Advanced Micro Devices has already told us that 2016 was going to be the year of graphics, but the reality is that they also have a lot going on in their CPU and APU division as well. In fact, in addition to Advanced Micro Devices’s newly announced 7th Generation APUs in 2016, the company is also expected to launch their new Zen CPU cores… Read More
 CEO Interview with Dr. Raj Gautam Dutta of Silicon AssuranceDr. Raj Gautam Dutta is the Co-Founder and…Read More
CEO Interview with Dr. Raj Gautam Dutta of Silicon AssuranceDr. Raj Gautam Dutta is the Co-Founder and…Read More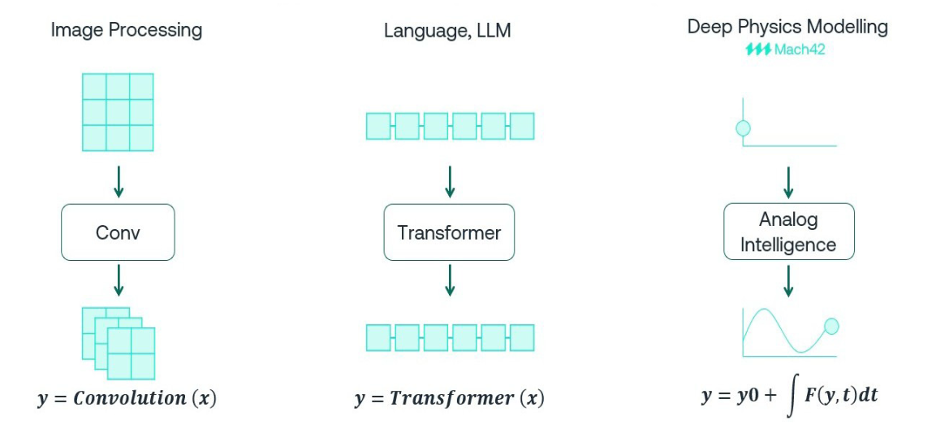 Beyond Transformers. Physics-Centric Machine Learning for AnalogPhysical AI is an emerging hot trend, popularly…Read More
Beyond Transformers. Physics-Centric Machine Learning for AnalogPhysical AI is an emerging hot trend, popularly…Read MoreCustom IC Layout Design at #53DAC
Last week at the #53DAC conference there was a lot of excitement in the air about custom IC design, especially at the luncheon that I attended on Tuesday from Synopsys where they had customers like STMicroelectronics, GSI Technology, Samsung Foundry and the Synopsys IP group talk about their experiences using the new Custom Compiler… Read More
Design for the System Age
Of late, it has become painfully obvious that the value of electronics is in the system. And since systems demand continuing improvement, increasing performance and decreasing cost (once partially guaranteed by semiconductor process advances) is now sought through algorithm advances – witness the Google TPU and custom… Read More
IBM on the way back and still crazy about IOT
IBM Update: IOT Transformation on Track?
There have been some interesting developments for Big Blue in the IOT space recently. Last time we reported on them, we were monitoring analysts’ worries about the semiconductor business and other divestures late last year. This year, it seems clear IBM is poised to create even more profitable… Read More
The Business of the Semiconductor Business, Part One: What Happened?
This is the first of an occasional series of articles on the semiconductor industry. Many column inches have covered industry consolidation and in this first article, I aim to explain how the industry reached this point. Later articles will cover subjects including China, joint ventures, emerging players like Brazil and Vietnam,… Read More
The Young and the Restless, PDA vs EDA, Photonic Soaps continued…
If you’ve followed my last article, The Guiding Light and Other Photonic Soaps, you read my comments about the use of waveguides to “guide the light” in photonic integrated circuits (PICs). This article continues the soap opera theme, this time with the Young and the Restless. My point here is that I am continually struck by the dichotomies… Read More
Because that is where the SoC power is
Still thinking of Sonics as just a network-on-chip company? They are pivoting to become an SoC realization company, and in their seminar at #53DAC in Austin we saw an entirely new plan focused on heisting an extremely valuable commodity everyone else is missing.… Read More
IoT Tutorial: Chapter 5 – IoT Clouds and Semantic Interoperability
Semantic Interoperability of IoT Data Streams: In the previous chapter of the IoT tutorial we introduced the concept of IoT and cloud computing convergence, while presenting concrete examples of IoT/cloud infrastructures, such as popular public IoT clouds (Xively.com, Thingspeak.com). These infrastructures enable the… Read More
IoT Tutorial: Chapter 4 – Internet of Things in the Clouds
The advent of cloud computing has acted as a catalyst for the development and deployment of scalable Internet-of-Things business models and applications. Therefore, IoT and cloud are nowadays two very closely affiliated future internet technologies, which go hand-in-hand in non-trivial IoT deployments. Furthermore, most… Read More
Is the Intel Cash Cow in Danger?
There was an interesting panel at the Silicon Summit sponsored by the Global Semiconductor Alliance (GSA) on “Designing for the Cloud.” It was led by Linley Gwennap (The Linley Group) with Ivo Bolsons (Xilinx), Ian Ferguson (ARM), and Steve Pawloski (Micron). Missing of course was Intel which derives close to 30% of its revenue… Read More

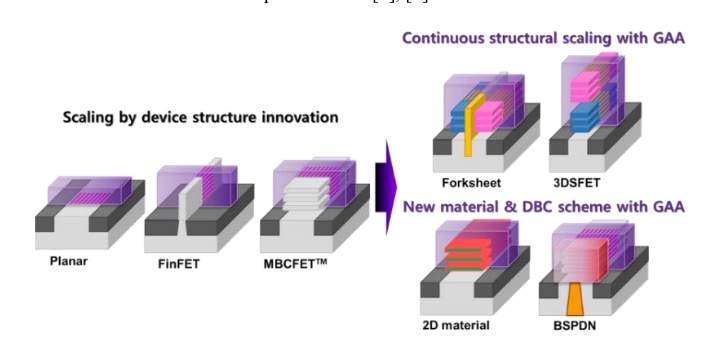


TSMC vs Intel Foundry vs Samsung Foundry 2026