If you have read the white paper recently launched by Dolphin, “New Power Management IP Solution from Dolphin Integration can dramatically increase SoC Energy Efficiency”, you should already know about the theory. This is a good basis to go further and discover some real-life examples, like Bluetooth Low Energy (BLE) chip in … Read More
 Griffin Securities’ Jay Vleeschhouwer on EDA Acquisitions and StartupsJay Vleeschhouwer, Managing Director of Software Research at…Read More
Griffin Securities’ Jay Vleeschhouwer on EDA Acquisitions and StartupsJay Vleeschhouwer, Managing Director of Software Research at…Read More Security Coverage: Assuring Comprehensive Security in Hardware DesignAs hardware systems become increasingly complex and security…Read More
Security Coverage: Assuring Comprehensive Security in Hardware DesignAs hardware systems become increasingly complex and security…Read More Scaling 3D IC Technologies – Siemens Hosts a Meeting of the Minds at DAC3D IC was a very popular topic at…Read More
Scaling 3D IC Technologies – Siemens Hosts a Meeting of the Minds at DAC3D IC was a very popular topic at…Read More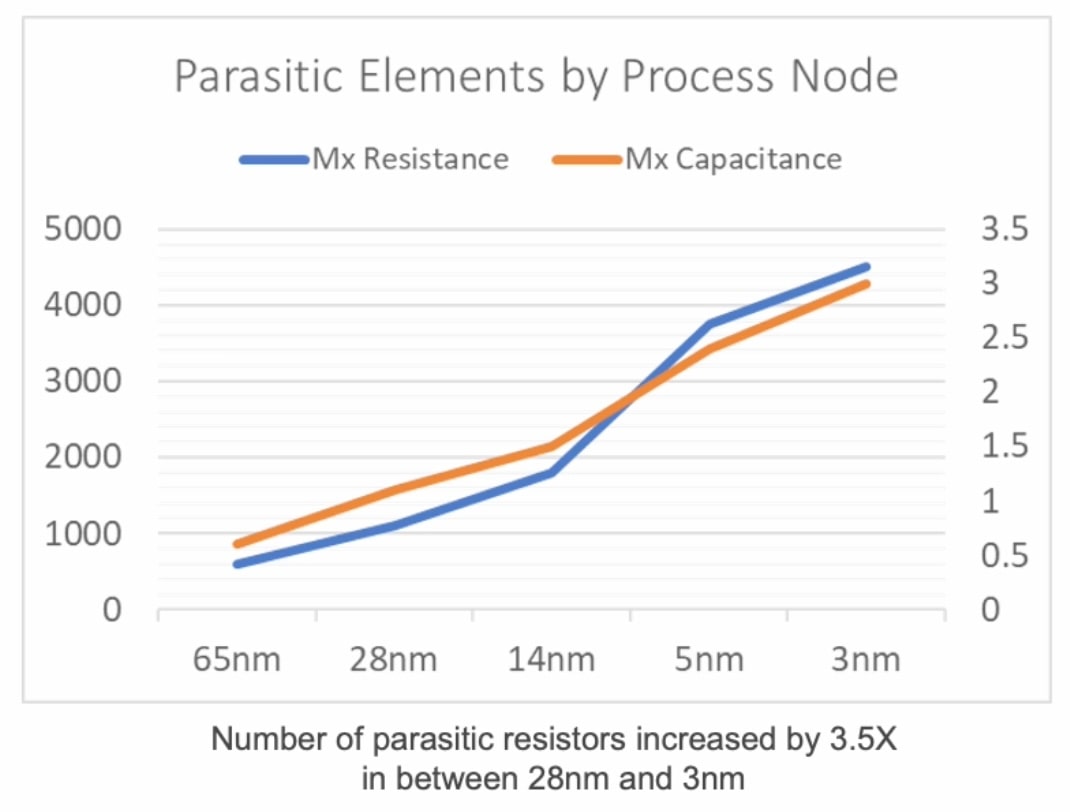 Analysis and Exploration of Parasitic EffectsWith advanced semiconductor processes continuing to shrink, the…Read More
Analysis and Exploration of Parasitic EffectsWith advanced semiconductor processes continuing to shrink, the…Read More Siemens Proposes Unified Static and Formal Verification with AIGiven my SpyGlass background I always keep an…Read More
Siemens Proposes Unified Static and Formal Verification with AIGiven my SpyGlass background I always keep an…Read MoreOne Less Reason to Delay that Venture
Many of us dream about the wonderful widget we could build that would revolutionize our homes, parking, health, gaming, factories or whatever domain gets our creative juices surging, but how many of us take it the next step? Even when you’re ready to live on your savings, prototypes can be expensive and royalties add to the pain. … Read More
Detail-Route-Centric Physical Implementation for 7nm
For many years TSMC has provided IC design implementation guidance as viewed from the process and manufacturing standpoints. The last time TSMC Reference Flow incremented, it was version 12.0 back in 2011. Since then, increased design, process and packaging related complexities of the advanced nodes have demanded more focused… Read More
Crossfire Baseline Checks for Clean IP Part II
