDA CEO, he spent the first 8 years of his career at Intel then spent … Read More
The Cadence Tensilica DNA100 DSP IP core is not a one-size-fits-all device. But it’s highly modular in order to support AI processing at the edge, delivering from 0.5 TMAC for on-device IoT up to 10s or 100 TMACs to support autonomous vehicle (ADAS). If you remember the first talks about IoT and Cloud, a couple of years ago, the IoT … Read More
The ISO 26262 standard defines four Automotive Safety Integrity Levels (ASILs), from A to D, technically measures of risk rather than safety mechanisms, of which ASIL-D is the highest. ASIL-D represents a failure potentially causing severe or fatal injury in a reasonably common situation over which the driver has little control.… Read More
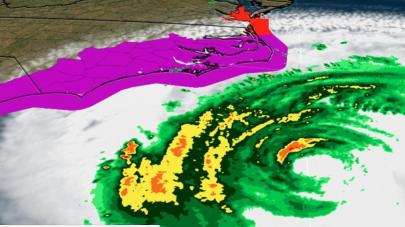
Here we go again. A hurricane is closing in on the U.S. East Coast and General Motors’ OnStar connected car team – now part of something called Global Connected Consumer Experience – is AWOL.
While mandatory evacuations have been ordered and two-way highway connections to the coast have been switched to single… Read More






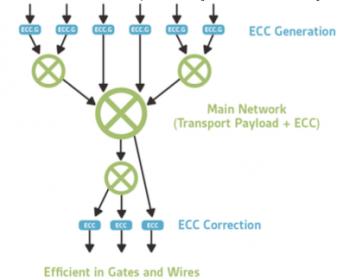
Semidynamics Unveils 3nm AI Inference Silicon and Full-Stack Systems