I knew that the acronym for TFT meant Thin Film Transistors, but I hadn’t heard that FPD stands for Flat Panel Detectors. It turns out the FPD are solid-state sensors used in x-ray applications, similar in operation to image sensors for digital photography and video. I’ll be attending and blogging about what I learn… Read More
 Hardware is the Center of the Universe (Again)The 40-Year Evolution of Hardware-Assisted Verification — From…Read More
Hardware is the Center of the Universe (Again)The 40-Year Evolution of Hardware-Assisted Verification — From…Read More Smarter ECOs: Inside Easy-Logic’s ASIC Optimization EngineEasy-Logic Technology Ltd. is a specialized Electronic Design…Read More
Smarter ECOs: Inside Easy-Logic’s ASIC Optimization EngineEasy-Logic Technology Ltd. is a specialized Electronic Design…Read More The Name Changes but the Vision Remains the Same – ESD Alliance Through the YearsThe Electronic System Design Alliance (ESDA) has been…Read More
The Name Changes but the Vision Remains the Same – ESD Alliance Through the YearsThe Electronic System Design Alliance (ESDA) has been…Read More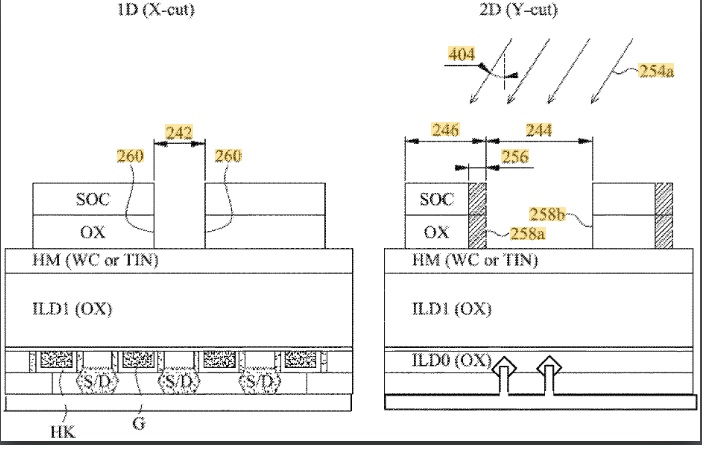 TSMC Process Simplification for Advanced NodesIn the modern world, the semiconductor industry stands…Read More
TSMC Process Simplification for Advanced NodesIn the modern world, the semiconductor industry stands…Read More CEO Interview with Juniyali Nauriyal of PhotonectJuniyali Nauriyal is the CEO and Co-Founder of…Read More
CEO Interview with Juniyali Nauriyal of PhotonectJuniyali Nauriyal is the CEO and Co-Founder of…Read MorePolishing Parallelism
The great thing about competition in free markets is that vendors are always pushing their products to find an edge. You the consumer don’t have to do much to take advantage of these advances (other than possibly paying for new options). You just sit back and watch the tool you use get faster and deliver better QoR. You may think that… Read More
Circuit Design: Anticipate, Analyze, Exploit Variations – Statistical Methods and Optimization
We are happy to publish book reviews, like this one from Dr. Georges Gielen of the KU Leuven in Belgium, for the greater good of the semiconductor ecosystem. So, if you have a semiconductor book you would like to review for fame not fortune let me know.… Read More
ARM’s (Back!) in FD-SOI. NXP’s Showing (Real!) Chips.
“Yes, we’re back,” Ron Moore, VP of ARM’s physical design group told a packed ballroom at the recent FD-SOI Symposium organized in Silicon Valley by the SOI Consortium. FD-SOI gives you a silicon platform that’s highly controllable, enables ultra-low power devices, and is really good with RF, said Ron Moore during his presentation,… Read More
Achieving Requirements Traceability from Concept through Design and Test
Excel is a wonderful, general purpose spreadsheet tool that lets me organize and analyze rows and columns of data into something meaningful, however it doesn’t know anything about requirements traceability for complex semiconductor projects. So why do so many engineering teams still rely upon Excel or custom, in-house… Read More
System-Level Power Estimation
When I first saw that Rob Knoth (Product Director at Cadence) had proposed this topic as a subject for a blog, my reaction was “well, how accurate can that be?” I’ve been around the power business for a while, so I should know better. It’s interesting that I jumped straight to that one metric for QoR; I suspect many others will do the same.… Read More
We Need Libraries – Lots of Libraries
It was inevitable that machine learning (ML) would come to EDA. In fact, it has already been here a while in Solido’s variation tools. Now it has found an even more compelling application – library characterization. Just as ML has radically transformed other computational arenas; it looks like it will be extremely disruptive here… Read More
Noise, The Need for Speed, and Machine Learning
Technology trends make the concerns with electronic noise a primary constraint that impacts many mainstream products, driving the need for “Design-for-Noise” practices. That is, scaling, and the associated reduction in the device operating voltage and current, in effect magnifies the relative importance of non-scalable… Read More
Dear Cadence: Calibre Didn’t Run Any Dracula Decks
After reading the Cadence blog post –“Dracula, Vampire, Assura, PVS: A Brief History” – Dr. Andrew Moore has written the below article where he helps readers get a sense as to what “the year of hell” was like, from one of the key individuals who lived it. Andrew also addresses and corrects some of the “urban legends”… Read More
Data Center Explosion Push for Fast Adoption of 25G
The data center rack server market is estimated to growat a high Compound Annual Growth Rate (CAGR) of 20% to reach $90 billion by 2021. Such growth is due to the significantly rise in the number of connected devices, the growth in the volume of data per device and theneed for quick processing of high-volume data. Much of these data … Read More








The Name Changes but the Vision Remains the Same – ESD Alliance Through the Years