In our previous article bearing the same title, we discussed the recommended baseline checks covering cell and pin presence, back-end, and some front-end checks related to functional equivalency. In this article, we’ll cover the extensive list of characterization checks, that include timing arcs, NLDM, CCS, ECSM/EM, and … Read More
Should Companies be Allowed to Hack Back after a Cyberattack?
Potential for Hack-Back Legislation. Government officials and experts are weighing in on the concept of ‘hacking back’, the practice of potentially allowing U.S. companies to track down cyber attackers and retaliate.
Former head of the CIA and NSA outlined his thoughts to the Fifth Domain on the Hack Back issue currently being… Read More
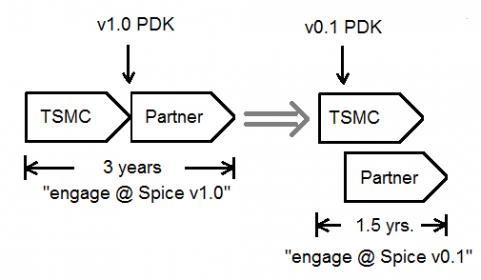
Top 10 Highlights from the TSMC Open Innovation Platform Ecosystem Forum
Each year, TSMC hosts two major events for customers – the Technology Symposium in the spring, and the Open Innovation Platform Ecosystem Forum in the fall. The Technology Symposium provides updates from TSMC on:
… Read More
Closing Coverage in HLS
Coverage is a common metric with many manifestation. During the ‘90s, both fault and test coverage were mainstream DFT (Design For Testability) terminologies used to indicate the percentage of a design being observable or tested. Its pervasive use was then spilled over into other design segments such as code coverage, formal… Read More
TSMC and Synopsys are in the Cloud!
EDA has been flirting with the cloud unsuccessfully for many years now and it really comes down to a familiar question: Who can afford to spend billions of dollars on data center security? Which is similar to the question that started the fabless transformation: Who can afford to spend billions of dollars on semiconductor manufacturing… Read More
The real race for superiority is TSMC vs Intel
Recent talk of AMD vs Intel market share share is misguided, the real race for superiority is TSMC vs Intel underlying that, tech dominance between US & China.
There has been much discussion of late about market share between Intel and AMD and how much market share AMD will gain at Intel’s expense due to Intel’s very… Read More
AVANTI: The Acquisition Game
This is the eighteenth in the series of “20 Questions with Wally Rhines”
Gerry Hsu’s departure from Cadence to form Avanti (originally named ArcSys) is chronicled in legal testimony as accusations of theft of software were followed by legal battles, financial awards and even prison terms. Mentor and Synopsys were… Read More







Musk’s new job as Samsung Fab Manager – Can he disrupt chip making? Intel outside