An attack on Dyn (a DNS service provider) through a distributed denial of service (DDOS) attack brought down Github, Amazon and Twitter for a while and is thought to have been launched through IoT devices. Hangzhou Xiongmai, a provider of webcams and the most publicly pilloried source of weakness in the attack is now recalling all… Read More
Tag: security
End-to-End Secure IoT Solutions from ARM
ARM announced today a comprehensive suite of solutions for IoT support, from IP optimized for applications in this space all the way to cloud-based support to manage edge devices in the field. Their motivation is to provide a faster path to secure IoT, from the chip to the cloud. One especially interesting component of this solution… Read More
Phish Finding
I wrote recently on the biggest hole in security – us. While sophisticated hacks on hardware and software make for good technology reading, fooling users into opening the front door remains one of the easiest and lowest cost ways for evil-doers to break into our systems. And one of the more popular ways to fool us is phishing in all … Read More
We Have Met the Enemy (of Security) and It Is Us
(With apologies to Pogo.) For all the great work that we are seeing in improving both software and hardware security, we – not the technology – are in many ways the weakest link in the security chain. Recent reports indicate we are surprisingly easy to fool, despite our much proclaimed awareness of risks.
In a recent experiment at … Read More
Semi execs look at IoT tradeoffs a bit differently
What happens when you get a panel of four executives together with an industry-leading journalist to discuss tradeoffs in IoT designs? After the obligatory introductions, Ed Sperling took this group into questions on power, performance, and integration.… Read More
Lethal data injection a much bigger threat
Watching a spirited debate on Twitter this morning between Tom Peters and some of his followers reminded me of the plot of many spy movies: silently killing an opponent with a lethal injection of some exotic, undetectable poison. We are building in enormous risks in more and more big data systems.… Read More
Linley Mobile and Wearable Conference Drills into Rapidly Evolving Markets
Last week the Linley conference on mobile and wearables started with an overview and keynote address by the event’s namesake Linley Gwennap. His talk offered a few surprises and was informative all around. As you have seen recently reported here on SemiWiki, he sees smartphone shipments continuing to rise, but with a declining… Read More
SMART sensors with OTP memory for the IIoT
A few years back before IoT became the buzzword, the industrial automation community had already talking about “smart sensors” since the mid-1990s. The impetus for those discussions was IEEE 1451, a family of standards for adding intelligence and wireless communications to sensors so they could be incorporated into field networks.… Read More
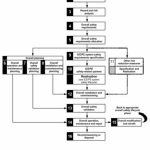
Can one process handle IIoT safety and security?
SemiWiki had another article recently making the case that in IoT applications, safety and security are intertwined, adding that both are important, but they are not the same thing. Mentor Graphics has weighed in with a new white paper trying to tie both issues to a methodology.
Industrial IoT – or IIoT as you’ll often see in shorthand… Read More
Safety Verification for Software
When automakers are thinking about the safety of an embedded system in a car, while it’s good to know the hardware has been comprehensively tested for safety-specific requirements, that isn’t much help if the software component of the system is not supplied with similarly robust guarantees.
The challenge is that the software … Read More