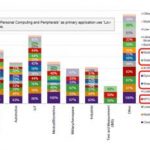
China has long been the largest market for semiconductors, accounting for over 50% of the global market for the last five years. China is now on track to become the largest semiconductor manufacturer in the next few years. The chart below shows China’s integrated circuit (IC) industry from 2010 to 2016, according to the China Semiconductor… Read More
 Revolutionizing Hardware Design Debugging with Time Travel TechnologyIn the semiconductor industry High-Level Synthesis (HLS) and…Read More
Revolutionizing Hardware Design Debugging with Time Travel TechnologyIn the semiconductor industry High-Level Synthesis (HLS) and…Read More Addressing Silent Data Corruption (SDC) with In-System Embedded Deterministic TestingSilent Data Corruption (SDC) represents a critical challenge…Read More
Addressing Silent Data Corruption (SDC) with In-System Embedded Deterministic TestingSilent Data Corruption (SDC) represents a critical challenge…Read More TSMC's 6th ESG AWARD Receives over 5,800 Proposals, Igniting Sustainability PassionTaiwan Semiconductor Manufacturing Company has once again demonstrated…Read More
TSMC's 6th ESG AWARD Receives over 5,800 Proposals, Igniting Sustainability PassionTaiwan Semiconductor Manufacturing Company has once again demonstrated…Read More Tiling Support in SiFive's AI/ML Software Stack for RISC-V Vector-Matrix ExtensionAt the 2025 RISC-V Summit North America, Min…Read More
Tiling Support in SiFive's AI/ML Software Stack for RISC-V Vector-Matrix ExtensionAt the 2025 RISC-V Summit North America, Min…Read More TSMC based 3D Chips: Socionext Achieves Two Successful Tape-Outs in Just Seven Months!Socionext’s recent run of rapid 3D-IC tape-outs is…Read More
TSMC based 3D Chips: Socionext Achieves Two Successful Tape-Outs in Just Seven Months!Socionext’s recent run of rapid 3D-IC tape-outs is…Read MoreARMing AI/ML
There is huge momentum building behind AI, machine learning (ML) and deep learning; unsurprisingly ARM has been busy preparing their own contribution to this space. They announced this week a new multi-core micro-architecture called DynamIQ, covering all Cortex-A processors, whose purpose is in their words, “to redefine … Read More
How to Design a Custom SoC with Analog, webinar from ARM and Tanner EDA
Leading edge SoC designs can contain billions of transistors, cost over $10M to design, and take over 18 months to deliver, but not all SoCs require that much complexity, cost and time. In fact, there is a growing class of SoC designs that integrate the popular ARM Cortex-M0 processor along with analog blocks that work with sensors… Read More
Top 10 Updates from the TSMC Technology Symposium, Part II
An earlier article described some of the technical and business highlights from the recent TSMC Symposium in Santa Clara (link). This article continues that discussion, with the top five updates.… Read More
Samsung Should Just Buy eSilicon Already!
As you all know I’m a big fan of the ASIC business dating back to the start of the fabless semiconductor transformation where anybody could send a design spec to an ASIC company and get a chip back. The ASIC business model also started the smart phone revolution when Samsung built the first Apple SoCs for the iPhones and iPads.
Today … Read More
Top 10 Updates from the TSMC Technology Symposium, Part I
Last week, TSMC held their 23rd annual technical symposium in Santa Clara. In the Fall, TSMC conducts the OIP updates from EDA/IP partners and customers. The theme of the Spring symposium is solely on TSMC’s technology development status and the future roadmap. Indirectly, the presentations also provide insight into … Read More
SRAM Optimization Saves Power on SOC’s and in Systems
Mobile device designers face the dilemma of reducing power and at the same time maintaining or increasing performance. Consumers will not tolerate increased battery life at the expense of performance. If it were otherwise, designers could simply dial back clock rates. Without this simple cure, the best way to reduce power for… Read More
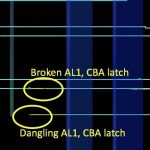
Quantum Resistance on the Edge
I’ve written recently about the trend to move more technology to the edge, to mobile devices certainly but also to IoT edge nodes. This is based particularly on latency, communications access and power considerations. One example is the move of deep reasoning apps to the edge to handle local image and voice recognition which would… Read More
Joe Costello and Other Luminaries Keynote at DAC
The most charismatic EDA CEO that I have ever witnessed is Joe Costello, who formed Cadence by merging SDA (Solomon Design Automation) and ECAD (known for DRC with Dracula). You will be impressed with his Monday keynote at DACon June 19th, starting at 9:15AM. Joe has long since left the EDA world and is currently the CEO of a company… Read More
Recipes for Low Power Verification
Synopsys hosted a tutorial on verification for low power design at DVCon this year, including speakers from Samsung, Broadcom, Intel and Synopsys. Verification for low power is a complex and many-faceted topic so this was a very useful update. There is a vast abundance of information in the slides which I can’t hope to summarize… Read More



Quantum Advantage is About the Algorithm, not the Computer